Hack.lu 2013 CTF Roboauth.exe Reverse Engineering Challenges Writeup
A solution guide for challenges released during a past CTF event
The last couple of days I’ve been completing in the hack.lu 2013 CTF event as part of the team 0x4e534931. This blogpost will be my writeup of the reversing challenge RoboAuth from the event which I was able to solve for the team.
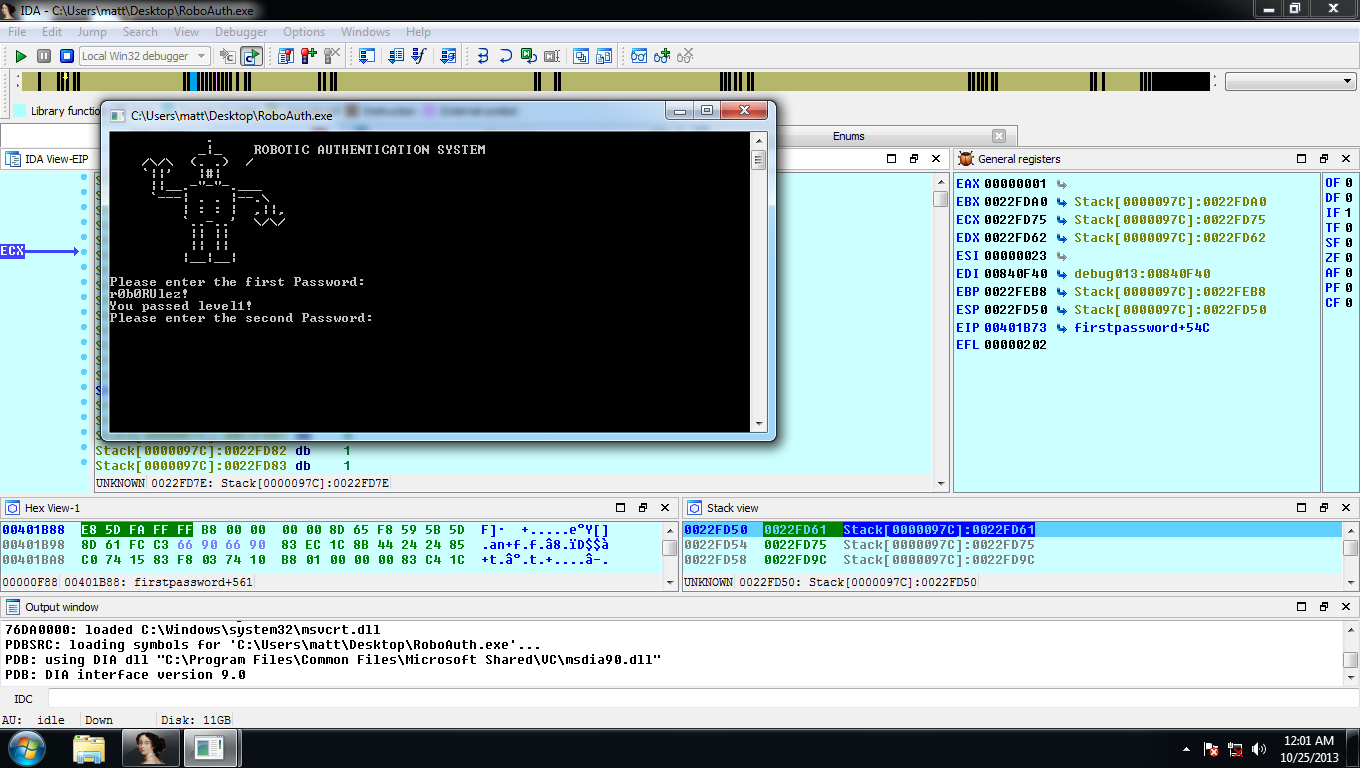
I downloaded the roboauth.exe binary from the CTF website, the flag for the challenge is [firstpassword_secondpassword]. When the binary executes it asks for two password, now time to reverse the binary to find the two passwords. Too begin with I open the binary in IDA Pro and began looking at the functions the binary calls during execution, I found an interesting function called sub_401627 which appears to be the function that asks for the first password.
Since I determined that the sub_401627 was the function which asks for and checks the first password, I renamed the function to sometime more meaningful, I placed breakpoints on the section which handles the check of the user input and executed the program.
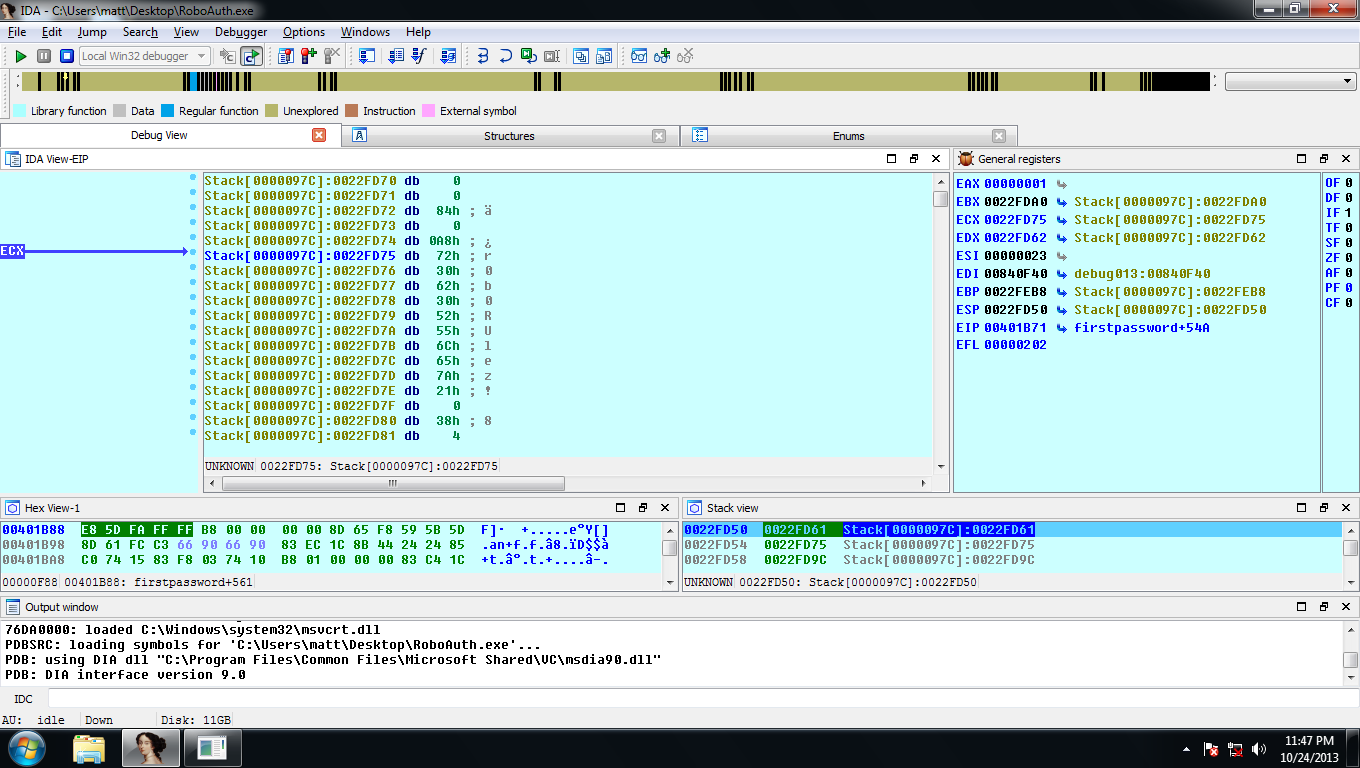
I continued executing the program after entering the first password and stopped right before a JNZ instruction which if the password was correct ZF flag is set to 0 and the jump isn’t taken, if the password incorrect the ZF flag is set to 1 and the jump is taken. Since I want the jump not be taken I need the ZF flag to be set to 0, but before taking the jump I need to find the first flag. Since the strcmp() function is called to compare the password I have entered to the correct password and than an test eax, eax instruction is executed I know I should be able to find the flag at this stage. Looking at the points the registers are pointing to I found the flag being pointed to by the ECX register.
The first password I found to be “r0b0RUlez!” I then verified that this password was correct by opening another instance of the binary and entering the password.

Now that I’ve identified the first password I need to find the second password, so continuing on from where I left off from in IDA I placed breakpoints on the instructions right after the JNZ instruction and than changed the value of the ZF flag to not take the jump. In the next section of the code prints “You have passed level1!” if the password was correct and then calls the function sub_4015ea. I looked at the function which basically runs through a set of instructions which IDA analysis to be a trap for debugger and then returns back to the sub_401627 function.
Once the trap to debugger code has been stepped through the code returns back to the debugger and continues on to another function called sub_40157F which accepts the next password, once the password as been entered the binary calls another function called sub_401547 which XOR’s the real second password and then compares the password entered by the user to the real password character by character. As soon as the characters don’t match the program closes, if the characters match a loop is taken and compares the next character, the loop continues until all the characters of the real password is check.
This process is shown in following instructions taken from the sub_401547 function.
mov eax, [ebp+arg_0]
movzx edx, byte ptr [eax]
mov eax, [ebp+arg_4]
movzx eax, byte ptr [eax]
xor eax, 2
cmp dl, al
jz short loc_401566
The input of the second password from the user is stored in the edx and the real password is stored in the eax register, the xor instruction decrypts the value stored in the eax register which is where the real password and then compares the value from the dl register and the al register together. So since this is the real password all I did was restart the IDA debugging process and entered in a string of 10 a’s and just check taking the jump until there was no more values to compare in the al register, at each time I recorded the value in the EAX register and found the values to be the following 0x77336c6c64306e65 which when I decoded from hexadecimal to ascii I found the string to be “w3lld0ne“. I tried this second password in combination with the first password and saw briefly before the program closes the congratulation message.
I then went to the challenge and submitted the flag “r0b0RUlez!_w3lld0ne” successfully completing the challenge.