CSAW CTF Qual 2014 csaw2013reversing2.exe Writeup
A solution guide for the csaw2013reversing2.exe challenge released during the 2014 CSAW Qualification CTF
This post I will be covering my solution I used for the csaw2013reversing2.exe binary which was the binary for Reverse Engineering 200 challenge. Along with the name of the binary, the challenge had a decision which was “We got a little lazy so we just tweaked an old one a bit”.
When the binary is ran a message box is open containing a string of unreadable characters. Next step was to open the PE binary in IDA to get a better understanding of binary execution flow and a possible solution for the challenge.
NOTE: For due diligence I ran the commands “file” and “strings” on the file, in case strings could pick-up the flag or anything else unexpected.
file csaw2013reversing2.exe
csaw2013reversing2.exe: PE32 executable (console) Intel 80386, for MS Windows
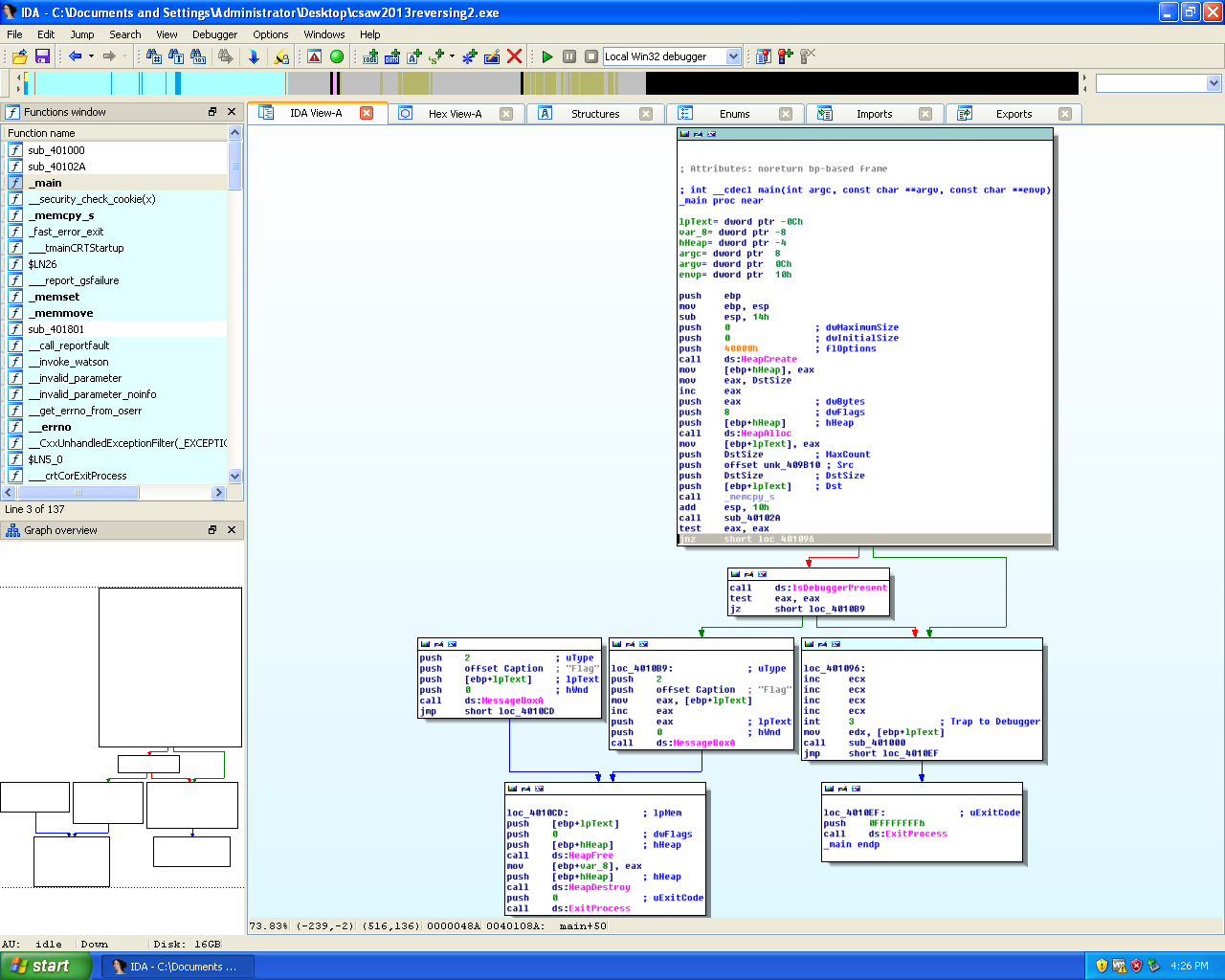
Screenshot of the main function in IDA.
Looking at the main function, the program comes to a branch in execution with the decision being determined by a JNZ (Jump Not Zero) instruction which will jump of the Z flag is not set to “0”. So I need to force the to “loc_401096”, in this section of program there is a call to a subroutine “sub_40100”, once the program returns from this function the program exits. This means I need to look at the “sub_401000” subroutine.
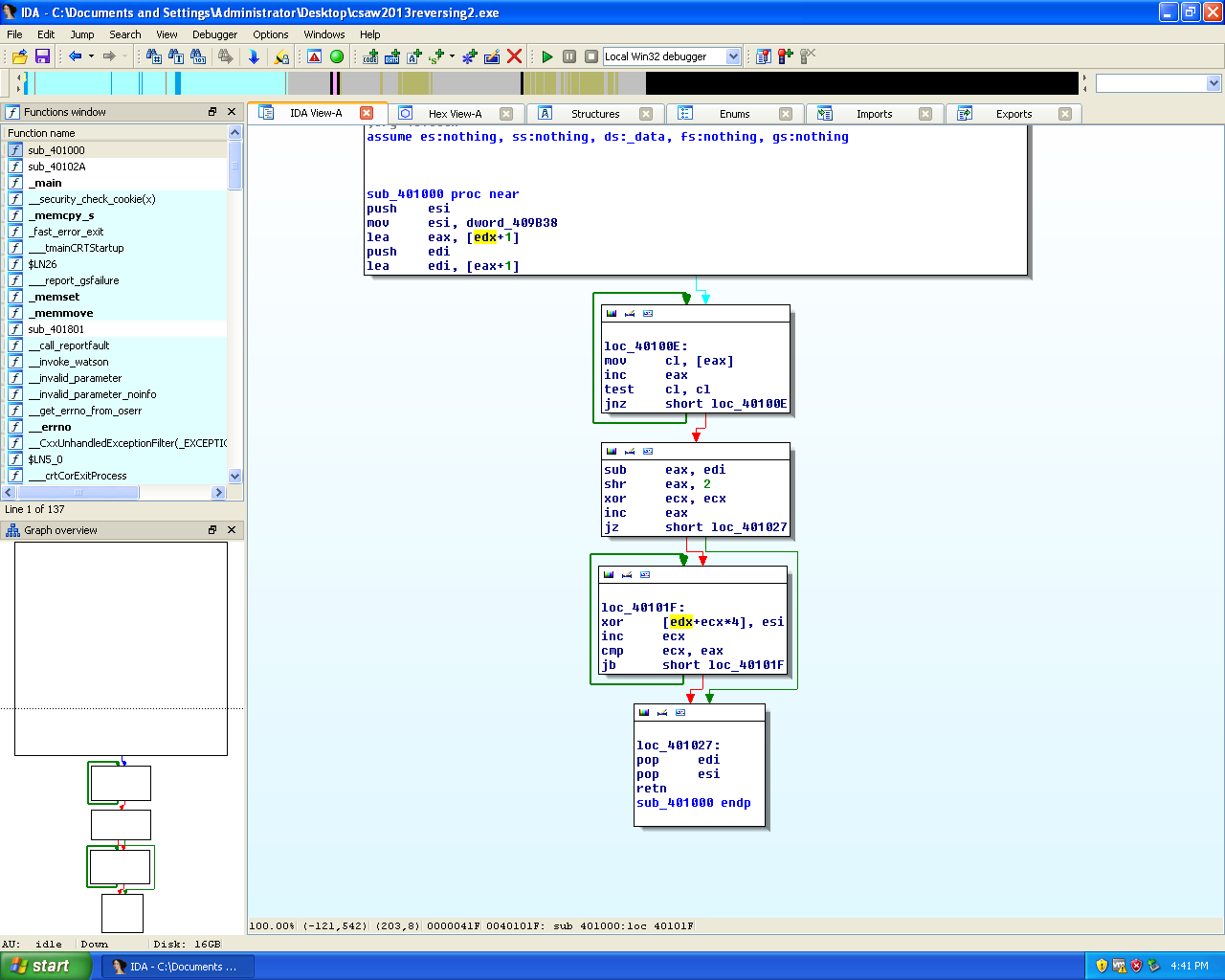
Screenshot of the sub_401000 function in IDA.
We can see this function contains 2 loops and a branch in execution and then returns back to the main function. The last loops seems to be decrypting loop, which means I needed to direct the execution to this point.
So I placed a breakpoint in the following locations:
- On the “jnz short loc_401096” instruction in the main function.
- On the “jmp short loc_4010E” instruction after the “call sub_401000” instruction in the main function.
- On the “jz short loc_40102” instruction in the “sub_401000” function.
- On the “pop edi” instruction in the “sub_401000” function.
These points allow me to control the flow of execution and inspect the registers for the value after the loops in the “sub_401000” function.

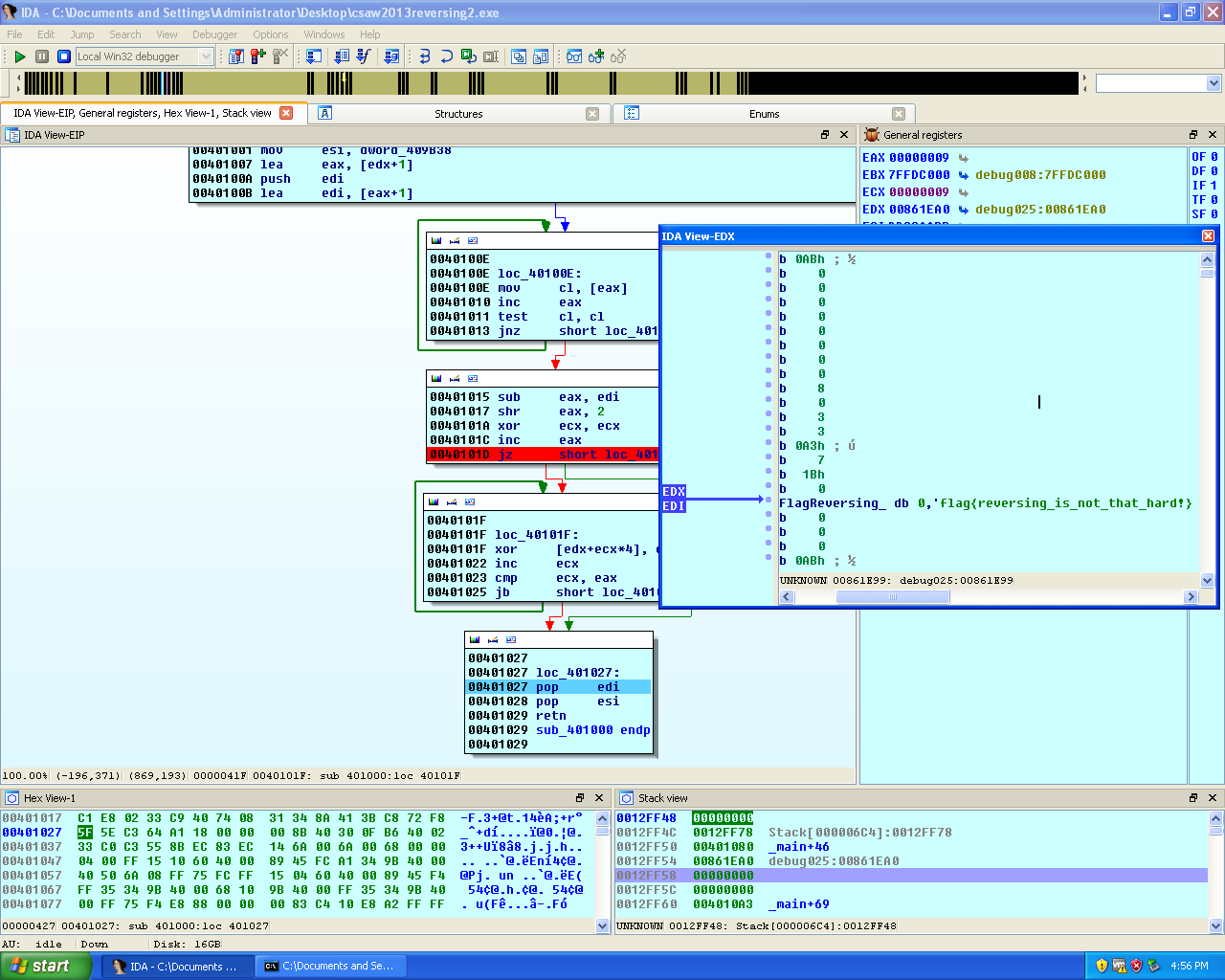
The flag was successfully decrypted and found.
After the loop was successfully passed, I inspected the EDX register which contained the flag for this challenge.
flag{reversing_is_not_that_hard!}