Home
Over 10 years of penetration testing, red team and purple teaming experience in my current role as a principal security consultant at a Cyber Security Firm. My current role includes operating as a service offering lead for the purple teaming, and restricted environment breakout testing (and the wireless penetration testing previously) service offerings.
Featured Posts
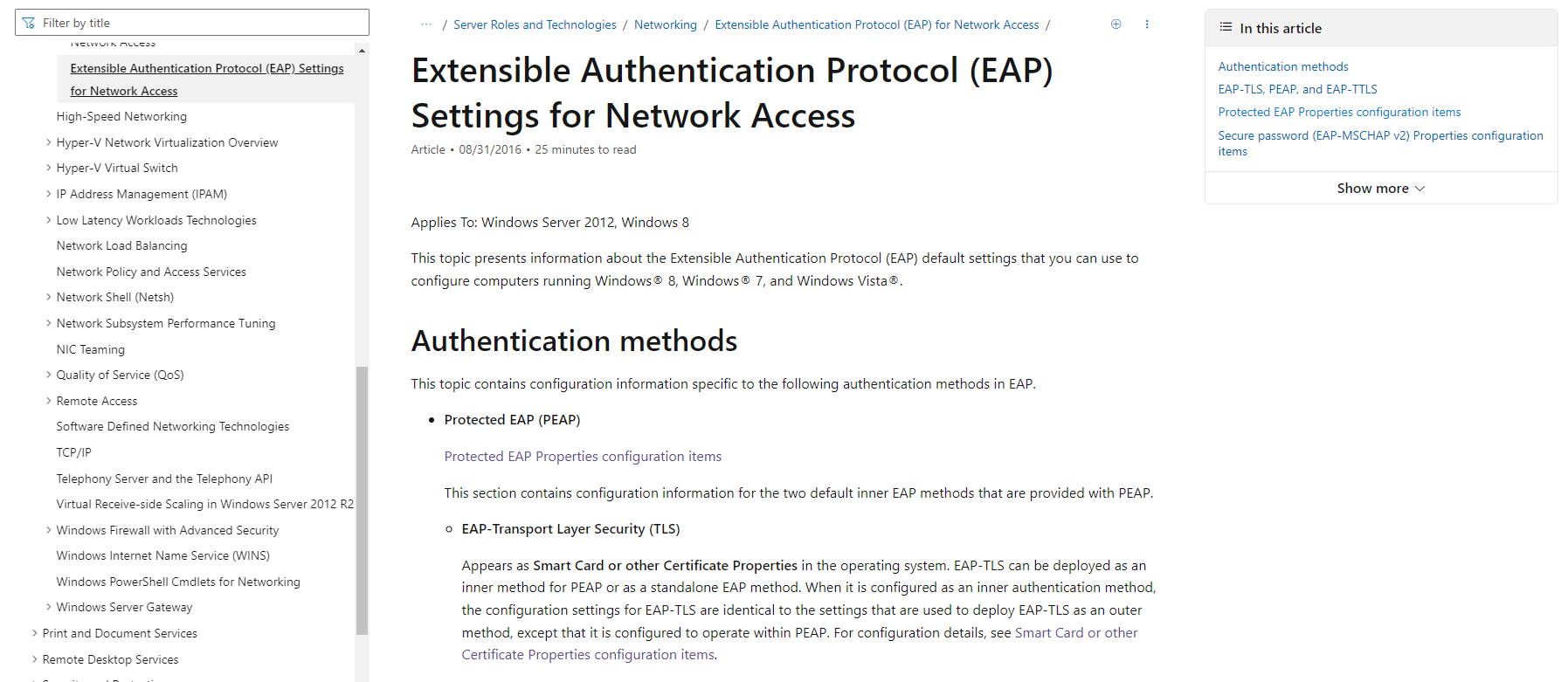
An adversarial perspective of the Windows supplicant settings
Understanding the various Windows supplicant settings and their security implications Continue reading An adversarial perspective of the Windows supplicant settings
Latest Posts
Demonstrating Threat Actor Thought Process For Known Password Cracking
Using hashcat to build target specific wordlists Continue reading Demonstrating Threat Actor Thought Process For Known Password Cracking
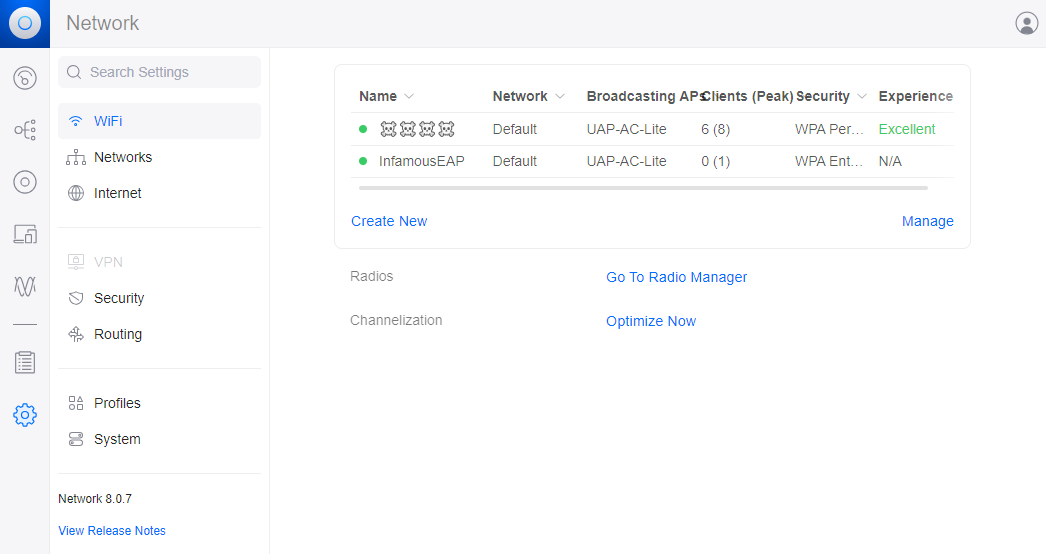
Building a WPA2 Enterprise WLAN with a Ubiquiti UniFi Controller and a Microsoft Network Policy Server
An end-to-end guide to building a Ubiquiti WPA2 Enterprise with Microsoft RADIUS WLANs Continue reading Building a WPA2 Enterprise WLAN with a Ubiquiti UniFi Controller and a Microsoft Network Policy Server

An adversarial perspective of the Windows supplicant settings
Understanding the various Windows supplicant settings and their security implications Continue reading An adversarial perspective of the Windows supplicant settings
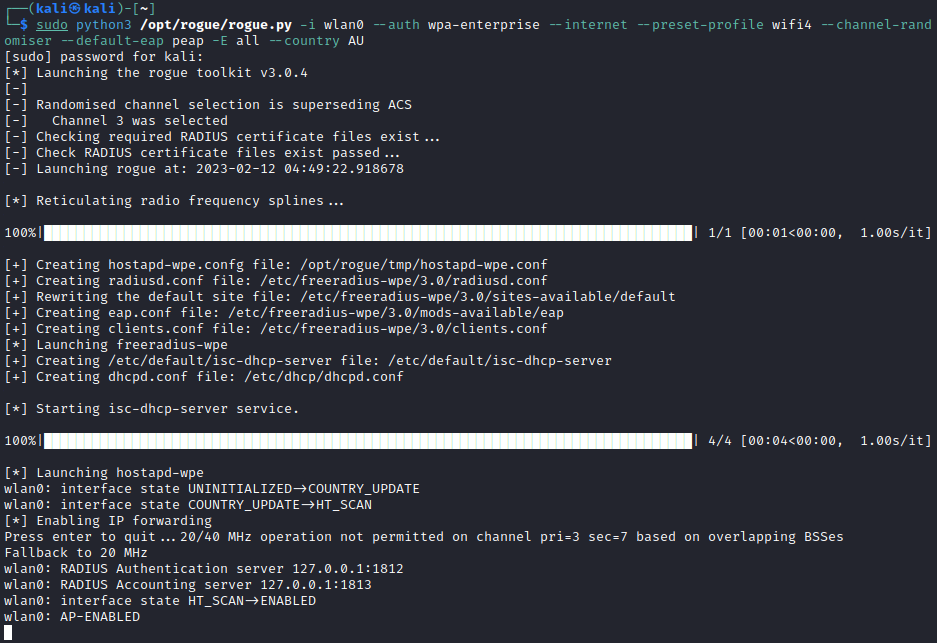
Cracking WPA2-EAP WLAN perimeters with Evil Twin attacks
Coercing domain credentials from a device using evil twin attacks Continue reading Cracking WPA2-EAP WLAN perimeters with Evil Twin attacks
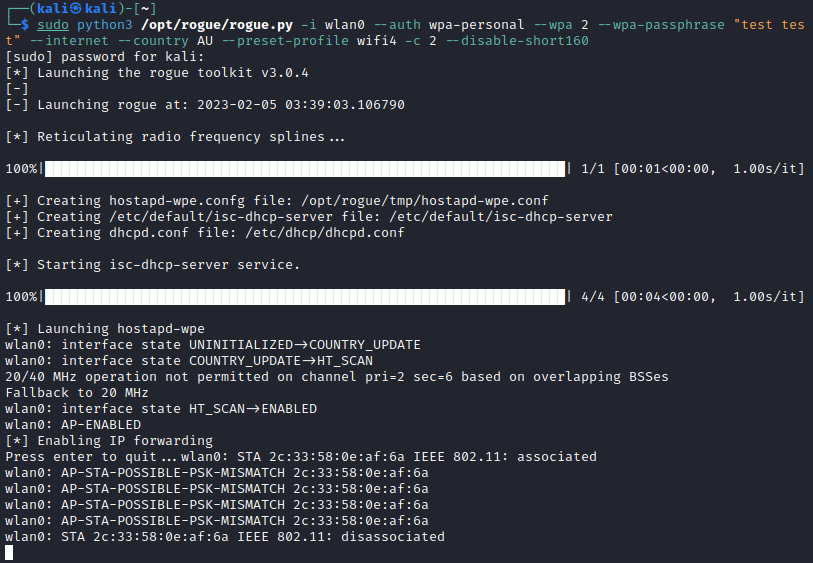
Cracking PSK WLAN perimeters with Evil Twin attacks
Coercing the PSK from a device without deauthentication attacks Continue reading Cracking PSK WLAN perimeters with Evil Twin attacks
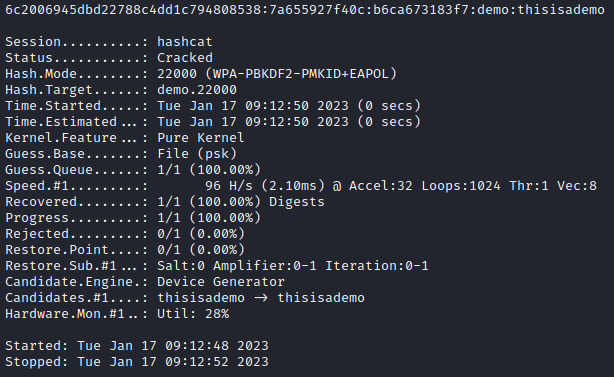
Cracking WEP & WPA2-PSK Wireless Encryption Redux
A 2023 guide on cracking WEP & WPA2-PSK wireless encryption Continue reading Cracking WEP & WPA2-PSK Wireless Encryption Redux
See Posts for more